- Oct 23, 2012
- 12,527
The criminal group behind the Adwind RAT, one of the most actively deployed remote access trojans, has rebranded its product once again, this time returning to the malware market with the name of JBifrost.
This particular malware appeared in January 2012, under the name of Frutas RAT, and the following year, in January 2013, it rebranded as the Adwind RAT, a moniker that would stick with all security vendors.
As malware campaigns and the RAT's activity were exposed across the years, the crooks would always change the malware's name time and time again. Adwind rebranded as the Unrecom RAT in February 2014, as AlienSpy in October 2014, and as JSocket RAT in June 2015.
JSocket shuts down, and JBifrost appears three months later
After a scorching in-depth report published by Kaspersky in February 2016, the latest incarnation of this RAT known as JSocket shut down soon after.
According to researchers from security vendor Fortinet, the people behind Adwind have gone through the old motions of rebranding their product once again, which, three months later, reappeared on the market on May 15, 2016, as the JBifrost RAT.
Fortinet researchers are 100 percent positive this is a rebranded Adwind RAT, with a new GUI, and only a small set of new features when compared with its previous reincarnation, JSocket.
Adwind (JBifrost) website is now a closed community
The JBifrost website is not available to anyone anymore, and unlike previous instances where anyone could buy the RAT, users now need an invitation code to register on the JBifrost website and purchase the RAT.
This particular malware appeared in January 2012, under the name of Frutas RAT, and the following year, in January 2013, it rebranded as the Adwind RAT, a moniker that would stick with all security vendors.
As malware campaigns and the RAT's activity were exposed across the years, the crooks would always change the malware's name time and time again. Adwind rebranded as the Unrecom RAT in February 2014, as AlienSpy in October 2014, and as JSocket RAT in June 2015.
JSocket shuts down, and JBifrost appears three months later
After a scorching in-depth report published by Kaspersky in February 2016, the latest incarnation of this RAT known as JSocket shut down soon after.
According to researchers from security vendor Fortinet, the people behind Adwind have gone through the old motions of rebranding their product once again, which, three months later, reappeared on the market on May 15, 2016, as the JBifrost RAT.
Fortinet researchers are 100 percent positive this is a rebranded Adwind RAT, with a new GUI, and only a small set of new features when compared with its previous reincarnation, JSocket.
Adwind (JBifrost) website is now a closed community
The JBifrost website is not available to anyone anymore, and unlike previous instances where anyone could buy the RAT, users now need an invitation code to register on the JBifrost website and purchase the RAT.
Crooks are selling JBifrost as a monthly subscription, $45 for the first month and $40 for a subscription renewal.
Another big change in how the crooks operate is in how they collect their money. Previously, they accepted payments via PerfectMoney, CoinPayments, Advcash, EntroMoney, and Bitcoin.
This time around, they only take Bitcoin, most likely because the other payment methods are not anonymous and may lead law enforcement back to the crooks.
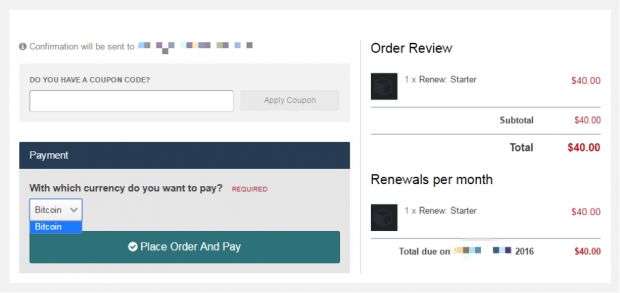
Bifrost Bitcoin-only payment options
Taking into account Kaspersky's long-standing cooperation with law enforcement agencies around the world, the Adwind gang seems to be legitimately scared and have taken precautions to hide their operations like never before.
JBifrost comes with minimal changes compared to Adwind
As for the JBifrost changes compared to JSocket, Fortinet said it detected only minor changes that include a new column that shows an infected victim's keyboard status (in use or not), and a new column that shows the title of the victim's current window.
There is also a new tab called Misc that allows users to configure additional JBifrost servers, as well as a new feature that lets attackers grab data from web forms displayed inside the Google Chrome browser.
At the time of its analysis, Fortinet says the JBifrost malware had been downloaded from the homepage 1,566 times, and that it has been detected in live malware distribution campaigns.
"Based on our findings, it is clear that Adwind perpetrators intend to stay in business by simply rebranding their RAT whenever they appear in the news. They do so by migrating their current subscribers’ accounts to a new website," Fortinet's Rommel Joven and Roland Dela Paz note. "As of this writing, we can confirm that JBifrost RAT is currently being utilized in active attacks, including attacks related to business email compromise (BEC) schemes."
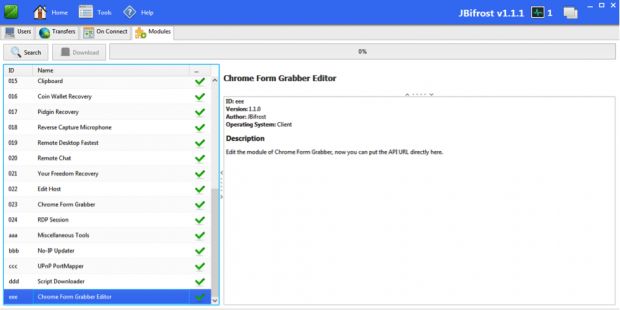
Bifrost Chrome form grabber feature