5 Ways to Secure Wi-Fi Networks
Wi-Fi is one entry-point hackers can use to get into your network without setting foot inside your building because wireless is much more open to eavesdroppers than wired networks, which means you have to be more diligent about security.
But there’s a lot more to Wi-Fi security than just setting a simple password. Investing time in learning about and applying enhanced security measures can go a long way toward better protecting your network. Here are six tips to betters secure your Wi-Fi network.
Use an inconspicuous network name (SSID)
The service set identifier (SSID) is one of the most basic Wi-Fi network settings. Though it doesn’t seem like the network name could compromise security, it certainly can. Using a too common of a SSID, like “wireless” or the vendor’s default name, can make it easier for someone to crack the personal mode of WPA or WPA2 security. This is because the encryption algorithm incorporates the SSID, and password cracking dictionaries used by hackers are preloaded with common and default SSIDs. Using one of those just makes the hacker’s job easier.
(As we discuss later, this vulnerability doesn’t apply to networks using the enterprise mode of WPA or WPA2 security, one of the many benefits of using the enterprise mode.)
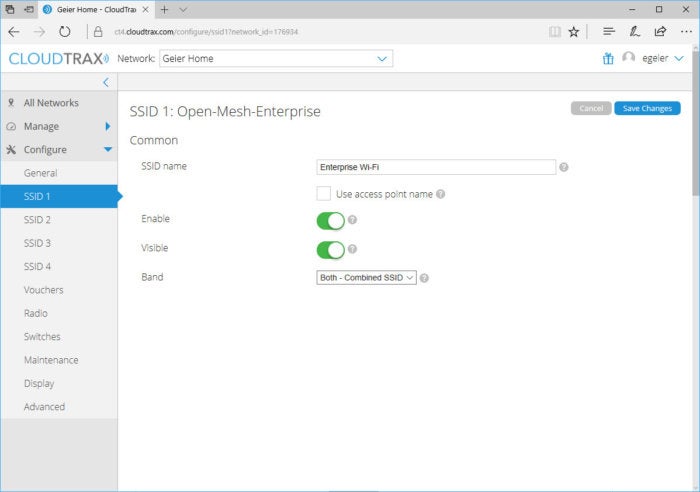 CloudTrax
CloudTrax
Name your network wisely - it something generic but not too common and without revealing the location.
Although it might make sense to name the SSID something easily identifiable, like the company name, address, or suite number, that might not be the best idea either. This is especially true if the network is in a shared building or in close proximity to other buildings or networks. If hackers drive by a congested area and see a dozen different Wi-Fi networks pop-up, they would likely target the one easiest to identify, which could help them understand what they might gain by hacking it. They might also choose one that’s easier to find in a congested area.
It is possible to turn off SSID broadcast, essentially making the name of your network invisible, but I don’t suggest that. Forcing users to manually enter the SSID, and the negative performance effects of probe requests on the Wi-Fi, typically outweigh the security benefit. And someone with the right tools can still capture the SSID from sniffing other network traffic.
Remember physical security
Wireless security—or all of IT security for that matter—isn’t all about fancy technologies and protocols. You can have the best encryption possible and still be vulnerable. Physical security is one of those vulnerabilities. Locking down just your wiring closets isn’t enough, either.
Most access points (APs) have a reset button that someone can press to restore factory default settings, removing the Wi-Fi security and allowing anyone to connect. Thus, the APs distributed throughout your facility need to be physically secured as well to prevent tampering. Ensure they are always mounted out of reach and consider using any locking mechanisms offered by the AP vendor to physically limit access to the AP buttons and ports.
 Cisco
Cisco
An example of a reset button on an access point, courtesy of Cisco.
Another physical security concern with Wi-Fi is when someone adds an unauthorized AP to the network, typically called a “rogue AP.” This could be done for legit reasons by an employee wanting to add more Wi-Fi coverage, or for ill-intended purposes by an employee or even an outsider who gains access to the facility. To help prevent these types of rogue APs, ensure any unused ethernet ports (like wall ports or loose ethernet runs) are disabled. You could physically remove the ports or cables, or disable the connectivity of that outlet or cable on the router or switch. Or if you really want to beef up security, enable 802.1X authentication on the wired side, if your router or switch supports that, so any device plugging into the ethernet ports has to enter log-in credentials to gain network access.
