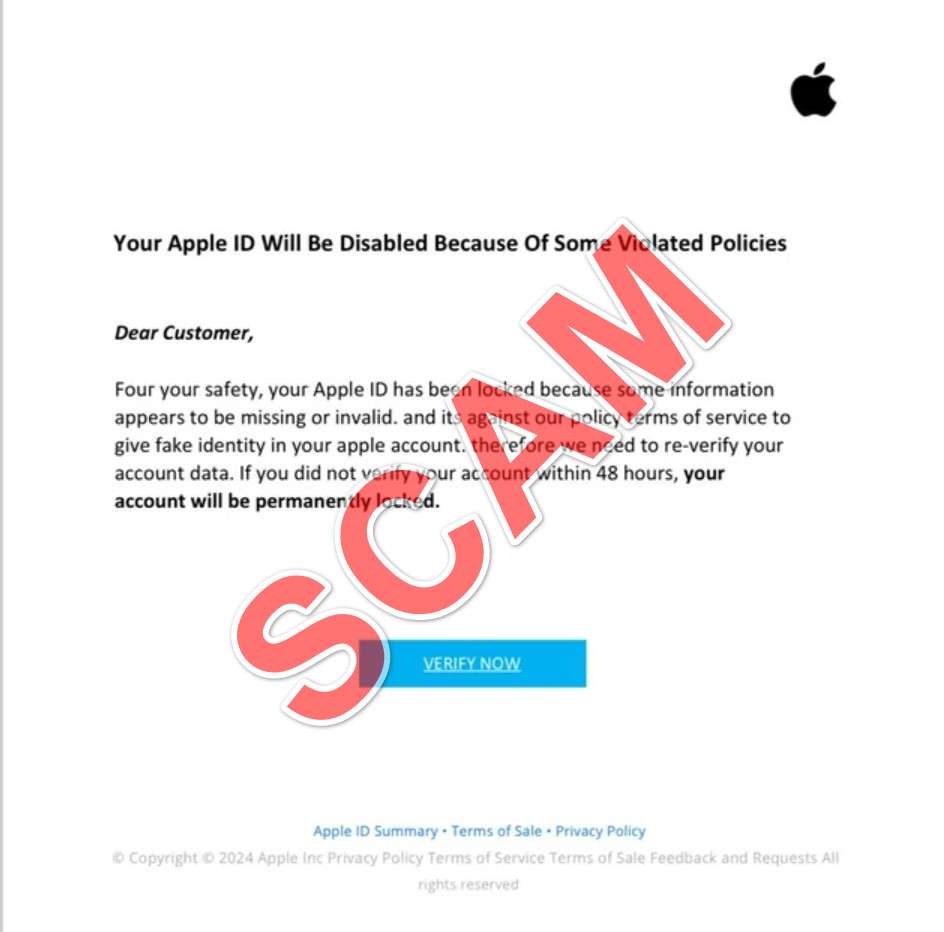
You may have recently received an email that appears to be from Apple, warning you that “Your Apple ID Will Be Disabled Because Of Some Violated Policies!”. The email goes on to state that for your safety, your Apple ID has been locked because some information appears to be missing or invalid, and this is against Apple’s terms of service.
The email urges you to “verify your account” within 48 hours to avoid having your account permanently locked. It includes an eye-catching “Verify Now” button that promises to take you to the Apple verification page.
This is a scam designed to steal your Apple ID login credentials.
While the email appears convincing with Apple branding and logos, it was not sent by Apple. It is a phishing scam aimed at tricking users into inputting their Apple ID username and password on a fake website controlled by scammers.
This article will provide an in-depth look at how this Apple disable scam works, how to spot fake Apple emails, what to do if you fell victim, and key tips to avoid getting fooled by this and other Apple phishing scams.
Overview of the Apple ID Disable Scam
The “Your Apple ID Will Be Disabled Because Of Some Violated Policies!” phishing scam is one of the more common and convincing Apple-themed phishing scams circulating via email. Since 2020, Apple users worldwide have reported receiving this scam which threatens to disable your Apple ID within 48 hours unless you verify your account immediately.
The scam email is carefully crafted to trick users into believing their Apple account is at imminent risk of being locked. Scammers accomplish this by using legitimate Apple branding and logos, posing as Apple support addresses, and claiming your account will be permanently disabled within 48 hours for violating Apple policies.
The email urges you to act fast by clicking a Verify Now button, which leads unwitting victims to a fake Apple login page operated by the scammers. If users enter their Apple ID email address and password on this phishing site, the scammers capture their credentials and can access the victim’s real Apple account.
From there, scammers may change account passwords to lock out the owner, access private data, make fraudulent purchases with stored payment methods, steal personal information for identity theft, and deploy additional scams while posing as Apple support.
The phishing email instills fear and urgency in recipients by warning their access will be cut off permanently within two days, pressuring them to provide their credentials without proper scrutiny of what is really a well-crafted scam.
