In recent weeks, many residents across the Dallas-Fort Worth area have reported receiving suspicious text messages claiming to be from the North Texas Tollway Authority (NTTA). These fraudulent messages often pressure recipients to urgently pay a so-called “ZipCash bill” to avoid legal action.
This timely article provides an in-depth overview of how this text message scam works, including a close analysis of the scam texts, the fake websites they link to, and first-hand accounts from victims. With scammers constantly evolving their tactics, it’s crucial that residents stay informed to protect themselves.
Read on to learn how to detect these NTTA scam texts, avoid falling for their tricks, and report them to stop the scammers in their tracks.
Scam Overview: Anatomy of the Fraudulent NTTA Texts
The scam messages are specifically designed to mimic legitimate communication from the North Texas Tollway Authority. This is done to deceive recipients into believing the texts come from an official source.
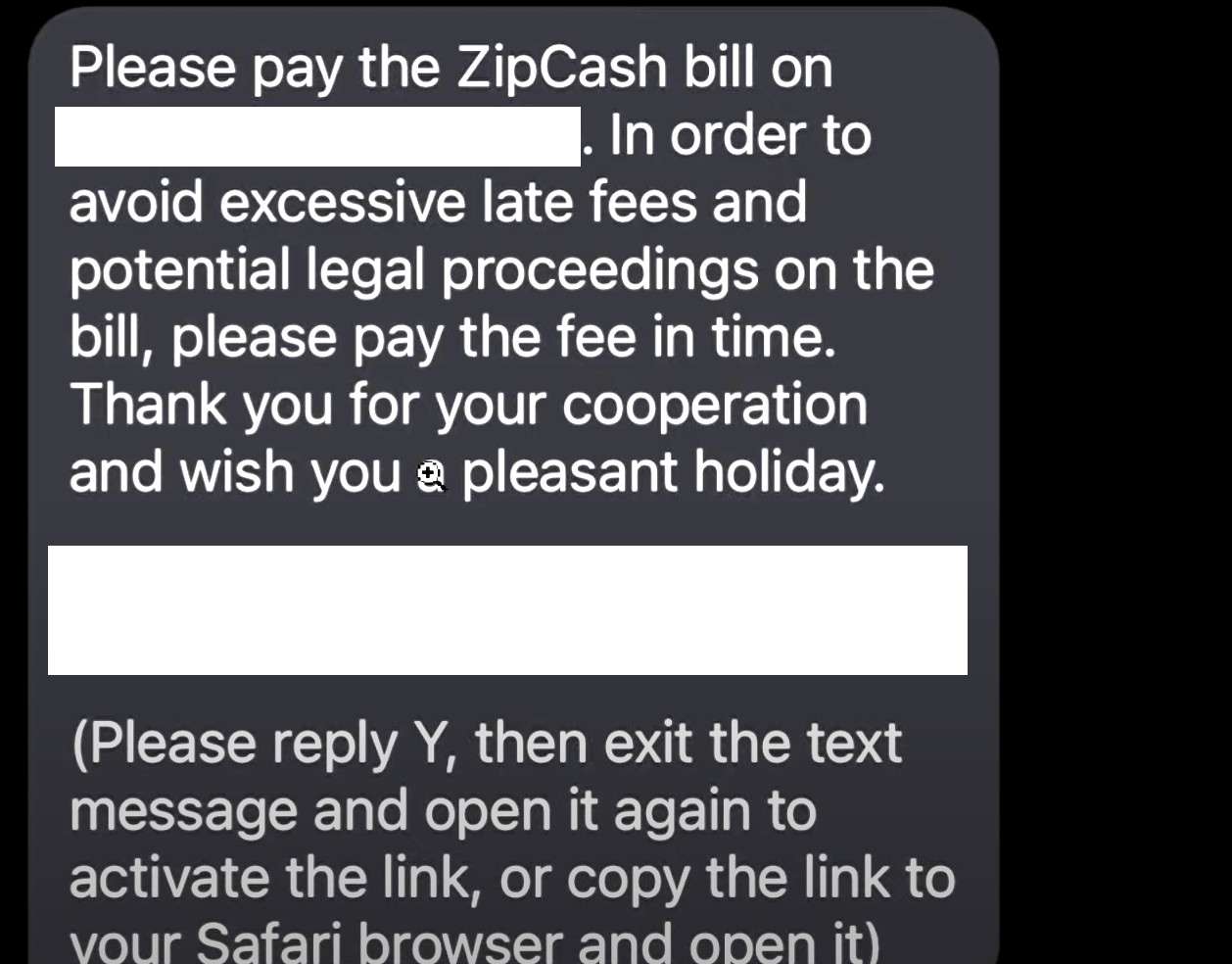
Here are some typical examples of the fraudulent text messages residents have received:
Please pay the ZipCash bill on [date]. In order to avoid excessive late fees and potential legal proceedings on the bill, please pay the fee in time. Thank you for your cooperation and wish you a pleasant holiday.