Use Enterprise WPA2 with 802.1X authentication
One of the most beneficial Wi-Fi security mechanisms you can put into place is deploying the enterprise mode of Wi-Fi security, because it authenticates every user individually: Everyone can have their own Wi-Fi username and password. So if a laptop or mobile device is lost or stolen, or an employee leaves the company, all you have to do is change or revoke that particular user’s log-ins.
(In personal mode, by contrast, all users share the same Wi-FI password, so when devices go missing or employees leave you have to change the password on every single device — a huge hassle.)
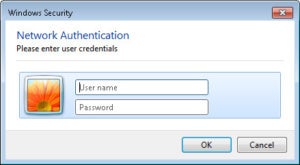 Microsoft
Microsoft
With enterprise Wi-Fi security, users enter their unique username and password when connecting.
Another great advantage of enterprise mode is that every user is assigned his or her own encryption key. That means users can only decrypt data traffic for their own connection — no snooping on anyone else’s wireless traffic.
To put your APs into enterprise mode you'll first need to set up a RADIUS server. This enables user authentication and connects to or contains the database or directory (such as Active Directory) that holds everyone’s usernames and passwords.
Although you could deploy a standalone RADIUS server, you should first check if your other servers (like a Windows Server) already provide this function. If not, consider a cloud-based or hosted RADIUS service. Also keep in mind that some wireless access points or controllers provide a basic built-in RADIUS server, but their performance limits and limited functionality typically make them only useful for smaller networks.
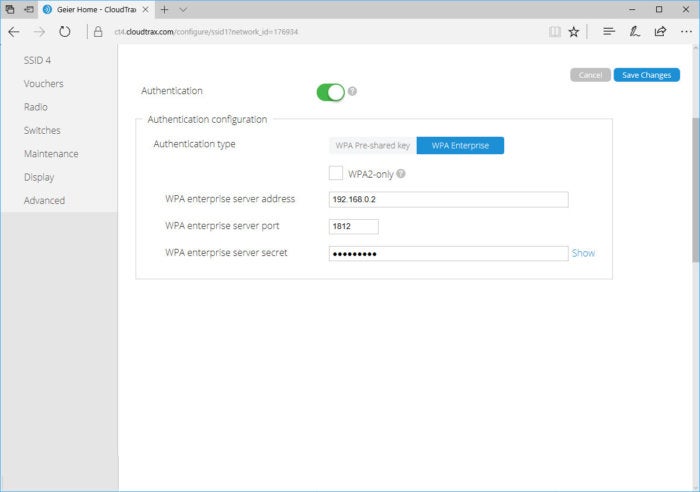 CloudTrax
CloudTrax
An example of how you'd configure the APs with the RADIUS server’s IP, port and secret.
Secure the 802.1X client settings
Like other security technologies, the enterprise mode of Wi-Fi security still has some vulnerabilities. One of these is man-in-the-middle attacks, with a hacker sitting in an airport or cafe, or even outside in the parking lot of a corporate office. Someone could set up a fake Wi-Fi network with the same or similar SSID as the network they’re trying to imitate; when your laptop or device attempts to connect, a bogus RADIUS server could capture your login credentials. The thief could then utilize your login credentials to connect to the real Wi-Fi network.
A way to prevent man-in-the-middle attacks with 802.1X authentication is to utilize server verification on the client side. When server verification is enabled on the wireless client, the client won’t pass your Wi-Fi login credentials to the RADIUS server until it verifies it’s communicating with a legit server. The exact server verification capabilities and requirements you can impose on the clients will vary, depending upon the device or OS of the client.
In Windows, for instance, you can enter the domain name(s) of the legit server, select the certificate authority that issued the server’s certificate, and then choose to not allow any new servers or certificate authorities. So if someone has set up up a fake Wi-Fi network and RADIUS server and you try to log on to it, Windows will stop you from connecting.
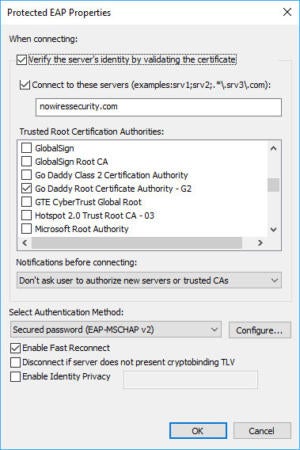 Microsoft
Microsoft
You find the 802.1X server verification feature in Windows when configuring the EAP settings of the Wi-Fi connection.
Use rogue-AP detection or wireless intrusion prevention
We’ve already touched on three vulnerable access point scenarios: One where an attacker could set up a fake Wi-Fi network and RADIUS server, another where someone could reset an AP to factory defaults, and a third scenario where someone could plug in their own AP.
