Cryptocurrency scams are unfortunately becoming more and more common as digital currencies gain popularity. One such scam that has recently emerged is the “Tesla X Wallet”, which lures victims with promises of free Bitcoin and other cryptocurrencies.
Overview of the Scam
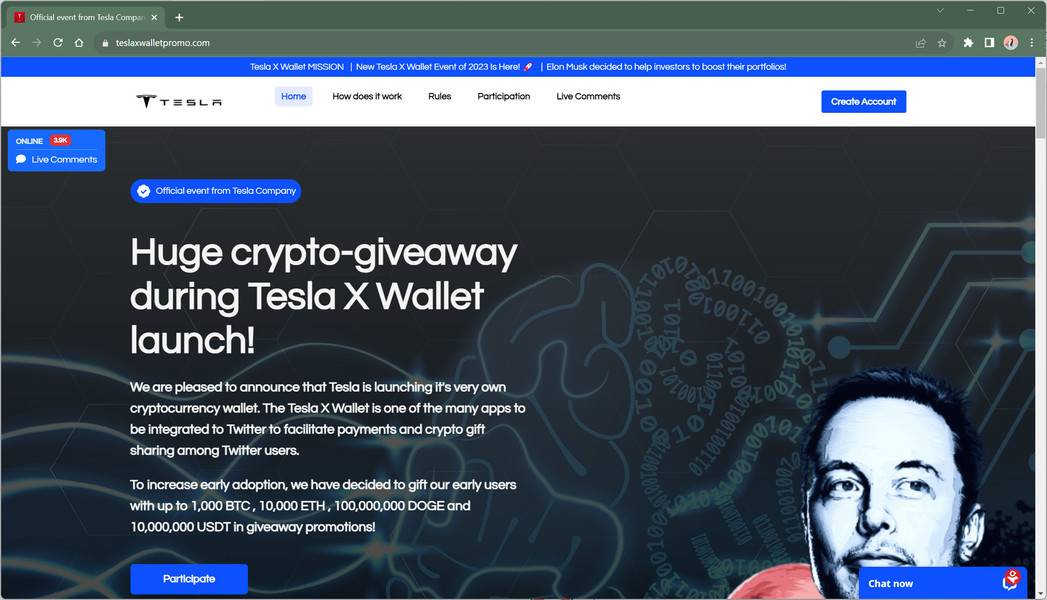
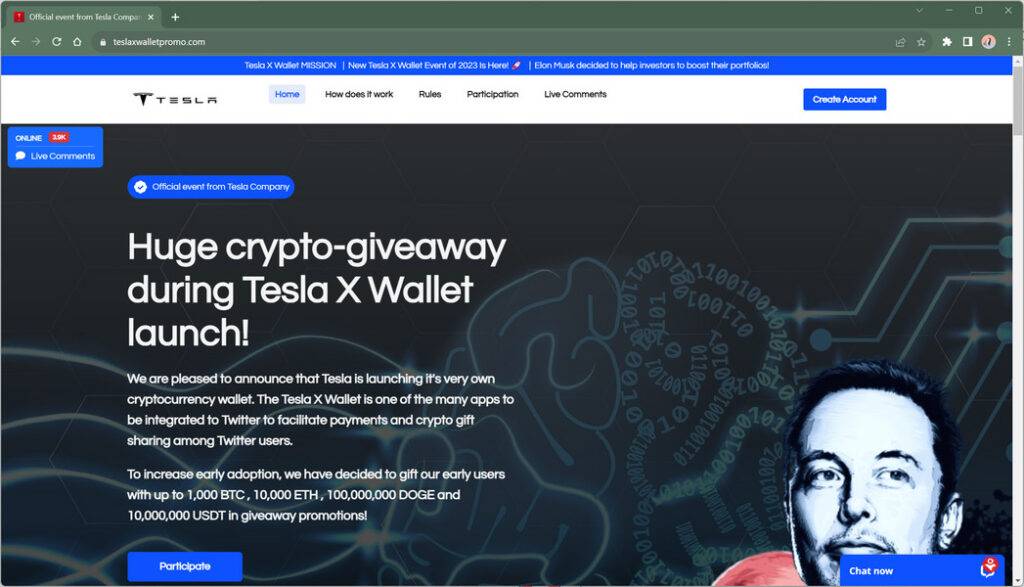
The Tesla X Wallet Promo scam claims to be giving away free cryptocurrency to celebrate the launch of Tesla’s new crypto wallet app. Scam websites like teslaxwalletpromo.com promote the fake offer using Elon Musk’s name and image without his permission.
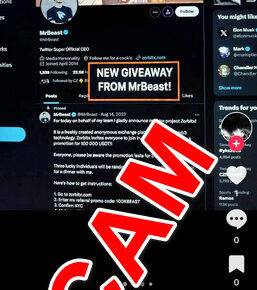
The scam is promoted via fake ads and images on social media sites like Facebook, Instagram, and TikTok. The ads show fake tweets from Elon Musk announcing the giveaway.
If victims visit the scam website, they are greeted with promises of earning up to 1,000 BTC, 10,000 ETH, 100,000,000 DOGE, and 10,000,000 USDT completely free. All they need to do is make a small deposit into a wallet to participate.
