- Nov 10, 2017
- 3,135
- 1
- 22,994
- 4,269
Anonymous Member Arrested in Ohio
The Federal Bureau of Investigation has arrested an Ohio man on accusations of launching DDoS attacks on websites belonging to the city of Akron.
According to court documents obtained by Bleeping Computer, the man's name is James Robinson, 32, from Akron, Ohio. He went online under the pseudonym of AkronPhoenix420.
Online, Robinson posed as a member of the Anonymous hacker collective. He ran a YouTube account where he regularly published Anonymous-themed videos and a Twitter account from where he threatened, touted, and bragged about DDoS attacks and the Anonymous operations he was taking part in.
Man charged for DDoSing Akron PD, city website
While his Twitter feed lists a litany of supposed DDoS attacks, court documents filed on Thursday, May 10, reveal that US authorities have charged him with carrying out two attacks in particular —against the domains of akronohio.gov and akroncops.org, belonging to the city of Akron, Ohio.
According to court documents, the attack took place on August 1, 2017. EyeMG, the company providing the hosting for the two websites said it often changed IP addresses to skirt the attacks, but the attacker would target the new ones as well.
The DDoS attack continued until August 5, during which time the two websites "were unavailable to legitimate users."
Attacker bragged on Twitter, YouTube
Two weeks before the attacks, an account allegedly associated with Robinson uploaded a video on YouTube threating Ohio police with impeding cyber-attacks from the Anonymous collective. He then reshared the video, along with the targeted domains and their IP addresses during the attack.
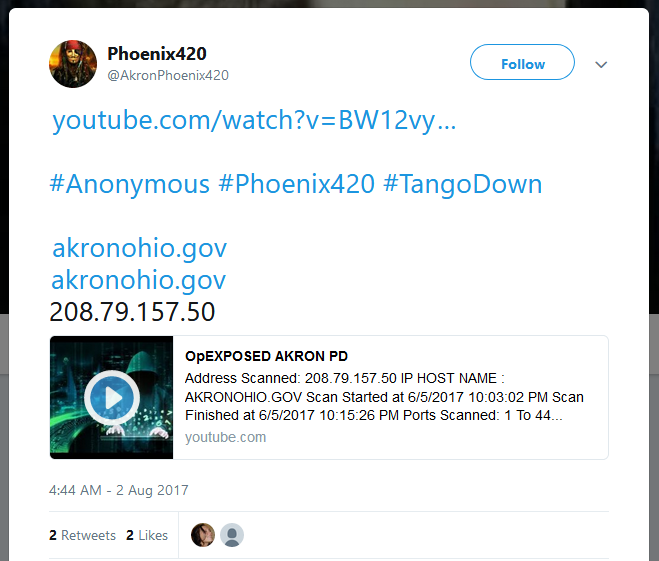
"Akron PD abuses the law," a man wearing the typical Guy Fawkes mask, a symbol of the Anonymous group, said in the video.
"This week the city of Akron experienced system failures on multiple domains including their emergency TCP ports. Akron PD thinks that by cornering anons and abusing them that they will scare anons."
Robison supposedly goes on to say that Akron PD does not care "for the safety of [their] people," launching all sorts of wild accusations.
His Twitter account is choke full of screenshots showing "evidence" of DDoS attacks against countless of US government domains, such as disa.mil, dod.gov, military.com, and others.
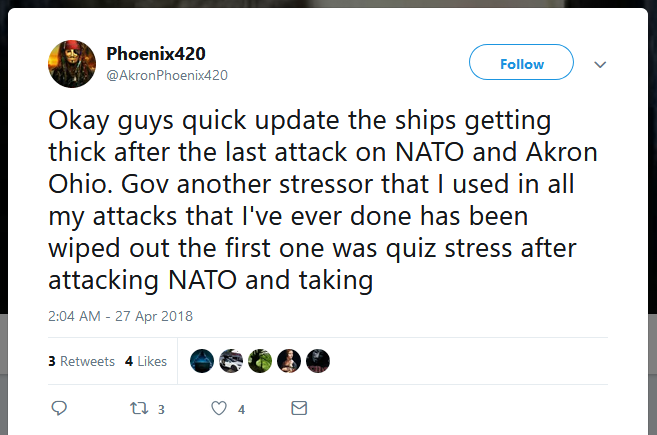
Such attacks were always tagged to appear like they were part of a bigger attack campaign named "#OpUSA." Threats and supposed attacks against Akron and government sites continued all year until days before his arrest.
OpSec mistake led to the arrest
Court documents reveal the FBI tracked down Robinson after the suspected connected to his Twitter account from his home IP address. The IP address and the mobile phone number associated with the Twitter account led investigators to Robinson.
The FBI arrested Robinson on Thursday, May 10. According to court documents, he is to be detained until May 15, pending a court hearing.
US authorities have charged the man under the Computer Fraud and Abuse Act with one count of knowingly causing the transmission of a program, information, code, and command, and as a result of such conduct, intentionally causing damage to a protected computer. He faces a maximum sentence of ten years in prison.
The Federal Bureau of Investigation has arrested an Ohio man on accusations of launching DDoS attacks on websites belonging to the city of Akron.
According to court documents obtained by Bleeping Computer, the man's name is James Robinson, 32, from Akron, Ohio. He went online under the pseudonym of AkronPhoenix420.
Online, Robinson posed as a member of the Anonymous hacker collective. He ran a YouTube account where he regularly published Anonymous-themed videos and a Twitter account from where he threatened, touted, and bragged about DDoS attacks and the Anonymous operations he was taking part in.
Man charged for DDoSing Akron PD, city website
While his Twitter feed lists a litany of supposed DDoS attacks, court documents filed on Thursday, May 10, reveal that US authorities have charged him with carrying out two attacks in particular —against the domains of akronohio.gov and akroncops.org, belonging to the city of Akron, Ohio.
According to court documents, the attack took place on August 1, 2017. EyeMG, the company providing the hosting for the two websites said it often changed IP addresses to skirt the attacks, but the attacker would target the new ones as well.
The DDoS attack continued until August 5, during which time the two websites "were unavailable to legitimate users."
Attacker bragged on Twitter, YouTube
Two weeks before the attacks, an account allegedly associated with Robinson uploaded a video on YouTube threating Ohio police with impeding cyber-attacks from the Anonymous collective. He then reshared the video, along with the targeted domains and their IP addresses during the attack.

"Akron PD abuses the law," a man wearing the typical Guy Fawkes mask, a symbol of the Anonymous group, said in the video.
"This week the city of Akron experienced system failures on multiple domains including their emergency TCP ports. Akron PD thinks that by cornering anons and abusing them that they will scare anons."
Robison supposedly goes on to say that Akron PD does not care "for the safety of [their] people," launching all sorts of wild accusations.
His Twitter account is choke full of screenshots showing "evidence" of DDoS attacks against countless of US government domains, such as disa.mil, dod.gov, military.com, and others.
Such attacks were always tagged to appear like they were part of a bigger attack campaign named "#OpUSA." Threats and supposed attacks against Akron and government sites continued all year until days before his arrest.

OpSec mistake led to the arrest
Court documents reveal the FBI tracked down Robinson after the suspected connected to his Twitter account from his home IP address. The IP address and the mobile phone number associated with the Twitter account led investigators to Robinson.
The FBI arrested Robinson on Thursday, May 10. According to court documents, he is to be detained until May 15, pending a court hearing.
US authorities have charged the man under the Computer Fraud and Abuse Act with one count of knowingly causing the transmission of a program, information, code, and command, and as a result of such conduct, intentionally causing damage to a protected computer. He faces a maximum sentence of ten years in prison.
