- Nov 15, 2016
- 867
Apple Rushes to Fix MacOS High Sierra 'All Access' Bug
Serious Flaw Can Be Remotely Exploited to Gain Root Access Without a Password

Apple shipped its latest desktop operating system, High Sierra, with a massive vulnerability that allows anyone, without a password, to easily create a new "root" account that has access to all files on the computer.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
Lemi Orhan Ergin, an Agile software developer at a company called Iyzico, described the vulnerability on Tuesday in a tweet that has been widely retweeted.
"Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as 'root' with empty password after clicking on login button several times," he said.
Others, including developer Mike Myers, have since found a post to Apple's user forums on Nov. 13 that describe the same bug.
Perhaps nobody noticed two weeks ago when the root login vulnerability in macOS High Sierra was shared as a helpful tip on Apple's own Developer forums. Updated to High Sierra, all Admin accounts now ... | Apple Developer Forums pic.twitter.com/sOiRt8j2X7
— Mike Myers (@fristle) November 29, 2017
Apple says in a statement: "We are working on a software update to address this issue."
The Root of the Problem
A root account is the most powerful account on a computer because it has access to all files, says Patrick Wardle, who's the chief security researcher with crowdsourced security firm Synack as well as a former NSA analyst. That's why many security experts recommend never using root accounts, except in cases where machines must be administered. Many organizations that issue computers to employees will not give them root access to the system, instead reserving such access only for IT support teams.
Gaining access to a root account makes life easier for any attackers. For example, they could easily install a keylogger or other malware on the computer. That's why malware programs designed for MacOS often try to trick users into divulging passwords to get root access, Wardle says.
"With this privilege, you can pretty much do anything," he says.
pic.twitter.com/4TBh5NetIS
— patrick wardle (@patrickwardle) November 28, 2017
This latest authentication bug in MacOS adds to other worrying authentication-related findings in High Sierra by independent security researchers. Wardle says that brings into question whether Apple's quality assurance processes have slipped.
"I'm coming to think there really isn't a QA process," says Wardle, who has reported many bugs to Apple and has a good relationship with its security team. "I don't mean that in a negative way. I'm not trying to personally attack Apple."
It's surprising that Apple, which is one of the more privacy-focused and security-aware companies, didn't catch the bug before High Sierra shipped, says Chris Pierson, chief security officer and general counsel for payment services firm Viewpost. "It is imperative for all of us in cybersecurity to slow down and be more precise in our mastery of secure products before they hit the market," he says.
Keys to the Kingdom
On vulnerable MacOS systems, there are several ways to exploit the bug and create a root account. One way is to use "root" as the username for the "other" account in the logon screen. A user will then be prompted for a password, at which point they can enter anything.
The authentication window then appears a second time, and whatever was entered before - even if the field was left blank - unlocks the root account. The same method can be used by opening system preferences, going to users & groups and clicking the lock icon, which then displays an authentication window. It's also possible to create the account through the terminal window.
Wardle says in previous versions of MacOS, the root account is disabled. To access it, a user would be asked for the system password before granting access to root. For some reason, that protection has been disabled in High Sierra.
The bug can also be exploited remotely. In one scenario, if the targeted computer allows for remote connections, the attacker can choose in a dialog box to login as root and do the same trick, Wardle says.
String of Authentication Slip-Ups
Apple's mistake is easy to fix and just takes a couple of lines of code, Wardle says. But until a patch is distributed, users should change the root account password, which will thwart any attempts to take advantage of it.
How to Mitigate the Bug, Pending Apple's Fix
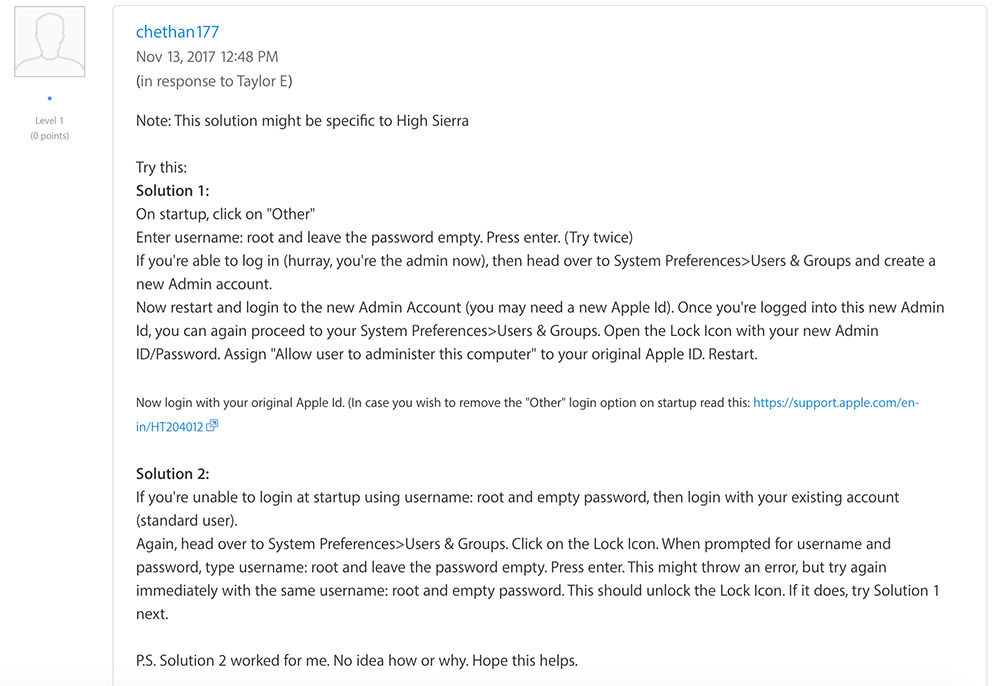
Developer Chethan Kamath, writing under the username chethan17, posted a temporary workaround for the High Sierra password flaw, pending a patch from Apple.
More broadly, Wardle says he's been surprised at Apple's slip-ups. Just prior to the release of High Sierra to the public on Oct. 31, Wardle found a major issue within Apple's password manager, which is called the Keychain (see Beware: Apple's Password Manager Has a Zero-Day Flaw).
Keychain is an encrypted container that stores a variety of authentication credentials for disk images, WiFi networks and other data, such as credit card numbers and banking PINs.
Wardle wrote proof-of-concept code that pulls those credentials in plain text without entering the system password, which is usually required to access Keychain data. A victim would have to be logged in for the attack to work. Apple has patched the bug.
The company also had to fix an issue found by Mathews Mariano of Leet Tech, which involved encrypted containers that used Apple's latest file system, APFS. The password for an encrypted container was revealed if someone clicked to get a hint for it.
Serious Flaw Can Be Remotely Exploited to Gain Root Access Without a Password

