A new security feature added in macOS High Sierra (10.13) named "Secure Kernel Extension Loading" (SKEL) can be bypassed to allow the loading of malicious kernel extensions.
Just like Linux and Windows, macOS allows applications to load third-party kernel extensions whenever they need to perform actions that require access to lower levels of the operating system.
SKEL improves the kernel extension loading process
Developers who want to load kernel extensions (KEXT files) during their app installation process need to sign the kernel extension with a special kernel code-signing certificate, which Apple has been very careful to whom it issues.
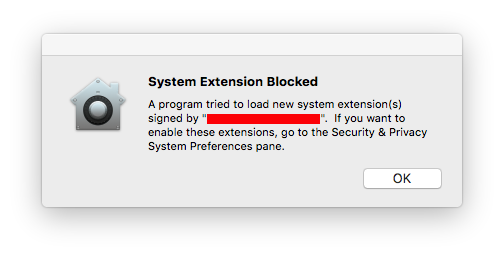
Apple's soon-to-be-released macOS High Sierra introduces the SKEL feature to improve the security of the KEXT loading process. SKEL works by showing a popup like the one pictured below whenever apps try to load kernel extensions.
The popup does not trigger for a few applications known to come from trusted developers, and a few other edge cases detailed in Apple's SKEL documentation page
here.
SKEL bypassed before High Sierra release
At a quick glance, macOS users would be satisfied with Apple's efforts to improve the security of its operating system by deploying SKEL.
The same thing cannot be said for Patrick Wardle, a well-known Apple security researcher and Chief Security Researcher at Synack.
Wardle claims that Apple's recently launched SKEL system "merely hampers the efforts of the ‘good guys’ (i.e. 3rd-party macOS developers such as those that design security products)."
The researcher claims that "due to flaws in its implementation, the bad guys (hackers/malware) will likely remain unaffected" by SKEL's intended protection measures.