ESET researchers have uncovered Bootkitty, the first-ever UEFI bootkit designed to target Linux systems. This malware marks a significant evolution in the UEFI threat landscape, previously dominated by Windows-focused bootkits. While Bootkitty appears to be a proof-of-concept and has not yet been observed in active attacks, its existence signals a concerning shift for Linux-based platforms.
Bootkitty discovery and analysis
ESET researchers Martin Smolár and Peter Strýček
analyzed Bootkitty after a sample named bootkit.efi was uploaded to VirusTotal in November 2024. This UEFI bootkit was specifically tailored to a few Ubuntu Linux versions and signed with a self-signed certificate, limiting its functionality on systems with UEFI Secure Boot enabled—unless attackers had previously installed their certificates.
Bootkitty's main objectives include:
- Disabling kernel signature verification to permit unauthorized modules.
- Preloading unknown ELF binaries during the system's initialization phase.
- Patching GRUB and kernel functions in memory to bypass integrity checks.
Additionally, ESET identified a potentially related kernel module, BCDropper, and a secondary binary, BCObserver, linked to the bootkit's functionality.
Technical overview
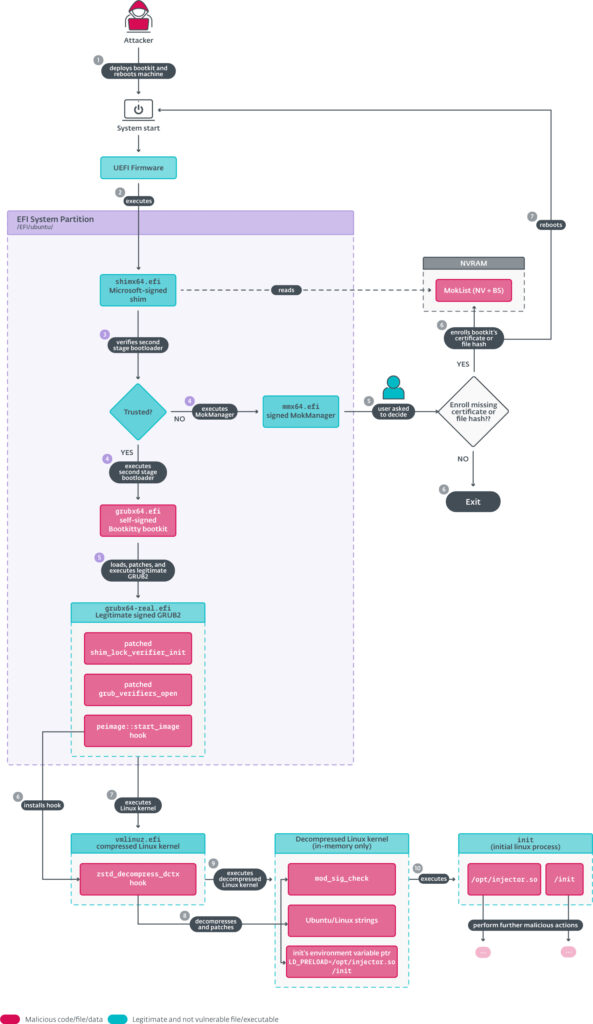
Bootkitty operates by leveraging the UEFI environment to manipulate the bootloader and kernel before the operating system initializes. The bootkit's primary functions are the following two:
- Hooks GRUB functions responsible for starting the Linux kernel, bypassing signature checks by modifying verification processes.
- Alters hardcoded offsets in the Linux kernel image to disable module signature checks and preload binaries via the LD_PRELOAD environment variable, a common tactic for injecting malicious code.
However, Bootkitty's use of hardcoded patterns and offsets makes it functional only in a narrow range of configurations. This limitation, combined with the presence of unused functions and artifacts, suggests that Bootkitty is an experimental or early-stage project rather than a mature malware tool.
Bootkitty's execution flow
ESET
Connections to BCDropper and BCObserver
ESET linked Bootkitty to a kernel module named BCDropper, which was also uploaded to VirusTotal. This module drops an ELF binary (BCObserver) into /opt/observer, which monitors system startup and loads another kernel module via finit_module. Despite the connections, ESET cannot definitively confirm the same authorship for Bootkitty and BCDropper.
BCDropper also exhibits rootkit capabilities, such as hiding processes, files, and ports, and the ability to self-conceal by removing its entry from the kernel module list.
Broader implications
This discovery disrupts the belief that UEFI bootkits are exclusively Windows threats. Linux systems, widely used in enterprise servers and cloud environments, have largely been overlooked by attackers in the pre-boot phase. Bootkitty demonstrates how attackers could expand their arsenal to target these systems, even with limited reach in its current state.
ESET researchers emphasize that Bootkitty's capability to disable key security features, such as kernel signature verification, makes it a precursor to more sophisticated attacks.
ESET advises the following to mitigate UEFI bootkit threats like Bootkitty:
- Enable UEFI Secure Boot to ensure all boot components are signed with trusted certificates.
- Update firmware and operating systems regularly to reduce vulnerabilities exploitable by bootkits.
- Monitor for anomalies like changes in kernel integrity, unexpected modules, or tampered files.
- Restore legitimate files, such as GRUB loaders, to their original locations if tampering is detected.
While Bootkitty currently poses minimal risk due to its proof-of-concept status, its emergence highlights the need for proactive defense measures in Linux environments.