I'm curious about your perspective on the methodologies. What did you think of their approach?AVLab test not to be considered.
Why not to be considered?
View attachment 290441View attachment 290442View attachment 290443

Results in November 2024 » AVLab Cybersecurity Foundation
The latest results of the Advanced In-The-Wild-Malware Test, in which we regularly evaluate software designed to protect devices.avlab.pl
App Review AV test #5 - underrated Emsisoft vs recent malware
- Thread starter Khushal
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
- Content created by
- rifteyy
I am not an expert, but whichever methodology yielding such absurd results (MD scoring higher than Bitdefender internet security and ESET smart security premium) has to be questioned.I'm curious about your perspective on the methodologies. What did you think of their approach?
Any reputable AV is fine if you prefer not to use MS Defender, and Emsisoft is certainly one of them. Please remember to stay safe, not paranoid! 


When evaluating these kinds of results, I've found it's crucial to first understand the methodologies used in the tests themselves.I am not an expert, but whichever methodology yielding such absurd results (MD scoring higher than Bitdefender internet security and ESET smart security premium) has to be questioned.
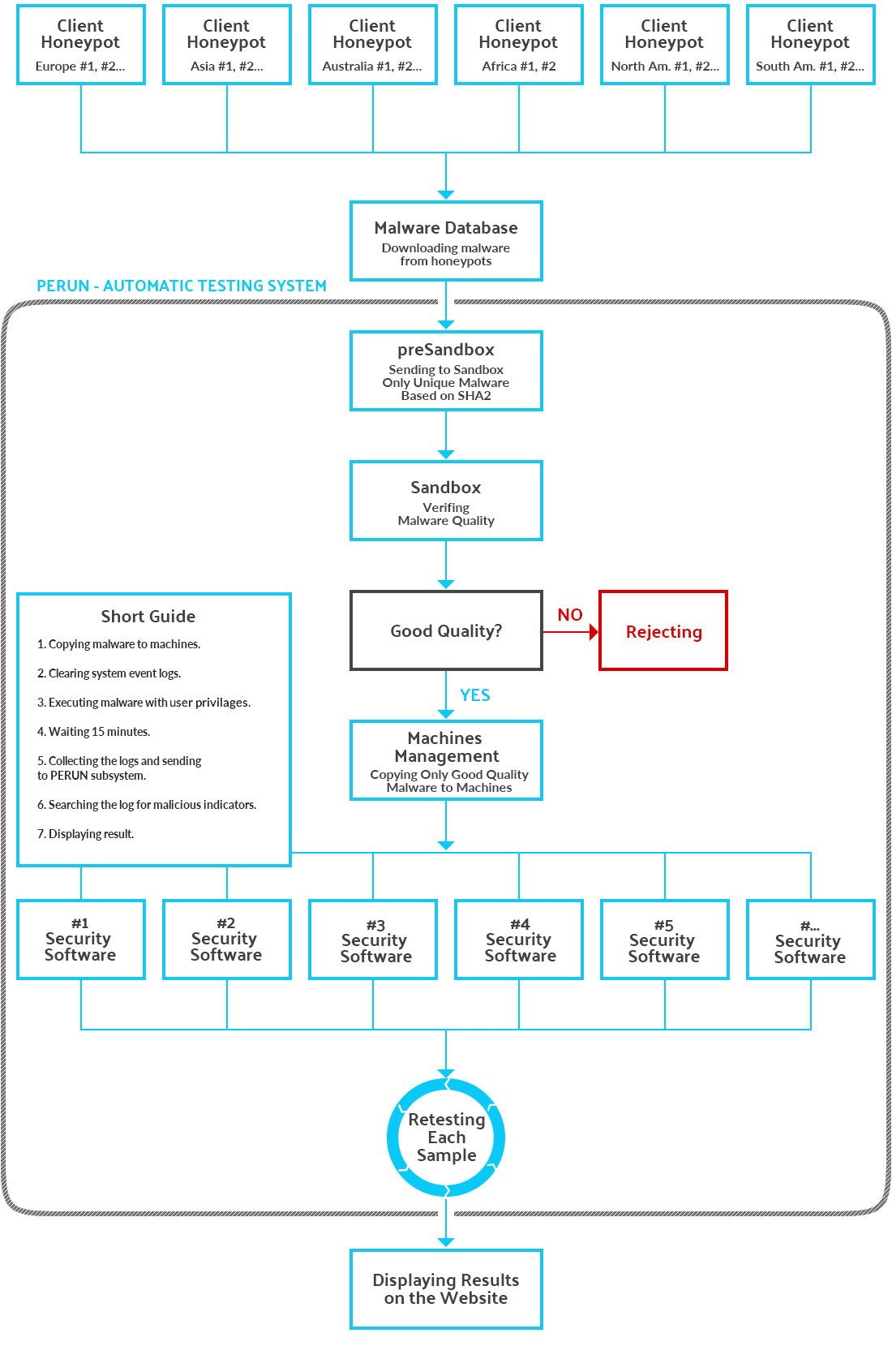
Methods of carrying out automatic tests » AVLab Cybersecurity Foundation
Question - What does the name of the "Advanced In-The-Wild Malware Test" mean?
When I get a research for reviewing before publication, even if the methods section is well-written, if the results look far from logic, I have to ask myself if the method was applied as presented or not? Is there any data fabrication or falsification or not?When evaluating these kinds of results, I've found it's crucial to first understand the methodologies used in the tests themselves.

Methods of carrying out automatic tests » AVLab Cybersecurity Foundation
Question - What does the name of the "Advanced In-The-Wild Malware Test" mean?avlab.pl