Apple shipped its latest desktop operating system, High Sierra, with a massive vulnerability that allows anyone, without a password, to easily create a new "root" account that has access to all files on the computer.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
Lemi Orhan Ergin, an Agile software developer at a company called Iyzico, described the vulnerability on Tuesday in a tweet that has been widely retweeted.
"Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as 'root' with empty password after clicking on login button several times," he said.
Others, including developer Mike Myers, have since found a post to Apple's user forums on Nov. 13 that describe the same bug.
Perhaps nobody noticed two weeks ago when the root login vulnerability in macOS High Sierra was shared as a helpful tip on Apple's own Developer forums. Updated to High Sierra, all Admin accounts now ... | Apple Developer Forums pic.twitter.com/sOiRt8j2X7
— Mike Myers (@fristle) November 29, 2017
Apple says in a statement: "We are working on a software update to address this issue."
The Root of the Problem
A root account is the most powerful account on a computer because it has access to all files, says Patrick Wardle, who's the chief security researcher with crowdsourced security firm Synack as well as a former NSA analyst. That's why many security experts recommend never using root accounts, except in cases where machines must be administered. Many organizations that issue computers to employees will not give them root access to the system, instead reserving such access only for IT support teams.
Gaining access to a root account makes life easier for any attackers. For example, they could easily install a keylogger or other malware on the computer. That's why malware programs designed for MacOS often try to trick users into divulging passwords to get root access, Wardle says.
"With this privilege, you can pretty much do anything," he says.
pic.twitter.com/4TBh5NetIS
— patrick wardle (@patrickwardle) November 28, 2017
This latest authentication bug in MacOS adds to other worrying authentication-related findings in High Sierra by independent security researchers. Wardle says that brings into question whether Apple's quality assurance processes have slipped.
"I'm coming to think there really isn't a QA process," says Wardle, who has reported many bugs to Apple and has a good relationship with its security team. "I don't mean that in a negative way. I'm not trying to personally attack Apple."
It's surprising that Apple, which is one of the more privacy-focused and security-aware companies, didn't catch the bug before High Sierra shipped, says Chris Pierson, chief security officer and general counsel for payment services firm Viewpost. "It is imperative for all of us in cybersecurity to slow down and be more precise in our mastery of secure products before they hit the market," he says.
Keys to the Kingdom
On vulnerable MacOS systems, there are several ways to exploit the bug and create a root account. One way is to use "root" as the username for the "other" account in the logon screen. A user will then be prompted for a password, at which point they can enter anything.
The authentication window then appears a second time, and whatever was entered before - even if the field was left blank - unlocks the root account. The same method can be used by opening system preferences, going to users & groups and clicking the lock icon, which then displays an authentication window. It's also possible to create the account through the terminal window.
Wardle says in previous versions of MacOS, the root account is disabled. To access it, a user would be asked for the system password before granting access to root. For some reason, that protection has been disabled in High Sierra.
The bug can also be exploited remotely. In one scenario, if the targeted computer allows for remote connections, the attacker can choose in a dialog box to login as root and do the same trick, Wardle says.
String of Authentication Slip-Ups
Apple's mistake is easy to fix and just takes a couple of lines of code, Wardle says. But until a patch is distributed, users should change the root account password, which will thwart any attempts to take advantage of it.
How to Mitigate the Bug, Pending Apple's Fix

Developer Chethan Kamath, writing under the username chethan17, posted a temporary workaround for the High Sierra password flaw, pending a patch from Apple.
More broadly, Wardle says he's been surprised at Apple's slip-ups. Just prior to the release of High Sierra to the public on Oct. 31, Wardle found a major issue within Apple's password manager, which is called the Keychain (see Beware: Apple's Password Manager Has a Zero-Day Flaw).
Keychain is an encrypted container that stores a variety of authentication credentials for disk images, WiFi networks and other data, such as credit card numbers and banking PINs.
Wardle wrote proof-of-concept code that pulls those credentials in plain text without entering the system password, which is usually required to access Keychain data. A victim would have to be logged in for the attack to work. Apple has patched the bug.
The company also had to fix an issue found by Mathews Mariano of Leet Tech, which involved encrypted containers that used Apple's latest file system, APFS. The password for an encrypted container was revealed if someone clicked to get a hint for it.