A new Trojan designed for Android takes advantage of the new security features introduced in Android Marshmallow, and utilizes a little social engineering to fool its victims and steal banking details.
Named 'Trojan-Banker.AndroidOS.Gugi.c' or simply 'Gugi,' its gimmick starts by posing as a spam message, which reads:
"Dear user, you receive MMS-photo! You can look at it by clicking on the following link."
If a recipient clicks on the link, it will begin downloading Guci onto the device.
The file downloaded will be named "img67123987.jpg." The file poses itself as a digital image, as it is after all pretending to be an MMS message downloaded. At this point, those who are not very knowledgeable about Android security will unmindfully install the file, in order to view the purported message. In reality, the malware is starting to warm itself up.
Upon opening the app, users will be prompted with a window asking for 'additional rights,' with only one button 'provide.' If tapped, they will be led to a page that will authorize the app overlay.
In Android Marshmallow, apps have to request a permission to overlay itself over others, as a security measure to protect users from phishing and ransomware attacks.
Named 'Trojan-Banker.AndroidOS.Gugi.c' or simply 'Gugi,' its gimmick starts by posing as a spam message, which reads:
"Dear user, you receive MMS-photo! You can look at it by clicking on the following link."
If a recipient clicks on the link, it will begin downloading Guci onto the device.
The file downloaded will be named "img67123987.jpg." The file poses itself as a digital image, as it is after all pretending to be an MMS message downloaded. At this point, those who are not very knowledgeable about Android security will unmindfully install the file, in order to view the purported message. In reality, the malware is starting to warm itself up.
Upon opening the app, users will be prompted with a window asking for 'additional rights,' with only one button 'provide.' If tapped, they will be led to a page that will authorize the app overlay.
In Android Marshmallow, apps have to request a permission to overlay itself over others, as a security measure to protect users from phishing and ransomware attacks.
Once this permission has been granted, Gugi moves on to its next step. With the ability to draw over other apps, it will now initiate a series of requests for additional permissions, by exploiting another Android Marshmallow feature, the dynamic request capability that allows apps to ask for more permission than it originally requested after they have been installed.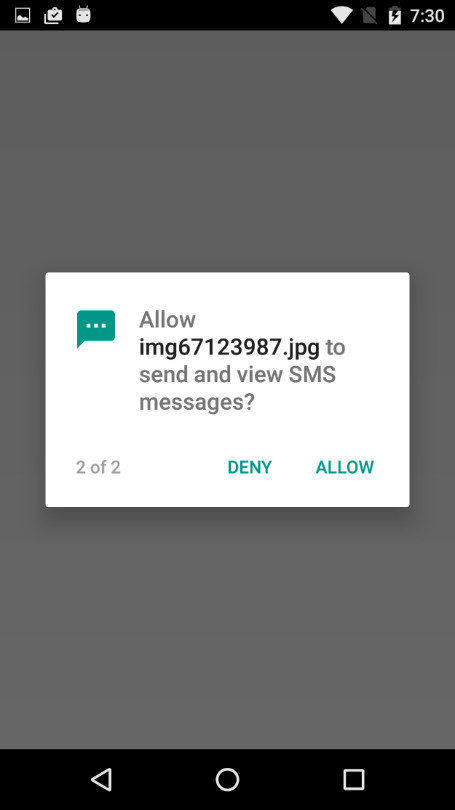
The user is given no option at this point, as the app which has now superimposed itself over other apps has only one button, named 'Activate.' On the first tap, it will request for administrative privileges. Through this, it makes it even harder to uninstall the app. It will also ask for the ability to send and view SMS and to make calls.
Should the victim of the Trojan refuse to grant even one of these requests, it will block the infected device. A victim can now only rescue the device by rebooting in safe mode to try and uninstall the Gugi Trojan.
While the Trojan is currently contained in Russia, it could always spread to other areas. At this point, we advise our readers to be careful about suspicious links and emails. Disallowing third-party devices to install on Android phones goes a long way too, to ensure that no malware can ever penetrate the device.
Source: SecureList via Bleeping Computer | Screenshot via SecureList