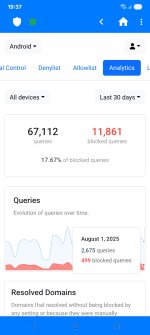
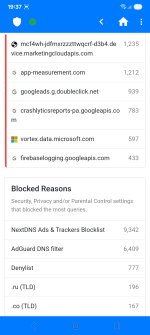
Your smartphone is a portable hub for your personal and professional life, making it a prime target for cybercriminals. This guide focuses on the simple, yet crucial, habits that will protect your mobile device and the sensitive data it holds.
By making these simple habits a regular part of your mobile routine, you can significantly reduce the risk of a security breach and keep your digital life safe and private.
1. Secure Your Device Physically
The first line of defense is preventing unauthorized access if your phone is lost or stolen.- Use a Strong Lock Screen: This is non-negotiable. Use a strong PIN (at least six digits), a complex password, or biometrics like a fingerprint scanner or facial recognition.
- Configure "Find My Device" Service: Both Android and iOS have built-in services to help you locate a lost device, remotely lock it, display a message on the screen, or even erase all its data. Make it a habit to ensure this feature is enabled and configured.
2. Be Skeptical of Links (Phishing and Smishing)
This is one of the most common and dangerous ways malware is delivered. Scammers use a variety of tricks to get you to click.- Links in Emails and Text Messages: Phishing and "smishing" attacks often create a sense of urgency. They may claim to be from your bank, a delivery service, or a government agency, and tell you there's a problem that requires immediate action. Never click on a link in an email or text message that you weren't expecting.
- The Golden Rule: If you get an email or text from a company you do business with, don't use the link they sent. Instead, open your browser and navigate to the company's official website or app yourself. Log in from there to check for any alerts or issues.
- Beware of "Free" Offers and Pop-ups: Avoid clicking on ads that promise free prizes or services. These are often a front for malicious websites that try to steal your information or download malware to your device. Close the browser tab immediately.
3. Be Smart with Apps
Apps are the main way malware gets onto your phone. A little caution goes a long way.- Only Download from Official App Stores: Stick to the Google Play Store and Apple App Store. They have a vetting process to catch and remove malicious apps. Sideloading apps from unofficial sources is extremely risky.
- Review App Permissions: Before you install an app, take a moment to look at the permissions it's requesting. Does a simple game really need access to your contacts, camera, or location? If the permissions seem excessive, it's a red flag.
- Delete Unused Apps: Make it a habit to regularly review and delete apps you no longer use. They can be a security liability and often collect data in the background.
4. Manage Your Connections Wisely
Your phone's connectivity features can be a gateway for security risks if not managed properly.- Turn Off Wi-Fi and Bluetooth When Not in Use: Leaving these on makes your phone constantly search for networks, which not only drains battery but can also expose you to malicious attacks.
- Treat Public Wi-Fi as Unsecured: Never perform sensitive activities like online banking or shopping on a public Wi-Fi network unless you are using a Virtual Private Network (VPN) to encrypt your traffic.
- Don't Auto-Connect to Open Wi-Fi: Configure your phone to ask you before connecting to new Wi-Fi networks to prevent it from automatically joining an unsecured network.
5. Stay Up-to-Date
Operating system and app updates are critical for patching security vulnerabilities.- Enable Automatic Updates: Configure both your mobile OS (iOS or Android) and your apps to update automatically.
- Don't Ignore Update Notifications: When an update is available, install it as soon as you can. These updates often contain critical security patches that close newly discovered security holes.
6. Back Up Your Data
Even with the best habits, accidents and theft can happen. A backup is your ultimate safety net.- Enable Cloud Backups: Both Android and iOS offer free, automated cloud backup services that can save your photos, contacts, and app data.
- Perform Manual Backups: For critical information, consider making a manual backup to your computer or an external drive. This provides a second, offline copy of your most important data.
By making these simple habits a regular part of your mobile routine, you can significantly reduce the risk of a security breach and keep your digital life safe and private.