Each of these unauthorized APs could go undetected by IT staff for a long period of time if proper protection isn’t put in place. Thus, it’s a good idea to enable any type of rogue detection offered by your AP or wireless controller vendor. The exact detection method and functionality vary, but most will at least periodically scan the airwaves and send you an alert if a new AP is detected within range of the authorized APs.
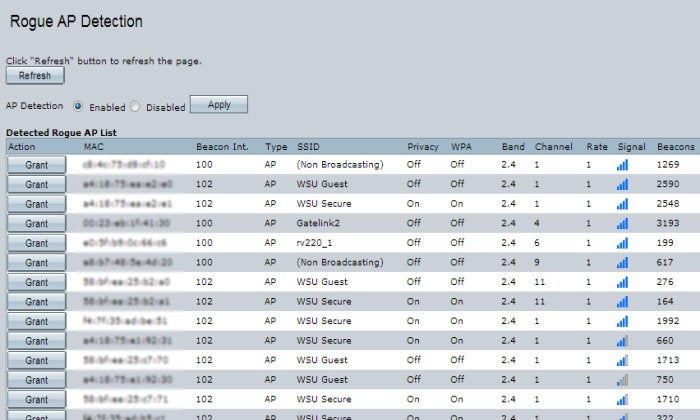 Cisco
Cisco
An example of simple rogue AP detection, courtesy of Cisco, where you’d see a list of other APs in the area.
For even more detection capabilities, some AP vendors offer a full-fledged wireless intrusion detection system (WIDS) or intrusion protection system (WIPS) that can sense a range of wireless attacks and suspicious activity along with rogue APs. These include erroneous de-authentication requests, mis-association requests, and MAC address spoofing.
Furthermore, if it’s a true WIPS offering protection rather than a WIDS offering just detection, it should be able to take automatic countermeasures, such as disassociating or blocking a suspect wireless client to protect the network under attack.
Wi-Fi is one entry-point hackers can use to get into your network without setting foot inside your building because wireless is much more open to eavesdroppers than wired networks, which means you have to be more diligent about security.
But there’s a lot more to Wi-Fi security than just setting a simple password. Investing time in learning about and applying enhanced security measures can go a long way toward better protecting your network. Here are six tips to betters secure your Wi-Fi network.
Use an inconspicuous network name (SSID)
The service set identifier (SSID) is one of the most basic Wi-Fi network settings. Though it doesn’t seem like the network name could compromise security, it certainly can. Using a too common of a SSID, like “wireless” or the vendor’s default name, can make it easier for someone to crack the personal mode of WPA or WPA2 security. This is because the encryption algorithm incorporates the SSID, and password cracking dictionaries used by hackers are preloaded with common and default SSIDs. Using one of those just makes the hacker’s job easier.
(As we discuss later, this vulnerability doesn’t apply to networks using the enterprise mode of WPA or WPA2 security, one of the many benefits of using the enterprise mode.)
 CloudTrax
CloudTraxName your network wisely - it something generic but not too common and without revealing the location.
Although it might make sense to name the SSID something easily identifiable, like the company name, address, or suite number, that might not be the best idea either. This is especially true if the network is in a shared building or in close proximity to other buildings or networks. If hackers drive by a congested area and see a dozen different Wi-Fi networks pop-up, they would likely target the one easiest to identify, which could help them understand what they might gain by hacking it. They might also choose one that’s easier to find in a congested area.
It is possible to turn off SSID broadcast, essentially making the name of your network invisible, but I don’t suggest that. Forcing users to manually enter the SSID, and the negative performance effects of probe requests on the Wi-Fi, typically outweigh the security benefit. And someone with the right tools can still capture the SSID from sniffing other network traffic.
Remember physical security
Wireless security—or all of IT security for that matter—isn’t all about fancy technologies and protocols. You can have the best encryption possible and still be vulnerable. Physical security is one of those vulnerabilities. Locking down just your wiring closets isn’t enough, either.
Most access points (APs) have a reset button that someone can press to restore factory default settings, removing the Wi-Fi security and allowing anyone to connect. Thus, the APs distributed throughout your facility need to be physically secured as well to prevent tampering. Ensure they are always mounted out of reach and consider using any locking mechanisms offered by the AP vendor to physically limit access to the AP buttons and ports.
 Cisco
CiscoAn example of a reset button on an access point, courtesy of Cisco.
