- Aug 30, 2012
- 6,598
A cyber-espionage group believed to operate from Lebanon and to have political ties has been identified by security researchers to rely in its targeted attacks on a custom remote access Trojan (RAT) called “Explosive.”
The threat actor aims at compromising computers belonging to individuals, companies and institutions across the world, some of the identified victims being related to Israel, although live infections have been detected in the US, Canada, UK, Turkey and Lebanon, too.
Trojan constantly records keystrokes
Named “Volatile Cedar” by researchers at Check Point Software Technologies, the campaign has been active since November 2012 (as per the sample compilation date of the first version) and its operators managed to fly under the radar, despite not being highly sophisticated in nature.
This was done by continually adapting their techniques in accordance to the victim’s actions and antivirus detection improvements.
Entities infected with Explosive malware range from defense contractor firms, telecommunications and media companies to educational institutions.
The features of the threat, as well as the nature of its targets, rule out the possibility of financial purposes being pursued since the tool is aimed at collecting information from a small number of select victims.
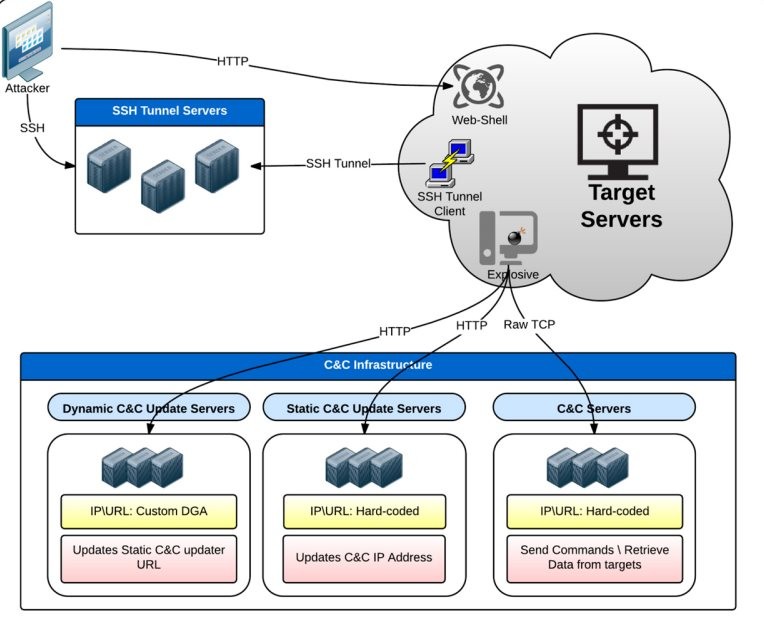
According to the analysis from Check Point, the malware constantly records keystrokes and clipboard content, and sends the data to the remote machine; it can also take screenshots and run commands on the infected system.
Additional functionality refers to fingerprinting the compromised machine, self-destruction capabilities, spreading across the network and a remote shell.
Explosive RAT planted after careful planning
The researchers say that Volatile Cedar did not go unnoticed for the past years and its Explosion implant was detected heuristically by antivirus solutions.
However, as soon as this happened, the threat actor would immediately take action and modify the tool so that it would pass undetected.
Also, each version was configured taking into account the computer activity of the victim.
“Our analysis leads us to believe that the attackers conduct a fair amount of intelligence gathering to tailor each infection to its specific target,” a report from Check Point says.
The attack begins with compromising Internet-facing web servers (via glitches found both automatically and manually), which are then used in reconnaissance operations that allow determining other targets in the network as well as deeper infiltration.
Efficient stealth tactics
Check Point identified five versions of Explosive malware, each one succeeding the previous one once antivirus products raised the alarm.
Stealth tactics implemented by Volatile Cedar also included RAM monitoring, to keep Explosive processes from being picked up by server administration utilities. This was achieved by restarting the parent process once memory usage reached a certain threshold.
Additionally, all API activities that could have been deemed suspicious were contained in a separate DLL, thus ensuring that the Trojan itself would not be detected.
On the same note, Volatile Cedar customized the Trojan for each target, so that it initiated network communication during the victim’s working hours and avoid low traffic periods, when this activity would stand out.
The information exchange with the command and control (C&C) servers is obfuscated in such a way that some network inspection devices are fooled into labeling the communication as network "noise" and would not raise the flag for suspicious activity.