Over the decades there have been many, many unfounded conspiracy claims that the labs do not perform unbiased testing. Except for one particular case, I don't think it is a system problem with the AV Test Lab industry. To a large extent, AV lab tests are for marketing purposes. Their intent is not to fully pentest each software at default and advanced configurations and do the utmost to destroy the security solution. That sort of thing is left to privately funded pentesting engagements.When I get a research for reviewing before publication, even if the methods section is well-written, if the results look far from logic, I have to ask myself if the method was applied as presented or not? Is there any data fabrication or falsification or not?
Some people take exception to the fact that vendors that participate can challenge results, and have some of them reversed.
More likely it is the AV publishers that are up to no good by submitting modified products intended to "game" or "cheat code" the test. A few Chinese AVs got caught doing that. Then there are AVs that do underhanded stuff to suppress test results.

CrowdStrike, Symantec, ESET Face Lawsuit Over Product Testing
NSS Labs says the companies conspired to hamper independent reviews of their antivirus products. CrowdStrike, ESET and Symantec, are dismissing the allegations as baseless.
As far as AVLab.pl - @Adrian Ścibor and his staff work really hard to make their testing unbiased, accurate, and reliable for both the vendors and end users. Out of all the people that I know at AV test labs, I trust @Adrian Ścibor the most. The model he adopted essentially eliminates undue influence by software publishers while giving the publishers that disagree with the results a chance to make their case. I've never seen @Adrian Ścibor make unfair or underhanded decisions.
The quest of chasing the AV that will save one from all things. The one that is perfect with no bugs - ever. That no Youtube tester can show fails to protect. That achieves 100% protection from any AV test lab for any test methodology or test scenario.Any reputable AV is fine if you prefer not to use MS Defender, and Emsisoft is certainly one of them. Please remember to stay safe, not paranoid!
F
ForgottenSeer 94738
I think you misunderstood Shadowra. I assume his comment about AV-Comparatives, AV-TEST, was meant jokingly. Notice his smile.I understand your preference for AVLab's testing. They are indeed an excellent lab, and their focus on 'Living off the Land Binaries' (LOLBins) and live threats makes their tests very insightful. I completely agree that they are a reliable source.
