- Jul 22, 2014
- 2,525
....
SandboxEscaper, a researcher who back in August tweeted out a Windows privilege escalation bug, has published another unpatched Windows flaw on Twitter.
The new bug has some similarities to the previous bug. Windows services usually run with elevated privileges. Sometimes they perform actions on behalf of a user, and to do this they use a feature called impersonation. These services act as if they were using a particular user's set of privileges. After they've finished that action, they revert to their normal, privileged identity.
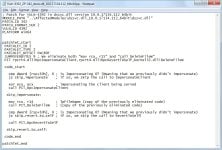
Both this bug and SandboxEscaper's previous bug depend on improper use of impersonation—specifically, the services in question (last time it was Task Scheduler, this time it's the "Data Sharing Service") revert their impersonation too quickly and end up performing some actions with elevated privileges when they should in fact have been impersonated. The last bug allowed one file to be written over another. In this case, it's a call to delete a file that is improperly impersonated, ultimately giving regular unprivileged user the ability to delete any file on the system, even those that they should have no access to.
The new bug appears to have an important timing aspect to it; two actions must happen simultaneously to make the impersonation end prematurely. SandboxEscaper says that because of this, exploitation on a single core machine seems unlikely, but multicore machines are vulnerable. SandboxEscaper's proof of concept, published on GitHub, will attempt to delete Windows' PCI driver. As such, we wouldn't recommend running it on any system that you care about because it's not going to be able to boot once that file has been removed.
....
SandboxEscaper, a researcher who back in August tweeted out a Windows privilege escalation bug, has published another unpatched Windows flaw on Twitter.
The new bug has some similarities to the previous bug. Windows services usually run with elevated privileges. Sometimes they perform actions on behalf of a user, and to do this they use a feature called impersonation. These services act as if they were using a particular user's set of privileges. After they've finished that action, they revert to their normal, privileged identity.
Both this bug and SandboxEscaper's previous bug depend on improper use of impersonation—specifically, the services in question (last time it was Task Scheduler, this time it's the "Data Sharing Service") revert their impersonation too quickly and end up performing some actions with elevated privileges when they should in fact have been impersonated. The last bug allowed one file to be written over another. In this case, it's a call to delete a file that is improperly impersonated, ultimately giving regular unprivileged user the ability to delete any file on the system, even those that they should have no access to.
The new bug appears to have an important timing aspect to it; two actions must happen simultaneously to make the impersonation end prematurely. SandboxEscaper says that because of this, exploitation on a single core machine seems unlikely, but multicore machines are vulnerable. SandboxEscaper's proof of concept, published on GitHub, will attempt to delete Windows' PCI driver. As such, we wouldn't recommend running it on any system that you care about because it's not going to be able to boot once that file has been removed.
....