Evidence points to Lebanon-based attackers
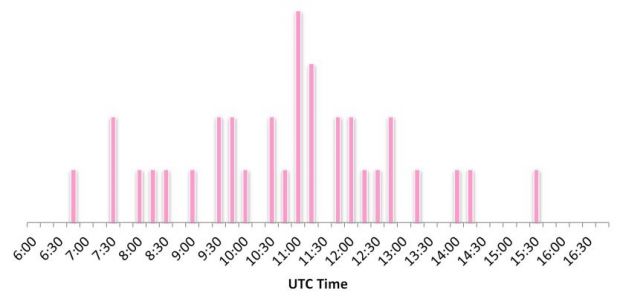
Attributing any cyber-espionage operation to a certain actor is not an easy task, but Check Point points to Lebanon as the geographical location of the attackers, based on the compilation hours of Explosive samples (GMT+2) and the fact that some C&C servers were hosted at a major Lebanese hosting company.
Also fueling this conclusion is a failure from the attackers, who exposed the DNS registrant contact for a short period of time when WHOIS privacy feature was inactive, revealing an email address associated with social media accounts supportive of Lebanese political activism.
“The combination of these factors leads us to believe that the attack originated or is sponsored by groups affiliated with Lebanon and the specific targets are chosen based on nation-state/political-group interests,” Check Point says, admitting that it has no hard evidence to support their attribution theory and many of the factors taken into consideration could be forged or misinterpreted at this stage.
Volatile Cedar cyber-espionage campaign is currently ongoing.
Compilation time for the Explosion samples analyzed
The threat actor aims at compromising computers belonging to individuals, companies and institutions across the world, some of the identified victims being related to Israel, although live infections have been detected in the US, Canada, UK, Turkey and Lebanon, too.
Trojan constantly records keystrokes
Named “Volatile Cedar” by researchers at Check Point Software Technologies, the campaign has been active since November 2012 (as per the sample compilation date of the first version) and its operators managed to fly under the radar, despite not being highly sophisticated in nature.
This was done by continually adapting their techniques in accordance to the victim’s actions and antivirus detection improvements.
Entities infected with Explosive malware range from defense contractor firms, telecommunications and media companies to educational institutions.
The features of the threat, as well as the nature of its targets, rule out the possibility of financial purposes being pursued since the tool is aimed at collecting information from a small number of select victims.
According to the analysis from Check Point, the malware constantly records keystrokes and clipboard content, and sends the data to the remote machine; it can also take screenshots and run commands on the infected system.
Additional functionality refers to fingerprinting the compromised machine, self-destruction capabilities, spreading across the network and a remote shell.
Explosive RAT planted after careful planning
The researchers say that Volatile Cedar did not go unnoticed for the past years and its Explosion implant was detected heuristically by antivirus solutions.
However, as soon as this happened, the threat actor would immediately take action and modify the tool so that it would pass undetected.
Also, each version was configured taking into account the computer activity of the victim.
“Our analysis leads us to believe that the attackers conduct a fair amount of intelligence gathering to tailor each infection to its specific target,” a report from Check Point says.
The attack begins with compromising Internet-facing web servers (via glitches found both automatically and manually), which are then used in reconnaissance operations that allow determining other targets in the network as well as deeper infiltration.
Efficient stealth tactics
Check Point identified five versions of Explosive malware, each one succeeding the previous one once antivirus products raised the alarm.
Stealth tactics implemented by Volatile Cedar also included RAM monitoring, to keep Explosive processes from being picked up by server administration utilities. This was achieved by restarting the parent process once memory usage reached a certain threshold.
Additionally, all API activities that could have been deemed suspicious were contained in a separate DLL, thus ensuring that the Trojan itself would not be detected.
On the same note, Volatile Cedar customized the Trojan for each target, so that it initiated network communication during the victim’s working hours and avoid low traffic periods, when this activity would stand out.
The information exchange with the command and control (C&C) servers is obfuscated in such a way that some network inspection devices are fooled into labeling the communication as network "noise" and would not raise the flag for suspicious activity.
Evidence points to Lebanon-based attackers
Attributing any cyber-espionage operation to a certain actor is not an easy task, but Check Point points to Lebanon as the geographical location of the attackers, based on the compilation hours of Explosive samples (GMT+2) and the fact that some C&C servers were hosted at a major Lebanese hosting company.
Also fueling this conclusion is a failure from the attackers, who exposed the DNS registrant contact for a short period of time when WHOIS privacy feature was inactive, revealing an email address associated with social media accounts supportive of Lebanese political activism.
“The combination of these factors leads us to believe that the attack originated or is sponsored by groups affiliated with Lebanon and the specific targets are chosen based on nation-state/political-group interests,” Check Point says, admitting that it has no hard evidence to support their attribution theory and many of the factors taken into consideration could be forged or misinterpreted at this stage.
Volatile Cedar cyber-espionage campaign is currently ongoing.
Compilation time for the Explosion samples analyzed