However, the major testing labs that you've dismissed—AV-Comparatives, AV-TEST, are considered the industry standard for a reason, and it comes down to their methodology.
(Corrected text)
Last edited by a moderator:
Shadowra is a male and I did not misunderstand him.I think you misunderstood Shadowra. I assume her comment about AV-Comparatives, AV-TEST, was meant jokingly. Note her smile.
I am not the expert; @Shadowra is; you may discuss the shortcoming of the test with the tester.
That GDI malware was skidware and on my test VM it did not overwrite the MBR.
Given all this, Emsisoft will undergo retesting in September, and we'll see what it can (or can't) do
The effectiveness of Emsisoft depends upon the configuration. The Behavior Blocker has to be set to "Alert" - and the user has to be able to effectively respond to the alerts - in order to prevent certain types of malicious actions - particular scripts. Same with GDI and similar malware.Given all this, Emsisoft will undergo retesting in September, and we'll see what it can (or can't) do
At default settings, if you use script and similar malware, your test results will be the same - assuming that you use the same script malwares but different variants that are FUD.
Unless someone takes the time to report and work with Emsisoft support - giving them the exact malware so that they can replicate, it will not know about the problem and therefore the issues will not be fixed.
The effectiveness of Emsisoft depends upon the configuration. The Behavior Blocker has to be set to "Alert" - and the user has to be able to effectively respond to the alerts - in order to prevent certain types of malicious actions - particular scripts. Same with GDI and similar malware.
At default settings, if you use script and similar malware, your test results will be the same - assuming that you use the same script malwares but different variants that are FUD.
Unless someone takes the time to report and work with Emsisoft support - giving them the exact malware so that they can replicate, it will not know about the problem and therefore the issues will not be fixed.
Except that I don't change Emsisoft's settings unless asked to
PRO TIP
If you want to measure the average RAM and CPU load of processes such as Emsisoft accurately:
1. Locate before all Emsisoft processes and make a note of them.
2. Run PERF MON (performance monitor by Microsoft): Windows Performance Monitor Overview | Microsoft Community Hub
3. Right Click --> Add new Counter:
- select “Processes” in the general tab on the left
- select Emsisoft's processes --> add to the right column
- OK, then click “properties” on the main graph --> select sampling and values (minimum, maximum, average)
- for each process, you will have a graph and a line
Then, you can see for example an average CPU load during e.g. full system scanning.
Sorry for the screen in Polish lang!
Use this useful tool instead of other commercial ones. You need to learn something about processes and CPUs in this software, but check the documentation/manual
I may have mixed something up with the PerfMon, but I noticed an interesting post about performance, RAM, and CPUs/cores load
In MY opinion:
Resource usage on PC1 is not equal to that on PC2, because the software itself manages resource availability and can consume more or less CPU time, RAM, and disk load. Therefore, I consider performance tests to be very general, inaccurate, and not very well suited to modern machines with very different configurations. At the same time, the so-called AV SYSTEM SLOWDOWN can still slow down a power machine. This is more of a general principle than a rule.

If you want to measure the average RAM and CPU load of processes such as Emsisoft accurately:
1. Locate before all Emsisoft processes and make a note of them.
2. Run PERF MON (performance monitor by Microsoft): Windows Performance Monitor Overview | Microsoft Community Hub
3. Right Click --> Add new Counter:
- select “Processes” in the general tab on the left
- select Emsisoft's processes --> add to the right column
- OK, then click “properties” on the main graph --> select sampling and values (minimum, maximum, average)
- for each process, you will have a graph and a line
Then, you can see for example an average CPU load during e.g. full system scanning.
Sorry for the screen in Polish lang!
