Peter Levashov Allegedly Distributed Spam, Ransomware via Kelihos Botnet

Peter Levashov, in an undated picture. (Photo: Maria Levashov)
A Russian man arrested last year in Spain has been extradited to the United States to face allegations that he ran a notorious botnet that pumped out spam, banking Trojans and ransomware, including a strain named "JokeFromMars."
See Also: How to Scale Your Vendor Risk Management Program
The U.S. Department of Justice has accused Peter Yuryevich Levashov, 37, of St. Petersburg, Russia, of "harvesting login credentials, distributing bulk spam emails and installing ransomware and other malicious software" by owning and operating a botnet called Kelihos.
Appearing Friday in Connecticut federal court, Levashov entered not-guilty pleas, Thomas Carson, a spokesman for the U.S. Attorney for Connecticut, tells Information Security Media Group. Carson says jury selection for Levashov's case is scheduled to begin April 10.
If convicted of all charges, Levashov faces up to 52 years in prison.
Levashov remains detained, pending trial, with U.S. prosecutors arguing in a Friday court motion that "there is a serious risk that the defendant will flee if released," noting that the Russian national had never previously been in the United States. "All of his immediate family members are believed to be in Russia," according to court documents.
Levashov was arrested at the request of U.S. authorities last April in Spain, where he was vacationing with his wife and son. According to a criminal complaint and arrest warrant issued by the U.S. Attorney's Office in Connecticut, the FBI alleges that Levashov - aka Petr Levashov, Peter Severa, Petr Severa, Sergey Astakhov - ran and profited from Kelihos.
Spanish police referred to Levashov as a computer programmer by trade.
Source: Spamhaus
"Levashov is alleged to have controlled and operated the Kelihos botnet, which was used to distribute hundreds of millions of fraudulent emails per year, intercept credentials to online and financial accounts belonging to thousands of Americans, and spread ransomware throughout our networks," says John P. Cronan, the acting assistant attorney general of the criminal division of the U.S. Justice Department.
Prosecutors say that at times of peak operation, Kelihos sent out during a 24-hour period more than 2,500 unsolicited spam emails, often advertising fraudulent pump-and-dump stock schemes or carrying banking Trojans, ransomware, phishing attacks and malware-as-a-service offerings.
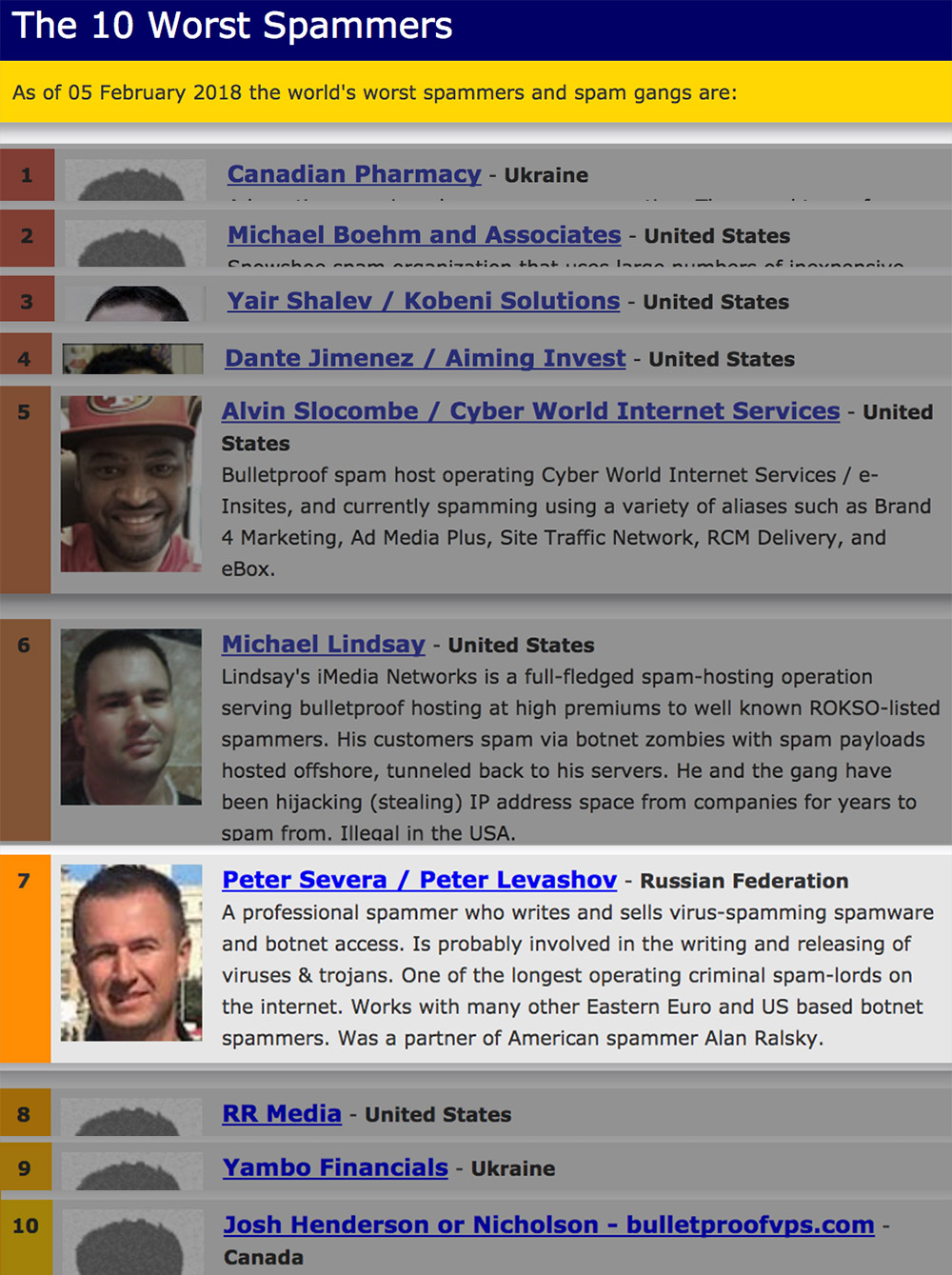
Anti-spam organization Spamhaus suspects Severa - one of Levashov's alleged aliases - ran both the Waledac and Kelihos botnets. On its world's worst spammers list, Spamhaus says Severa places seventh, saying he "writes and sells virus-spamming spamware and botnet access" and that he is "one of the longest operating criminal spam-lords on the internet."
The FBI appears to have been tracking the alleged operator of Kelihos for some time. In 2008, the Justice Department accused "Peter Severa, age unknown, of Russia" of collaborating with Alan M. Ralsky as part of a "complicated stock spam pump and dump scheme," and a related complaint accuses Severa of violating U.S. fraud and wiretapping statutes.
