Evjl's Rain
Level 47
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
- Apr 18, 2016
- 3,684

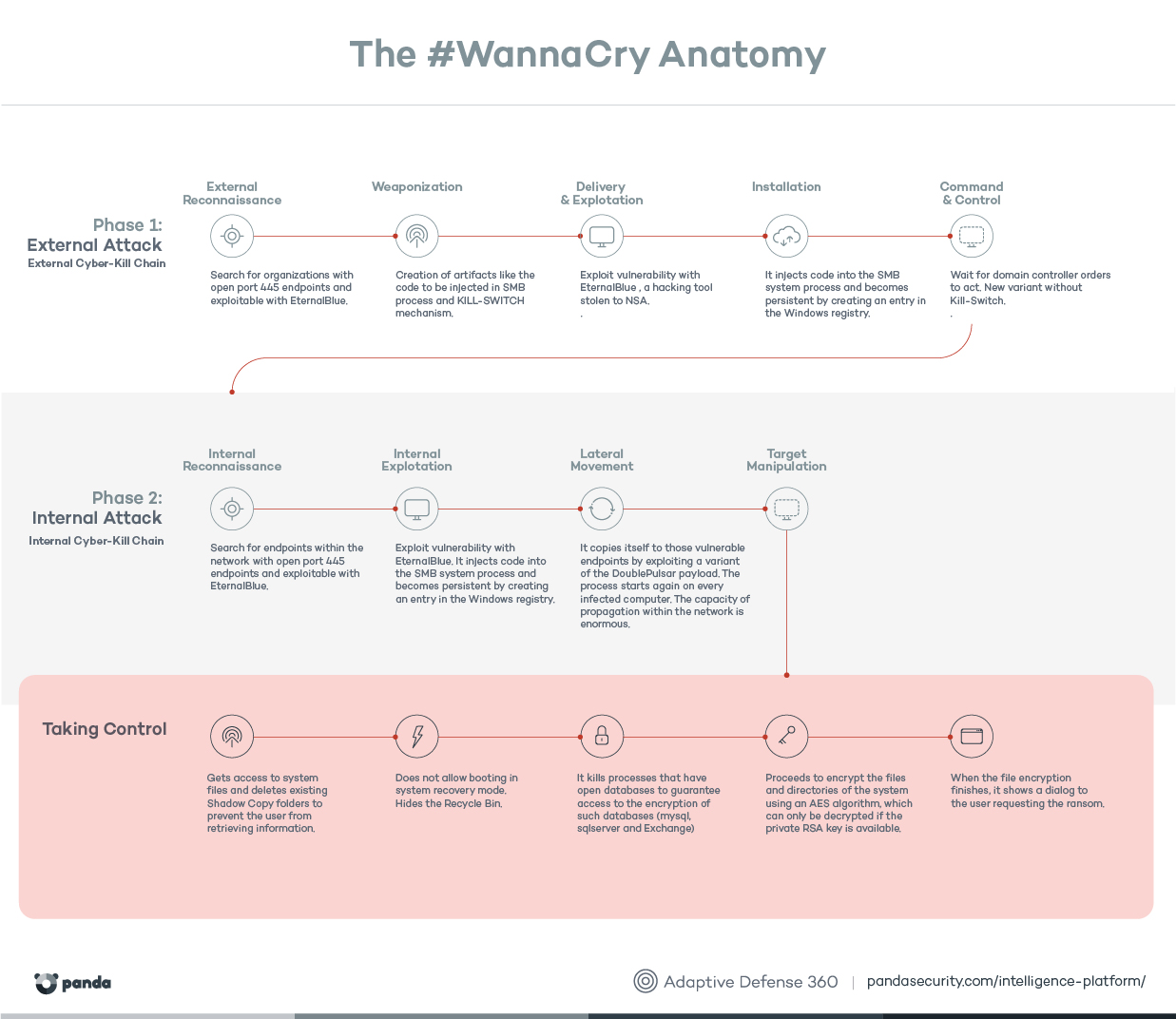
The WannaCry ransomware has been a major news story over the last few days. It has infected hundreds of thousands of computers worldwide (mostly in Russia), including some well-known companies and institutions. All the programs in our public Main Test Series now detect the WannaCry malware samples by means of signatures, but we decided to find out which of these programs would have blocked the malware proactively, i.e. before the the outbreak started and the malware samples became known. We ran a proactive protection test, i.e. we used vulnerable Windows 7 systems with definitions prior to May 12th. A WannaCry malware sample was then executed on offline systems. The list below shows which of the tested programs would have protected the system, and which did not.
As can be seen above, a majority of these products protected against this ransonware, but over 200,000 systems worldwide were compromised by it nonetheless. New variants might appear, and results for the next outbreak could look different. Users are advised to keep their systems patched, enable AV protection (i.e. do not disable features) and keep it up-to-date, as well as practising safe computing.