Use this useful tool instead of other commercial ones. You need to learn something about processes and CPUs in this software, but check the documentation/manual
I may have mixed something up with the PerfMon, but I noticed an interesting post about performance, RAM, and CPUs/cores load
In MY opinion:
Resource usage on PC1 is not equal to that on PC2, because the software itself manages resource availability and can consume more or less CPU time, RAM, and disk load. Therefore, I consider performance tests to be very general, inaccurate, and not very well suited to modern machines with very different configurations. At the same time, the so-called AV SYSTEM SLOWDOWN can still slow down a power machine. This is more of a general principle than a rule.
Most computers today come with at least 16 and 32 GB of RAM. Consuming 800-900 MB of RAM shouldn't be a problem. I use G Data antivirus. It's no different from Emsisoft. It consumes a lot of RAM because it uses Bitdefender SDK. Of course, it would be great if they consumed less RAM. But that shouldn't be a big problem these days.
For its most effective and comprehensive response, a modern security suite like Emsisoft relies on the specific triggers and context provided by a true route of infection.The effectiveness of Emsisoft depends upon the configuration. The Behavior Blocker has to be set to "Alert" - and the user has to be able to effectively respond to the alerts - in order to prevent certain types of malicious actions - particular scripts. Same with GDI and similar malware.
At default settings, if you use script and similar malware, your test results will be the same - assuming that you use the same script malwares but different variants that are FUD.
Unless someone takes the time to report and work with Emsisoft support - giving them the exact malware so that they can replicate, it will not know about the problem and therefore the issues will not be fixed.
Think of your security software as a detective investigating a crime.
The Flawed Test (Malware Zoo)
Running malware from a zip file is like giving the detective only the murder weapon. They can analyze the weapon itself (the file signature) and might identify it as dangerous. However, they have no context about how it got there, who used it, or what their initial plan was. The software is forced to make a decision based on very limited, last-second evidence.
The Real-World Attack
A true infection route provides the detective with the entire story. They see the suspect breaking in the door (the web protection blocking a malicious URL), sneaking down the hall (a Word document launching a script via exploit prevention), and then pulling out the weapon (the behavior blocker catching the final payload).
This sequence of events provides crucial context. A program like Microsoft Word launching PowerShell is a massive red flag and a powerful trigger for the Behavior Blocker. It can intervene right there, recognizing that this chain of events is illegitimate, often before the final malicious file even runs. Without that context, it only sees the final file running, which gives it far less information and less opportunity to act preemptively.
So, while it can still catch the malware at the very last stage with its file scanner, its most intelligent and proactive layers are "activated" by the suspicious sequence of events that only a real-world attack provides.
The only way to determine accurately and fully Emsisoft's Behavior Blocker capabilities is not to use files with MotW. The Emsi BB is not dependent upon MotW being present. So if the BB fails to handle specific malware with no ADS MotW (or those with it) it proves the BB is not effective against the malware.For its most effective and comprehensive response, a modern security suite like Emsisoft relies on the specific triggers and context provided by a true route of infection.
Think of your security software as a detective investigating a crime.
The Flawed Test (Malware Zoo)
Running malware from a zip file is like giving the detective only the murder weapon. They can analyze the weapon itself (the file signature) and might identify it as dangerous. However, they have no context about how it got there, who used it, or what their initial plan was. The software is forced to make a decision based on very limited, last-second evidence.
The Real-World Attack
A true infection route provides the detective with the entire story. They see the suspect breaking in the door (the web protection blocking a malicious URL), sneaking down the hall (a Word document launching a script via exploit prevention), and then pulling out the weapon (the behavior blocker catching the final payload).
This sequence of events provides crucial context. A program like Microsoft Word launching PowerShell is a massive red flag and a powerful trigger for the Behavior Blocker. It can intervene right there, recognizing that this chain of events is illegitimate, often before the final malicious file even runs. Without that context, it only sees the final file running, which gives it far less information and less opportunity to act preemptively.
So, while it can still catch the malware at the very last stage with its file scanner, its most intelligent and proactive layers are "activated" by the suspicious sequence of events that only a real-world attack provides.
Much malware is spread via shared infected USB flash drives which remove MotW.