FBI: Spam Campaigns, Payable in Bitcoin
An eight-count indictment against Levashov shows the FBI tied the defendant to various IP addresses he was allegedly using as well as intercepted or obtained some of his alleged communications.
"On or about March 2, 2016, Levashov sent an email from peter@severa.biz to a customer stating that "mailing costs 500 usd per 1 mil emails, 750 us=d per 2mil, 1k per 3mil," the indictment reads. "On or about March 21, 2017, Levashov instructed a customer for a spam campaign to pay him by bitcoin and stated that he charged $300 per 1 million emails, but more for phishing and scams."
Justice Department: Indictment Is Criminal
Upon his arrest, Russian media outlets - including Russian state propaganda arm RT, formerly known as Russia Today - circulated stories that Levashov had hacked the Democratic National Committee. But U.S. officials quickly dismissed any suggestion that there were any national security ties to Levashov's arrest, saying it was solely a criminal matter (see The US Presidential Election Hacker Who Wasn't).
After Levashov was arrested, the Justice Department quickly filed for his extradition.
Levashov fought the extradition request, arguing in court that his arrest had been politically motivated, in reprisal for alleged Russian government meddling in the 2016 presidential election. Levashov also claimed that he would be tortured or killed if sent to the United States, owning to work he'd done for President Vladimir Putin's United Russia, Reuters reported, citing Russian state news agency RIA Novosti.
"I collected different information about opposition parties and delivered it to the necessary people at the necessary time," RIA quoted him as saying. RIA added that Levashov was a serving officer in the Russian army with access to classified information.
Lisov Set for U.S. Extradition
Levashov is the second Russian citizen arrested in Spain in recent months to have had his extradition request to the United States approved by Spanish authorities.
In January 2017, Stanislav Lisov was arrested by Spanish police at U.S. request. Lisov had been on his honeymoon. He's been charged with crimes related to the "Neverquest" banking Trojan, also known as Vawtrak and Snifula. Based on Justice Department allegations, the actions of Lisov - aka "Black" and "Blackf" - resulted in $855,000 being stolen from U.S. banking customers between June 2012 and January 2015 (see Spanish Court Approves Suspected Hacker's Extradition).
Lisov's defense team had attempted to block the U.S. extradition request, claiming it was "a political act."
In both Levashov and Lisov's cases, the Russian government filed competing extradition requests, seeking to prevent them from being sent to the United States.
After appealing Spain's decision to extradite him, Lisov in December 2017 lost his appeal. He's now due to be extradited to the United States.
While Russia's competing extradition requests for alleged cybercriminals may make for good domestic headlines, they don't appear to have ever succeeded (see Russia's Accused Hacker Repeat Play: Extradition Tug of War).