cWhen you open the Task Manager on your Windows computer, you may notice a process called “Windows Image Acquisition” running in the background. This process, also known as WIA, is an essential component of the Windows operating system that plays a crucial role in image acquisition and scanning. In this article, we will explore why the Windows Image Acquisition process is running in Task Manager and its significance in the overall functioning of your computer.

What is the Windows Image Acquisition Process?
The Windows Image Acquisition process, or WIA, is a service that allows applications to communicate with image acquisition devices such as scanners, digital cameras, and webcams. It provides a standardized interface for acquiring images and transferring them to the computer for further processing or storage.
WIA is responsible for managing the communication between the hardware device and the software application. It handles tasks such as initializing the device, controlling its functions, and retrieving the acquired images. Without WIA, applications would need to implement device-specific drivers and protocols, making it much more challenging to support a wide range of image acquisition devices.
Why is the Windows Image Acquisition Process Running in Task Manager?
The presence of the Windows Image Acquisition process in Task Manager indicates that there is an active application or service on your computer that is utilizing image acquisition functionality. It could be a scanning software, a webcam application, or any other program that requires access to image acquisition devices.
When you launch an application that needs to interact with an image acquisition device, the application will start the WIA service to establish communication. The WIA process will then run in the background, ensuring that the device is properly initialized and ready for image acquisition.
It’s worth noting that the Windows Image Acquisition process is not always running. It only starts when an application requires its services and terminates once the application no longer needs access to the image acquisition device. So, if you see the WIA process running in Task Manager, it indicates that an application is actively using an image acquisition device.
Common Applications that Use the Windows Image Acquisition Process
Several popular applications rely on the Windows Image Acquisition process to interact with image acquisition devices. Here are some examples:
- Scanning software: Applications like Adobe Acrobat, Microsoft Office Document Imaging, and various scanning utilities utilize WIA to communicate with scanners and create digital copies of physical documents.
- Webcam software: Video conferencing applications, such as Skype and Zoom, use WIA to access webcams and enable video communication.
- Image editing software: Programs like Adobe Photoshop and GIMP utilize WIA to import images directly from scanners or digital cameras for editing purposes.
Should You Be Concerned About the Windows Image Acquisition Process?
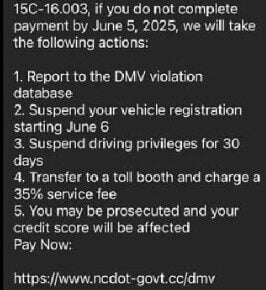
The Windows Image Acquisition process is a legitimate component of the Windows operating system and is not inherently harmful. However, like any other system process, it is essential to ensure that it is not being exploited by malware or malicious software.
If you notice unusual behavior or suspect that your computer may be infected with malware, it is recommended to perform a thorough scan using reliable antivirus software. One such trusted solution is Malwarebytes Free, which can detect and remove various types of malware.
Regularly updating your operating system and keeping your security software up to date can also help protect your computer from potential threats.
Conclusion
The Windows Image Acquisition process, or WIA, is an integral part of the Windows operating system that enables applications to communicate with image acquisition devices. It ensures smooth and standardized interaction between software and hardware, making it easier for developers to support a wide range of image acquisition devices.
If you see the Windows Image Acquisition process running in Task Manager, it indicates that an application on your computer is actively using an image acquisition device. This could be a scanning software, webcam application, or any other program that requires access to image acquisition functionality.
While the Windows Image Acquisition process is not inherently harmful, it is crucial to stay vigilant and ensure that it is not being exploited by malware. Regularly scanning your computer with reliable antivirus software, such as Malwarebytes Free, can help detect and remove any potential threats.
By understanding the role of the Windows Image Acquisition process and taking necessary security measures, you can ensure the smooth functioning of your computer and protect it from potential risks.

![Remove Dsg-protect.co.in Pop-up Ads [Virus Removal Guide] 5 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)