Another physical security concern with Wi-Fi is when someone adds an unauthorized AP to the network, typically called a “rogue AP.” This could be done for legit reasons by an employee wanting to add more Wi-Fi coverage, or for ill-intended purposes by an employee or even an outsider who gains access to the facility. To help prevent these types of rogue APs, ensure any unused ethernet ports (like wall ports or loose ethernet runs) are disabled. You could physically remove the ports or cables, or disable the connectivity of that outlet or cable on the router or switch. Or if you really want to beef up security, enable 802.1X authentication on the wired side, if your router or switch supports that, so any device plugging into the ethernet ports has to enter log-in credentials to gain network access.
Use Enterprise WPA2 with 802.1X authentication
One of the most beneficial Wi-Fi security mechanisms you can put into place is deploying the enterprise mode of Wi-Fi security, because it authenticates every user individually: Everyone can have their own Wi-Fi username and password. So if a laptop or mobile device is lost or stolen, or an employee leaves the company, all you have to do is change or revoke that particular user’s log-ins.
(In personal mode, by contrast, all users share the same Wi-FI password, so when devices go missing or employees leave you have to change the password on every single device — a huge hassle.)
 Microsoft
MicrosoftWith enterprise Wi-Fi security, users enter their unique username and password when connecting.
Another great advantage of enterprise mode is that every user is assigned his or her own encryption key. That means users can only decrypt data traffic for their own connection — no snooping on anyone else’s wireless traffic.
To put your APs into enterprise mode you'll first need to set up a RADIUS server. This enables user authentication and connects to or contains the database or directory (such as Active Directory) that holds everyone’s usernames and passwords.
Although you could deploy a standalone RADIUS server, you should first check if your other servers (like a Windows Server) already provide this function. If not, consider a cloud-based or hosted RADIUS service. Also keep in mind that some wireless access points or controllers provide a basic built-in RADIUS server, but their performance limits and limited functionality typically make them only useful for smaller networks.

An example of how you'd configure the APs with the RADIUS server’s IP, port and secret.
Secure the 802.1X client settings
Like other security technologies, the enterprise mode of Wi-Fi security still has some vulnerabilities. One of these is man-in-the-middle attacks, with a hacker sitting in an airport or cafe, or even outside in the parking lot of a corporate office. Someone could set up a fake Wi-Fi network with the same or similar SSID as the network they’re trying to imitate; when your laptop or device attempts to connect, a bogus RADIUS server could capture your login credentials. The thief could then utilize your login credentials to connect to the real Wi-Fi network.
A way to prevent man-in-the-middle attacks with 802.1X authentication is to utilize server verification on the client side. When server verification is enabled on the wireless client, the client won’t pass your Wi-Fi login credentials to the RADIUS server until it verifies it’s communicating with a legit server. The exact server verification capabilities and requirements you can impose on the clients will vary, depending upon the device or OS of the client.
In Windows, for instance, you can enter the domain name(s) of the legit server, select the certificate authority that issued the server’s certificate, and then choose to not allow any new servers or certificate authorities. So if someone has set up up a fake Wi-Fi network and RADIUS server and you try to log on to it, Windows will stop you from connecting.
 Microsoft
MicrosoftYou find the 802.1X server verification feature in Windows when configuring the EAP settings of the Wi-Fi connection.
Use rogue-AP detection or wireless intrusion prevention
We’ve already touched on three vulnerable access point scenarios: One where an attacker could set up a fake Wi-Fi network and RADIUS server, another where someone could reset an AP to factory defaults, and a third scenario where someone could plug in their own AP.
Each of these unauthorized APs could go undetected by IT staff for a long period of time if proper protection isn’t put in place. Thus, it’s a good idea to enable any type of rogue detection offered by your AP or wireless controller vendor. The exact detection method and functionality vary, but most will at least periodically scan the airwaves and send you an alert if a new AP is detected within range of the authorized APs.

An example of simple rogue AP detection, courtesy of Cisco, where you’d see a list of other APs in the area.
For even more detection capabilities, some AP vendors offer a full-fledged wireless intrusion detection system (WIDS) or intrusion protection system (WIPS) that can sense a range of wireless attacks and suspicious activity along with rogue APs. These include erroneous de-authentication requests, mis-association requests, and MAC address spoofing.
Furthermore, if it’s a true WIPS offering protection rather than a WIDS offering just detection, it should be able to take automatic countermeasures, such as disassociating or blocking a suspect wireless client to protect the network under attack.