Some examples of specific subject lines used in the phishing email include:
- Urgent: Your Apple ID Has Been Locked Due to Invalid Login Attempts
- Action Required Immediately To Avoid Disabling Apple ID
- Account Verification Required or Apple ID Will Be Disabled
- Critical Alert: Apple ID Locked for Violating Usage Policies
No matter the specifics of the subject line used, the email body itself reiterates the short 48 hour deadline before permanent disabling and provides little other detail about the supposed policy violations.
A bright red Verify Now button prominently positioned in the email body is the key action scammers want victims to take. They don’t want recipients reading the fine print or scrutinizing the scam email closely. The Verify Now button seems like the fastest path to rectifying the supposed problems with your Apple account, but in reality rapidly delivers your credentials directly to scammers.
The 48 hour countdown tactic creates urgency and pressure that inhibits users from discerning the fraudulent nature of the phishing attempt. But Apple does not actually disable accounts so rapidly without extensive prior notifications. This urgent 48 hour warning is a tactic exclusive to scammers rushing victims into providing their Apple IDs and passwords through deception.
The phishing landing page that victims are sent to after clicking Verify Now is designed to closely mimic Apple’s real account login site. Scammers use Apple graphics, logos, web addresses and branding so the site convincingly appears legitimate at first or even second glance.
Without careful scrutiny of the full web address in the browser bar, victims may be fooled into entering their confidential Apple credentials. The credentials are captured instantly by the scammers who can then access and takeover the victim’s real Apple account.
This scam illustrates the importance of always carefully analyzing any communication that claims to be from Apple and requests account verification or login information. Urgency, fear of account deactivation, and legitimate-looking branding are the hallmarks of Apple phishing scams aimed at deceiving users into giving up their account access.
With so many Apple users worldwide, scammers have realized impersonating Apple technical and security teams allows them to deploy sophisticated, large-scale phishing campaigns that convince many victims their accounts are threatened.
But awareness of the scam tactics and learning to identify subtle red flags in language and design can help Apple users avoid compromising the security of their accounts when these fraudulent emails land in their inbox. Scrutinizing the sender, avoiding urgency pressure, and verifying site authenticity before acting are key to protecting your Apple ID from phishing scams.
How the Apple Disable Scam Works
The scammers behind this scam put a lot of effort into making the phishing email appear legitimate. However, a closer look reveals signs that expose it as a scam. Here is a step-by-step look at how the Apple ID scam unfolds:
1. You Receive an Apple Phishing Email
The scam starts with an email being delivered to your inbox. The sender disguises themselves as an official Apple email address, often using something like “support@apple.com” or “security@appleid.apple.com.”
The email has Apple branding and logos, making it appear like legitimate correspondence from Apple. The subject line is designed to get your attention, usually stating something like “Your Apple ID has been locked!” or “Action Required Immediately To Avoid Disabling Apple ID.”
The email body reiterates that your Apple ID is at risk of being disabled within 48 hours for violating Apple policies. It provides little detail beyond this urgent warning.
2. Urged to Verify Account Within 48 Hours
The email stresses that you only have 48 hours to verify your account before it will be permanently locked by Apple. This creates a false sense of urgency to act quickly before time runs out.
A bright red “Verify Now” button is prominently displayed, promising it will take you to Apple’s verification site to confirm your account. In reality, it sends you to the scammer’s fake Apple site.
The 48 hour countdown is completely fabricated. Apple does not give warnings with such short deadlines before disabling accounts. This tactic pressures victims to click Verify Now before scrutinizing the email further.
3. Fake Apple Site Requests Apple ID and Password
When you click the Verify Now button, you are taken to a fake Apple account login page that is carefully designed to look like the real thing.
The site has Apple branding, logos, graphics, and web address to appear legitimate. The scammers often register lookalike domains like “appleverify.com” to mislead users.
Once at the fake login page, you are prompted to enter your Apple ID email/username and password to “verify your account.” If entered, this sensitive information is captured by the scammers running the site.
4. Scammers Access Real Apple Account
With your actual Apple ID and password in hand, the scammers will login to your real Apple account using the credentials you provided.
This gives them access to your personal information, stored payment methods, iCloud data, photos, contacts, and anything else connected to your Apple ID.
The scammers may disable your access to lock you out of your own Apple account. They could also use your account details for identity theft and financial fraud.
5. Account Takeover Damages and Risks
Once scammers takeover your Apple ID account, your personal data is exposed and there are financial risks. Identity theft with your info is possible.
They may lock you out by changing account passwords and enabling two-factor authentication with their own trusted devices.
Stolen payment info on your Apple ID could be used to make unauthorized purchases of apps, music, iCloud storage and more.
Recovering a compromised Apple ID often requires an arduous account recovery process with Apple support. Valuable personal data may be lost.
This highlights why it is critical not to fall for the Verify Now button and hand over your Apple login credentials to scammers.
What to Do If You Fell For the Apple Disable Scam
If you submitted your Apple ID email and password through the fake Apple site, don’t panic. Here are important steps to take right away:
1. Change Your Apple ID Password
Immediately go to Apple’s real website and change your Apple ID password. Pick a new, strong password that the scammers do not have. Enable two-factor authentication for added security.
