Gandalf_The_Grey
Level 83
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,256
In June-August 2021, AV-TEST carried out a test of ransomware protection offered by 11 different Endpoint Protection Platforms (EPP). In total, 113 different attacks were executed.
The three assessment scenarios were independently developed and executed by the test lab:
• Real-World ransomware attacks user files on local system
• Real-World ransomware attacks user files on remote shared folder
• Proof of Concept ransomware attacks user files on local system
During the test, the products were expected to detect ransomware activity and its files, block it, roll-back any changes to user files (the other words, to protect all user files) and eliminate the threat from the targeted system. Only these results were considered a true success and the relevant solution was given a credit in each test case.
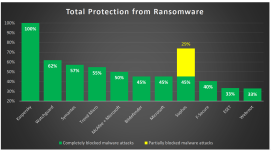
Kaspersky Endpoint Security Cloud achieved the best results, protecting against 100% of all the ransomware attacks in the test (113 in total), without loss of a single user file.
The individual results of the three scenarios revealed a difference in the detection/protection capabilities of the products being tested
Kaspersky blog post:

 www.kaspersky.com
AV-Test results in pdf:
www.kaspersky.com
AV-Test results in pdf:
The three assessment scenarios were independently developed and executed by the test lab:
• Real-World ransomware attacks user files on local system
• Real-World ransomware attacks user files on remote shared folder
• Proof of Concept ransomware attacks user files on local system
During the test, the products were expected to detect ransomware activity and its files, block it, roll-back any changes to user files (the other words, to protect all user files) and eliminate the threat from the targeted system. Only these results were considered a true success and the relevant solution was given a credit in each test case.

Kaspersky Endpoint Security Cloud achieved the best results, protecting against 100% of all the ransomware attacks in the test (113 in total), without loss of a single user file.
The individual results of the three scenarios revealed a difference in the detection/protection capabilities of the products being tested
Kaspersky blog post:

What is the most effective security solution against ransomware?
Researchers at AV-Test have established which security solution is best at dealing with ransomware.

