Earlier this year, BleepingComputer reported on hackers hiding malware in fake Windows error logs.
After gaining access to a Windows system and achieving persistence, the malware would read from a ".chk" file that impersonated event logs.
The apparent hexadecimal characters on the right side are actually decimal characters used to construct an encoded payload via rogue scheduled tasks.
More information has emerged on this complex malware and some other sinister tasks it carries out.
... ...
Attackers abuse Google DNS over HTTPS to download malware
- Thread starter LASER_oneXM
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
That was to be expected. DoT is a safer option, even a default DNS via port 53. I myself prefer dnscrypt, because UDP has a lower attack surface.
 www.thesslstore.com
www.thesslstore.com

 www.dnsfilter.com
www.dnsfilter.com
Paul Vixie is one of the architects of DNS. And given the subject, his opinion bears considerable weight. Over the weekend he responded to Nick Sullivan, the head of crypto at Cloudflare’s Twitter announcement about RFC 8484 (DNS over HTTPS) by voicing his opposition:
RFC 8484 is a cluster duck for internet security. Sorry to rain on your parade. The inmates have taken over the asylum.

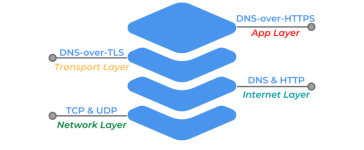
What is the difference between DNS over TLS & DNS over HTTPS?
While at first glance it might be easy to mistake DNS over TLS and DNS over HTTPS for the same thing. But there's one very controversial difference.
The main difference between DoT and DoH are the layers at which the encryption is enabled.
DNS-over-HTTPS is applied at the application layer (two layers removed from the Internet layer)
while DNS-over-TLS is applied at the transport layer (one layer removed from the Internet layer).


DNS over TLS vs. DNS over HTTPS | DNSFilter
Explore the differences between DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) to make an informed choice for DNS encryption in 2024.
I think you are mistaken on this thing, it is not about the malware hacking/intercepting/eavesdropping DOH traffic but the malware on the system (which was already present there) did used the doh ( encrypted port 443) to evade detection of packet inspection mechanisms on the company's security server. Any application on the system can use doh to query the net, there is nothing wrong in it. There is no mention in the article that the application (malware) did a man in the middle attack upon the encrypted doh traffic to google.That was to be expected. DoT is a safer option, even a default DNS via port 53. I myself prefer dnscrypt, because UDP has a lower attack surface.
See the url was inside the powershell code, the code then used doh service to query a bad server to download the payload. So there is nothing wrong with DOH, it is as safe as Dot.While revisiting the malware sample, researchers at MSP threat detection provider Huntress Labs noticed a suspicious URL in the PowerShell code they had previously analyzed:
The suspicious domain "jqueryupdatejs.com" immediately caught the attention of John Hammond, Senior Security Researcher at Huntress Labs.
That is a part of it, but it still applies. DoH is another vulnerable app, similar to dns cache. This attack is pretty much like dns poisoning, but with bonus TCP.it is not about the malware hacking/intercepting/eavesdropping DOH traffic but the malware on the system
Attackers love to hide in encrypted traffic, a point reiterated by the recent Magecart attacks.
If you look at it that way, every dns query service is vulnerable including dot and dnscrypt, it is just a matter of changing the code,That is a part of it, but it still applies. DoH is another vulnerable app, similar to dns cache. This attack is pretty much like dns poisoning, but with bonus TCP.
for example, if you change this code "https://dns.google.com/resolve?name=dmarc.jqueryupdatejs.com&type=txt" to tls://"your tls resolver".... then the query will go through port 853.In an already compromised system, nothing is safe, neither doh, dot nor dnscrypt. But for any clean system, doh or dot or dnscrypt is safer than unencrypted dns traffic, as there is less of a chance to have a man in the middle attack. DNS poisoning on doh is extremely difficult to do. You need a pretty good device to decrypt and re encrypt the traffic, but if the receiver has doh certificate verification enabled, the man in middle attack gets failed.
Last edited:
You can limit exposure with a firewall. DoH - all traffic to 443 is allowed, unconditionally. DoT/dnscrypt - you can use a firewall to allow only DNS servers.In an already compromised system, nothing is safe, neither doh, dot nor dnscrypt.
On an already compromised system, firewall is the last line of defense. Sure it can be bypassed, but it is an additional layer, that can help to prevent a payload.
Even if you don't use doh, you can't block traffic to port 443, it is used by system to send all https traffic, if you block it you will be saying goodbye to all https websites. What is the use of only allowing traffic to dns servers, if the server itself returns a malware infested website address? I think you are still not getting the point, if your system is compromised and dns queries are made to a server which supports encrypted dns, your firewall can't decrypt the qurey and filter it be it doh or TLS, that is the beauty of encryption. So the best way is to not get infected at all.You can limit exposure with a firewall. DoH - all traffic to 443 is allowed, unconditionally. DoT/dnscrypt - you can use a firewall to allow only DNS servers.
On an already compromised system, firewall is the last line of defense. Sure it can be bypassed, but it is an additional layer, that can help to prevent a payload.
You may also like...
-
Malware Analysis Discord Token Stealer Distributed as Fake Java Game
- Started by Trident
- Replies: 5
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23
-
Serious Discussion The Necessity of Simulating the Full Malware Infection Chain for Security Suite Testing
- Started by harlan4096
- Replies: 3
-
Serious Discussion Deep Research: McAfee GTI, JTI, Artemis and Other Technologies Explained
- Started by Trident
- Replies: 2
-
ESET repports that OilRig’s persistent attacks using cloud service-powered downloaders
- Started by Lymphocyte
- Replies: 0