So using malware that has no ADS MotW is not entirely invalid.
Well that (default configuration) is not going to work against certain malware types whether or not they have ADS MotW or not.Except that I don't change Emsisoft's settings unless asked to(the only thing I allow myself to do is set the AV engine to Paranoid because it's more responsive, and I set the interface to Dark Mode, otherwise my eyes hurt).
The focus needs to shift from just the 'mark of the web' to the actual behavioral triggers I described. Those are the conditions that must be met.The only way to determine accurately and fully Emsisoft's Behavior Blocker capabilities is not to use files with MotW. The Emsi BB is not dependent upon MotW being present. So if the BB fails to handle specific malware with no ADS MotW (or those with it) it proves the BB is not effective against the malware.
Much malware is spread via shared infected USB flash drives which remove MotW.
So using malware that has no ADS MotW is not entirely invalid.
I don't disagree with you, but AMSTO is never going to adopt those conditions due to complexity and expense of effort required. As far as Youtube testers, they're never going to do it. Oh, it's easy enough to write a script, Office macro, short-cut file, etc to perform a download or spawn child processes - but only a few such testers are capable or willing to do it.The focus needs to shift from just the 'mark of the web' to the actual behavioral triggers I described. Those are the conditions that must be met.
For the Emsisoft Behavior Blocker most of that will not matter, which is part of the point. It is a HIPS style behavior blocker that monitors for certain generic actions. In my own testing, if Emsisoft does not prevent the download or block the first stage file, in a significant % of instances the behavior blocker will fail to stop malware from infecting a system even when the user responds to the manual BB alert with "Block Always" or "Block Once."
In some respects, the Emsisoft Behavior Blocker is a lot like the old SpyShelter HIPS. While it was rare for SpyShelter HIPS to stop a malware infection when the user chose "Terminate (the process)" (the correct choice in all cases), it did not prevent many infections when the user selected "Block (the process action)." Even when selecting "Block Always," which is the equivalent of the "Terminate" within old SpyShelter, the Emsisoft BB often failed. The Emsisoft BB is not at the same level as Kaspersky's System Watcher (behavioral monitoring system).
I get the point of testing using download cradles and other means of delivery, but 85% or so of malware is still delivered as a fully-contained executable via user download, drive-by download, or email attachment within a .zip archive - now that is both consumer and enterprise combined. Contained within that 85% is infected USB flash drive delivered malware.
Most threat actors perform simple "Spray and Pray" campaigns of .exe files. They don't take the time or make the effort to craft themselves or purchase more sophisticated attack methods. Malicious PDF and Office Macro campaigns have dropped-off significantly within the past decade because of the preventions and countermeasures added by Adobe and Microsoft to prevent those attack methods from working by default.
So while none of that invalidates or undermines your advocacy of full-chain testing, execution from the desktop remains a fully legitimate test methodology. Testers, test labs, and software publishers are going to do what is lowest cost in terms of time, effort, and expense. Human nature.
It would be nice if AV labs would do the type of testing that you advocate for, but it is so time consuming and expensive to do so, that only a couple do it and only then rarely because the publishers don't want to pay for the testing costs. Heck, AV publishers themselves don't do that kind of testing. Some do if they are fortunate enough to locate "live in-the-wild" samples, but they will not go through the trouble of creating entire sophisticated exploit and infection vector chains for testing purposes. The vast majority are going to use static and dynamic analysis, with a heavy reliance upon sandbox analysis.
When AV test labs or publishers do make the effort, then the criticism becomes "Well that is a simulation and not a real-world in-the-wild kill chain." So even when they try, there are critics that immediately bash the effort.
The "issue" with Emsisoft raised in this thread is that it did not stop one (1) infection. Immediately the Emsisoft bashing began without any analysis or confirmation of the malware type tested. Malware evolves. New malware is developed. Behavior blockers only improve if someone reports the issues to the software publisher - which is main point regardless of the test methodology utilized.