[scam link](please reply Y, then exit the text message and open it again to activate the link, or copy the link to your Safari browser and open it)
“URGENT: Our records indicate you have an outstanding balance of $73.59 for recent toll road usage. To avoid additional penalties please submit payment by end of day at nttacollections.com/paynow”
These texts often include:
- A sense of urgency, with threats of “late fees” or “legal action”
- Fake links, disguising scam sites as official NTTA pages
- Requests for personal and/or financial information
- Poor grammar and spelling errors
The messages are designed to scare recipients into immediate action before they have time to think clearly. The criminals then try to harvest personal information, credit card details, or install malware.
Some versions of the scam texts don’t include a link. Instead, they instruct targets to “reply Y” to get the link. This allows the scammers to verify they have reached a real number before wasting effort sending a fraudulent link.
Examining the Fraudulent Links
While the scam texts vary, the fake links follow consistent patterns that reveal their deceitful nature upon closer inspection:
- Misspellings – “ntta.org-pay.cbs” instead of “ntta.org”
- Strange domains – “nttapayment.site” or “ntta-zipcash.com”
- Foreign country codes – “+91” prefixes to look like official IDs
These are all efforts to mimic the real NTTA website enough to trick users at a quick glance. The slight changes let the scammers create fake sites that recipients would believe are legitimate.
When targets click these links, they are taken to convincing replicas of the NTTA site. But the forms on these fake sites are designed to harvest personal and financial data.
Forensic Analysis of the Scam Infrastructure
Security experts who have analyzed the scam texts note they come from a wide array of numbers with no discernible pattern. The texts are sent through temporary “burner” phones or VoIP numbers.
The links lead to lookalike sites hosted through third-party web services. This allows the scammers to create professionally designed sites while remaining anonymous.
The infrastructure enables them to send untraceable texts on a mass scale and dynamically adjust sites based on the success rate. Like with email phishing scams, this setup allows quick changes to prevent detection.
How the ZipCash Bill Scam Works
Now that we’ve examined the anatomy of the scam texts and links, let’s break down step-by-step how the criminals operate the scam:
1. Casting a Wide Net with Scam Texts
The first stage involves sending out scam text messages en masse to phone numbers in a targeted area code. The criminals use automation to send thousands or even millions of texts to random local numbers.
Even with a low response rate, this shotgun approach gives them access to large pools of victims. Some targets have noted receiving the texts despite having no connection to toll roads. This reveals the scammers are simply blanket targeting all residents rather than specific toll road users.
2. Using Urgency and Threats to Scare Recipients
The content of the messages is carefully crafted to instill panic and urgency in recipients. Threatening legal action or late fees is intended to make targets act rashly out of fear. This gets victims to click on the link without taking time to think it through clearly.
The scammers know many people have an instinctive reaction to avoid legal consequences or financial penalties. By exploiting this, they improve their chances victims will fall for the scam in those critical first moments.
3. Leading Victims to Fake Sites to Harvest Information
For users who click the fraudulent link, the next stage begins. The link takes them to convincingly designed fake sites that mimic official NTTA pages.
These scam sites have web forms asking users to enter personal and payment information to settle the “outstanding bill.” But any data entered goes directly to the criminals rather than paying a real bill.
4. Collecting Financial Details to Steal Funds
With the victim’s information submitted, the scammers can now access their finances and steal money. The fake sites are designed to collect credit card details, account logins, Social Security numbers, and other sensitive data.
Victims will think they are paying a legitimate bill when in reality their payment info is going into the hands of criminals. This enables the scammers to drain bank accounts, make fraudulent charges, or steal identities.
5. Retargeting Victims for Further Exploitation
Once a target is snared, scammers will often retarget them for further exploitation. Those who entered info into the fake sites will be flagged as responsive.
The criminals can contact the victims again posing as NTTA representatives for “follow-up payments.” These repeat attacks are enabled by the personal data they already stole.