Of course, this is just a ploy to steal cryptocurrency deposits from victims. There is no Tesla crypto wallet, and no free giveaway. Any funds sent will be stolen by the scammers.
How the Tesla X Wallet Promo Scam Works
The scam works by taking advantage of people’s desire to earn easy money. The promise of free cryptocurrency is enticing, especially when promoted using Elon Musk’s name.
Here are the steps the scam typically follows:
- Fake social media ads – The scam begins with fake images and ads posted on social media promoting the crypto giveaway. The ads include Elon Musk’s name and photo to appear legitimate.
- Scam website – The ads lead to a website like teslaxwalletpromo.com which has all the details of the fake crypto giveaway. The site uses more fake Elon Musk tweets and fake comments to build credibility.
- Make a deposit – Visitors are instructed to make a small crypto deposit into a provided wallet address to participate in the giveaway. They are promised to receive double their deposit amount in return.
- Send funds – Enticed by the promise of free money, victims send cryptocurrency to the wallet address.
- Disappear – Once the scammers receive the deposits, they cut off all contact and disappear with the stolen funds.
The scam relies on people seeing the ads on social media, visiting the scam site, and falling for the promises of free cryptocurrency. It costs nothing for the scammers to set up, but can earn them thousands from unsuspecting victims.
What to Do If You Are a Victim
If you have fallen victim to the Tesla X Wallet scam and sent cryptocurrency to the scammers, here are some steps you can take:
- Report the scam – Report the scam ads, website, and wallet addresses to the relevant social media platforms, hosting providers, cryptocurrency exchanges, and authorities. This helps get them shut down faster.
- Inform your contacts – Let your friends and followers know that you, unfortunately, fell for a scam. This helps prevent the scam from spreading further.
- Don’t send more funds – Under no circumstances should you send the scammers more money for any reason. Common tactics include telling victims to pay “fees” or “taxes” to release their winnings.
- Check with your wallet provider – For large amounts, check if your wallet provider can help reverse or cancel the transactions. This only works in some cases when caught early.
- Consult professionals – Speak to professionals like lawyers and cybersecurity experts for guidance. They may be able to suggest further courses of action.
- Learn from the experience – Scams can happen to anyone. Try not to be too hard on yourself. Learn how to spot and avoid scams to stay safer in the future.
- Run an antivirus scan – If you suspect your device is infected with malware, you should run a scan with Malwarebytes Anti-Malware.
How to Avoid Falling Victim
Here are some tips to avoid falling prey to crypto scams like the Tesla X Wallet Promo:
- Be wary of “free crypto” offers – If it sounds too good to be true, it usually is. No one is going to give you free money or cryptocurrency.
- Verify legitimacy – Check the credentials of any website and offer very carefully before taking any action. Search for reviews and complaints to uncover scams.
- Watch for fake endorsements – Scammers often use celebrities like Elon Musk without their consent. Verify endorsement claims directly with the source.
- Check account details – Accounts spreading scam offers often have red flags like being recently created, having no followers, or using stolen images.
- Beware of fake sites – Scam websites tend to have new domains, use odd URLs, have spelling errors, and look generally unprofessional.
- Never send funds in advance – Never send cryptocurrency to an account to “verify” it, “unlock” bonuses, or for giveaways. You should only send crypto for legitimate purchases.
- Use crypto securely – Follow best practices like enabling 2FA and using hardware wallets to keep your funds more secure.
- Stay up to date – Keep up with the latest crypto scams and threats so you can identify and avoid them more easily.
Frequently Asked Questions
Here are some common questions about the Tesla X Wallet scam:
Is the Tesla X Wallet real?
No, there is no such thing as the Tesla X Wallet. It is completely fake. Tesla has not announced any plans to release a cryptocurrency wallet.
Can I really get free Bitcoin and crypto from this?
No, the offers of free cryptocurrency are completely fake. No one will give you free money, especially not in the amounts promised. Any crypto sent is likely to be stolen.
Why are they using Elon Musk’s name and image?
The scammers are illegally using Elon Musk’s name and likeness without his permission. This is done to make the offer appear legitimate and trustworthy. Elon Musk has no actual involvement.
I sent crypto to the wallet address given. Can I get it back?
Unfortunately, any cryptocurrency sent to scammers is likely gone for good. You can try reporting them in hopes of shutting them down but recovering the funds is very rare.
I was told to send more crypto to “unlock” my bonus. Should I?
Absolutely not. This is just another tactic scammers use to steal even more money from victims. Never send additional payments for any reason in a scam situation.
Can I report the scam to get my money back?
You should definitely report the scam in hopes of getting the fraudulent accounts and websites shut down. However, recovering lost money is very unlikely. Cryptocurrency transactions are generally irreversible.
How can I avoid falling for such scams in the future?
Be wary of “too good to be true” offers, verify legitimacy carefully, look for red flags, never send crypto in advance, and keep learning about the latest crypto scams and threats. Taking precautions helps avoid becoming a victim.
The Bottom Line
The Tesla X Wallet promo scam is a prime example of the cryptocurrency giveaway fraud happening today. By enticing victims with fake offers of free crypto using celebrity names, they can steal significant sums from unsuspecting people.
The best way to avoid these scams is to be aware of common red flags, verify every offer carefully, and never send payments in advance. With crypto scams on the rise globally, it pays to be extra vigilant to help protect yourself and your funds.