While desktop execution is essential for testing raw signature and heuristic capabilities, it can't show us how well a suite proactively defends against a real-world, multi-stage attack. To get a complete picture of a product's abilities, we need to see how it handles the entire kill chain.I don't disagree with you, but AMSTO is never going to adopt those conditions due to complexity and expense of effort required. As far as Youtube testers, they're never going to do it. Oh, it's easy enough to write a script, Office macro, short-cut file, etc to perform a download or spawn child processes - but only a few such testers are capable or willing to do it.
For the Emsisoft Behavior Blocker most of that will not matter, which is part of the point. It is a HIPS style behavior blocker that monitors for certain generic actions. In my own testing, if Emsisoft does not prevent the download or block the first stage file, in a significant % of instances the behavior blocker will fail to stop malware from infecting a system even when the user responds to the manual BB alert with "Block Always" or "Block Once."
In some respects, the Emsisoft Behavior Blocker is a lot like the old SpyShelter HIPS. While it was rare for SpyShelter HIPS to stop a malware infection when the user chose "Terminate (the process)" (the correct choice in all cases), it did not prevent many infections when the user selected "Block (the process action)." Even when selecting "Block Always," which is the equivalent of the "Terminate" within old SpyShelter, the Emsisoft BB often failed. The Emsisoft BB is not at the same level as Kaspersky's System Watcher (behavioral monitoring system).
I get the point of testing using download cradles and other means of delivery, but 85% or so of malware is still delivered as a fully-contained executable via user download, drive-by download, or email attachment within a .zip archive - now that is both consumer and enterprise combined. Contained within that 85% is infected USB flash drive delivered malware.
Most threat actors perform simple "Spray and Pray" campaigns of .exe files. They don't take the time or make the effort to craft themselves or purchase more sophisticated attack methods. Malicious PDF and Office Macro campaigns have dropped-off significantly within the past decade because of the preventions and countermeasures added by Adobe and Microsoft to prevent those attack methods from working by default.
So while none of that invalidates or undermines your advocacy of full-chain testing, execution from the desktop remains a fully legitimate test methodology. Testers, test labs, and software publishers are going to do what is lowest cost in terms of time, effort, and expense. Human nature.
It would be nice if AV labs would do the type of testing that you advocate for, but it is so time consuming and expensive to do so, that only a couple do it and only then rarely because the publishers don't want to pay for the testing costs. Heck, AV publishers themselves don't do that kind of testing. Some do if they are fortunate enough to locate "live in-the-wild" samples, but they will not go through the trouble of creating entire sophisticated exploit and infection vector chains for testing purposes. The vast majority are going to use static and dynamic analysis, with a heavy reliance upon sandbox analysis.
When AV test labs or publishers do make the effort, then the criticism becomes "Well that is a simulation and not a real-world in-the-wild kill chain." So even when they try, there are critics that immediately bash the effort.
The "issue" with Emsisoft raised in this thread is that it did not stop one (1) infection. Immediately the Emsisoft bashing began without any analysis or confirmation of the malware type tested. Malware evolves. New malware is developed. Behavior blockers only improve if someone reports the issues to the software publisher - which is main point regardless of the test methodology utilized.
This brings us to the core issue, declaring a product has failed based solely on a desktop execution test is a flawed conclusion. The problem isn't just the result, but the process itself, which prevents the product's full suite of proactive, layered defenses from ever being engaged.
You may also like...
-
App Review Kaspersky Premium vs McAfee Advanced
- Started by Shadowra
- Replies: 87
-
App Review Emsisoft Anti-Malware Home 2025
- Started by Shadowra
- Replies: 52
-
-
App Review Battle: Bitdefender Free Antivirus vs Comodo Free Antivirus | Test and Review | 2025
- Started by NB InfoTech
- Replies: 1
-
App Review Battle: Bitdefender Free Antivirus vs Avira Free Antivirus | Test and Review | 2025
- Started by NB InfoTech
- Replies: 7