Some victims have reported receiving frequent scam calls demanding more money after submitting to the initial fake texts. This multiphase scam approach allows criminals to maximize profits from each target.
What To Do If You Are Targeted by NTTA Scam Texts
If you receive a suspicious text message claiming to be from NTTA, there are steps you can take right away to protect yourself:
- Don’t click any links or reply “Y” to get a link. This verifies your number is active and leads to scam sites.
- Check the sender. The number may have a strange foreign country code or unusual characters.
- Look for spelling/grammar errors. Legitimate agencies don’t have typos.
- Search the web for the link/domain. Scam sites often have reviews warning they are fraudulent.
- Forward the text to 7726 (SPAM). This helps carriers identify and block numbers sending scam texts.
- Report it to NTTA. Contact them to notify them of texts impersonating them.
- Contact your phone carrier. They may be able to block numbers associated with reported scams.
- Monitor accounts closely. If you did enter info, scammers may target you again. Watch for fraudulent charges.
- Change passwords. Update logins for any accounts using passwords exposed through the scam.
- Consider credit monitoring. To catch any suspicious activity if the scammers have your social security number or other identity info.
Frequently Asked Questions About the ZipCash Bill Scam Texts
1. What exactly is the ZipCash Bill scam?
The ZipCash Bill scam is a text messaging phishing scam where recipients receive a text claiming to be from the North Texas Tollway Authority (NTTA) demanding payment for a supposed “ZipCash bill” to avoid late fees or legal action. The texts include fake links to convincing but fraudulent websites impersonating NTTA to steal personal and financial information from victims.
2. How do I recognize these scam text messages?
These scam texts often have a sense of urgency, threatening consequences for not paying immediately. They may contain misspellings, strange links with foreign country codes or odd domains. Legitimate toll agencies won’t demand payment over text message with threats.
3. What happens if I click the link or reply “Y”?
Replying “Y” or clicking the link verifies your number is active. It leads to sophisticated fake websites mimicking NTTA designed to harvest your personal, license, and payment information to steal your identity or drain your accounts. Avoid clicking or replying.
4. How can I report these fraudulent texts?
Save a screenshot as evidence. Report the texts to the NTTA, FCC, FTC, and your local police. File complaints with your cell carrier to block the sender. This helps identify scammers for law enforcement.
5. What are the risks if I provide my info to these scam sites?
Supplying any personal, license, or financial information to the scammers puts you at grave risk of identity theft, credit card fraud, and account hacking. Victims have faced devastating financial losses from these crimes.
6. What should I do if I already submitted information?
Immediately contact your bank and credit card companies to report fraudulent charges or suspicious activity and request fresh accounts/cards. Also monitor your credit reports for any accounts fraudulently opened in your name and report them.
7. How can I protect elderly relatives from these scams?
Educate them to never pay bills from out-of-the-blue texts and to forward suspicious messages to you for inspection first before taking any action. Set security codes with their phone provider to protect from porting scams.
8. Are these scams targeted or sent randomly?
Most victims appear to receive the scam texts randomly as criminals blanket text an entire area code hoping to snare as many victims as possible in their nets. But some may be retargeted if they already submitted data.
9. Can phone carriers block the scam messages?
Reporting the suspicious texts to your cell provider helps identify the numbers used so they can potentially block them. But scammers frequently change numbers, making this response challenging.
10. How can I stay updated on the latest scam tactics?
Be wary of any urgent financial demands via text. Search online to confirm authenticity of suspicious messages. Follow local police and consumer agencies on social media for scam alerts. Being informed is your best protection.
The Bottom Line: Stay Vigilant Against Evolving Scam Tactics
The ZipCash Bill scam texts impersonating NTTA demonstrate how criminals constantly adapt new techniques to steal personal information and money. As more commerce moves online, we must remain vigilant of phishing tactics on all channels, whether email, text, or social media messages.
The best protection is learning the warning signs of scams so you can recognize and report them before falling victim. If a suspicious text does arrive, avoid acting in haste under pressure. Instead, independently look up official contact info for the organization and reach out to verify legitimacy before providing any personal or financial information.
By staying informed, protecting our data, and alerting authorities to any scams, we can work together to frustrate these criminal enterprises. Although the scam details constantly change, the fundamental advice remains to pause and think before engaging with any unsolicited requests. Don’t let urgency or fear override your best judgment.