A new vulnerability arised in Safari Web Browser that can lead to an address spoofing allowing attackers to show any URL address while loading a different web page. While this proof of concept is not perfect, it could definitely be fixed to be used by phishing attacks very easily.
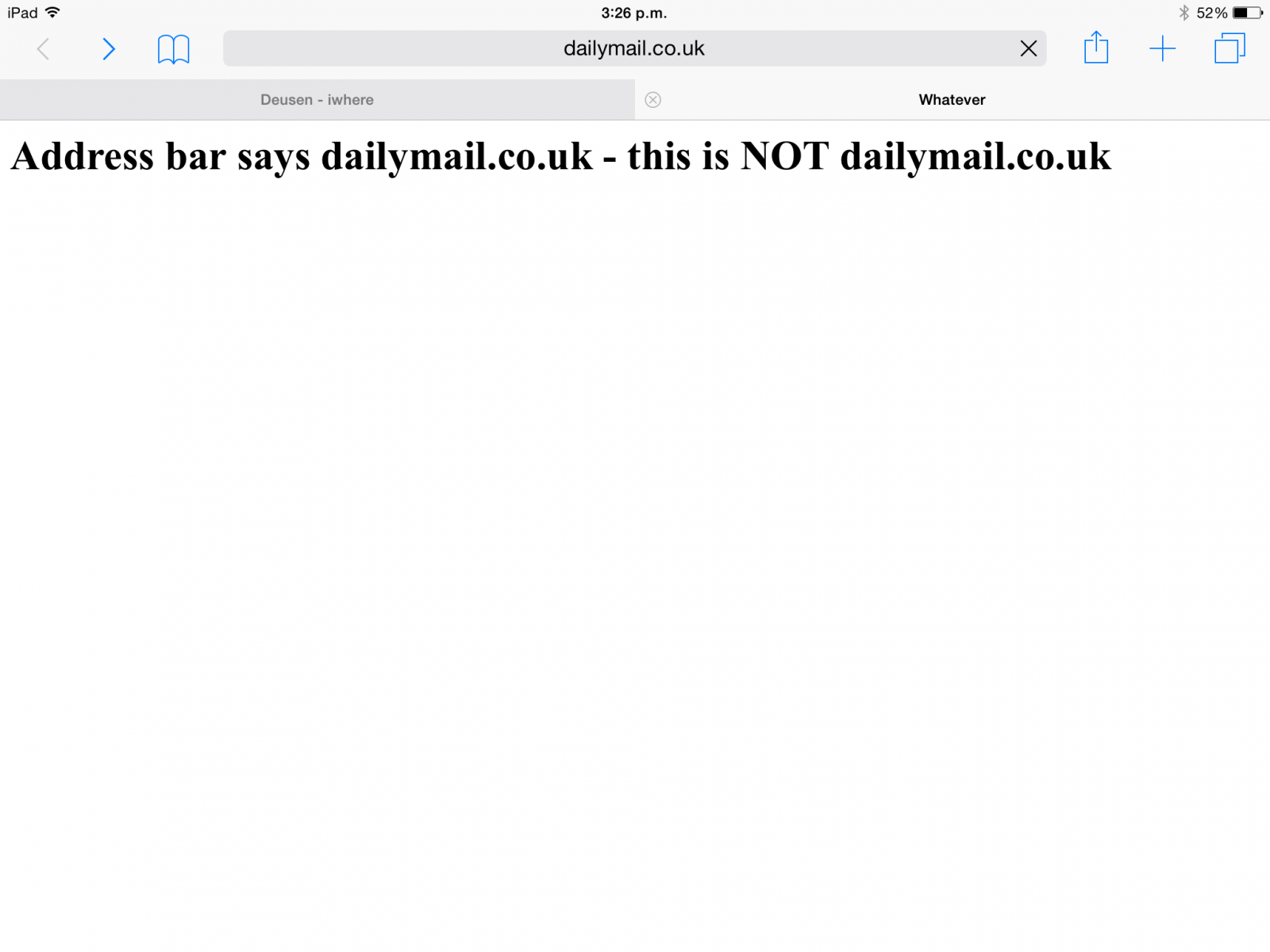
There is a proof of concept http://www.deusen.co.uk/items/iwhere.9500182225526788/. From an iPad Air 2 Safari Web Browser:
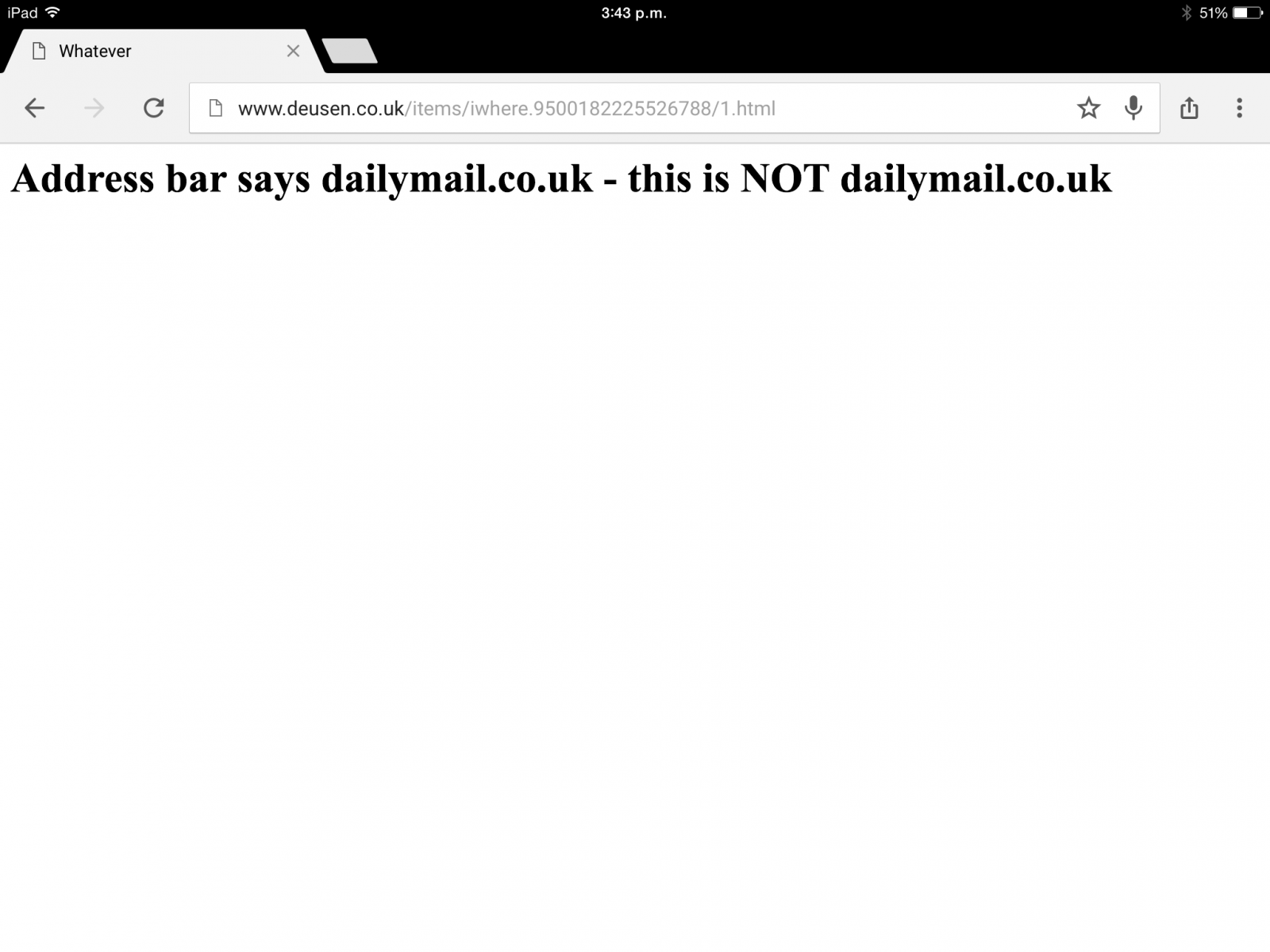
From same iPad using Google Chrome:
The code is very simple: webpage reloads every 10 milliseconds using the setInterval() function, just before the browser can get the real page and so the user sees the "real" web address instead of the fake one:
Read more: https://isc.sans.edu/forums/diary/Address+spoofing+vulnerability+in+Safari+Web+Browser/19705/
There is a proof of concept http://www.deusen.co.uk/items/iwhere.9500182225526788/. From an iPad Air 2 Safari Web Browser:

From same iPad using Google Chrome:

The code is very simple: webpage reloads every 10 milliseconds using the setInterval() function, just before the browser can get the real page and so the user sees the "real" web address instead of the fake one:
Read more: https://isc.sans.edu/forums/diary/Address+spoofing+vulnerability+in+Safari+Web+Browser/19705/