silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,743
- 123,908
- 8,399
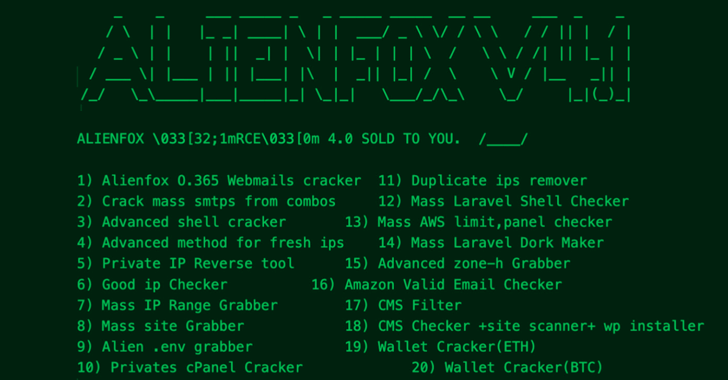
A new "comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers.
"The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.
The cybersecurity company characterized the malware as highly modular and constantly evolving to accommodate new features and performance improvements.
AlienFox Malware Targets API Keys and Secrets from AWS, Google, and Microsoft Cloud Services
AlienFox, a highly modular & constantly evolving toolset distributed on Telegram, enables attackers to harvest API keys & secrets from cloud services.
Executive Summary
- SentinelLabs analyzed several iterations of “AlienFox,” a comprehensive toolset for harvesting credentials for multiple cloud service providers.
- Attackers use AlienFox to harvest API keys & secrets from popular services including AWS SES & Microsoft Office 365.
- AlienFox is a modular toolset primarily distributed on Telegram in the form of source code archives. Some modules are available on GitHub for any would-be attacker to adopt.
- The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for cryptomining, in order to enable and expand subsequent campaigns.
- Along with our thorough analysis of different AlienFox iterations, we provide a full list of indicators of compromise, YARA rules, and recommendations in the full report.
Dissecting AlienFox | The Cloud Spammer’s Swiss Army Knife
A sophisticated new toolset is being used to harvest credentials from multiple cloud service providers, including AWS SES and Microsoft Office 365.