2. Remove Saved Payment Methods
Check your Apple account for any stored payment methods like credit cards. Remove anything saved on file to prevent unauthorized purchases.
3. Contact Apple Support
Notify Apple Support that your account was compromised so they can secure it and assess any damage. Be ready to prove account ownership to regain access.
4. Monitor Accounts Closely
Carefully monitor your Apple account as well as connected accounts like email, social media and financial accounts. Look for any unauthorized access or activity.
5. Run Anti-Virus Scans
If you entered Apple ID details on a device, scan it for viruses/malware in case scammers planted anything during account takeover.
6. Beware of Any Follow Up Scams
Scammers may deploy follow up phishing attempts posing as Apple tech support offering to “help secure your account.” Ignore these continued scam attempts.
Avoiding Apple Phishing Scams
Here are key tips to avoid falling victim to the “Your Apple ID Will Be Disabled” scam and other Apple phishing scams:
Closely Scrutinize Apple Emails
If an Apple email seems suspicious, take time to slowly and thoroughly review it before acting. Verify the sender address matches @apple.com.
Look for typos, grammatical errors, threatening urgent warnings, or requests for immediate account verification, as these are red flags of scams.
Never Call Numbers Provided
Some Apple phishing emails include phone numbers for you to call for account assistance. Never call these numbers, as they connect you to scammers posing as Apple support to steal your credentials.
Avoid Clicking Links in Emails
Do not click Verify Now or other links inside Apple emails. Instead, manually navigate to the Apple website by typing it directly into your browser if you want to check account status.
Check URL of Sites You Land On
If redirected to an Apple login page after clicking a link, check that the URL matches Apple’s real website and not a lookalike. Search for the site on Safe Browsing Lookup before entering info.
Use Strong, Unique Passwords
Always use strong, randomized passwords for your Apple ID and other important accounts. Never reuse the same password across multiple sites.
Enable two-factor authentication on your Apple ID for enhanced security against phishing.
Keep Software Up to Date
Maintain up-to-date antivirus software and keep apps, browsers and operating systems patched with the latest security updates. This prevents scammers from exploiting vulnerabilities.
Frequently Asked Questions About the Apple ID Disable Scam
1. What is the Apple ID disable scam?
The Apple ID disable scam is a phishing scam where scammers send fake emails pretending to be from Apple, warning victims that their Apple ID will be disabled within 48 hours unless they verify their account immediately. The emails include a “Verify Now” button that sends victims to a fake Apple login page to steal their credentials.
2. How do I recognize a fake Apple ID disable email?
Fake Apple emails have several red flags:
- Unknown sender address instead of @apple.com
- Threatening urgent warnings about disabling your account
- Countdown timer of 48 hours before alleged deactivation
- Requests for personal information like Apple IDs/passwords
- “Verify Now” buttons leading to fake Apple login pages
3. What happens if I click the Verify Now button?
The Verify Now button sends you to a fake Apple login page operated by scammers. If you enter your Apple ID and password, the scammers capture your credentials and gain access to your account.
4. How do scammers use my Apple ID credentials?
Scammers can use stolen Apple IDs to:
- Access and steal private data from your account
- Lock you out by changing your password
- Make unauthorized purchases with saved payment info
- Harvest personal info for identity theft
- Deploy additional phishing scams posing as Apple
5. What should I do if I gave the scammers my Apple ID info?
If you entered your info, immediately:
- Change your Apple ID password to lock out the scammers
- Remove any saved payment methods on your account
- Contact Apple Support to secure your account
- Monitor all connected accounts closely for suspicious activity
- Run anti-virus scans to check for malware
6. How can I check if an Apple login page is real or fake?
To verify an Apple login page:
- Check the URL carefully matches apple.com
- Look for the padlock icon by the URL signalling encryption
- Search for the page on safe browsing lookup sites like Google Safe Browsing
7. How can I report this Apple ID phishing scam?
To report fake Apple emails:
- Forward the email to reportphishing@apple.com
- File a complaint with the FTC at ReportFraud.ftc.gov
- Report the site to Google Safe Browsing
8. How can I avoid falling for the Apple ID disable scam?
To avoid the scam:
- Scrutinize sender addresses and urgencies in Apple emails
- Never call phone numbers provided in suspicious emails
- Manually navigate to Apple.com to check account status
- Use unique, complex passwords with two-factor authentication
- Keep software updated and run frequent anti-virus scans
9. Why do scammers pretend to be Apple?
Scammers pretend to be Apple because it’s a trusted company with millions of users. By pretending to be Apple security teams, scammers can launch convincing phishing campaigns.
10. Are other Apple users at risk of this scam?
Yes, this scam targets Apple users worldwide. Always be vigilant against phishing attempts and never give your Apple ID credentials unless you are certain the request is legitimate.
The Bottom Line
The “Your Apple ID Will Be Disabled” phishing scam aims to trick users into handing over their Apple login credentials by posing as an urgent account verification request.
But the email is not from Apple. The Verify Now button sends victims to a fake Apple site controlled by scammers to capture entered account details.
With your username and password, scammers can access and takeover your real Apple account. This can enable identity theft, payment fraud, account lockout and