When you’re planning to rob the Russian cyber mob, you’d better make sure that you have the element of surprise, that you can make a clean getaway, and that you understand how your target is going to respond. Today’s column features an interview with two security experts who helped plan and execute last week’s global, collaborative effort to hijack the Gameover Zeus botnet, an extremely resilient and sophisticated crime machine that helped an elite group of thieves steal more than $100 million from banks, businesses and consumers worldwide.
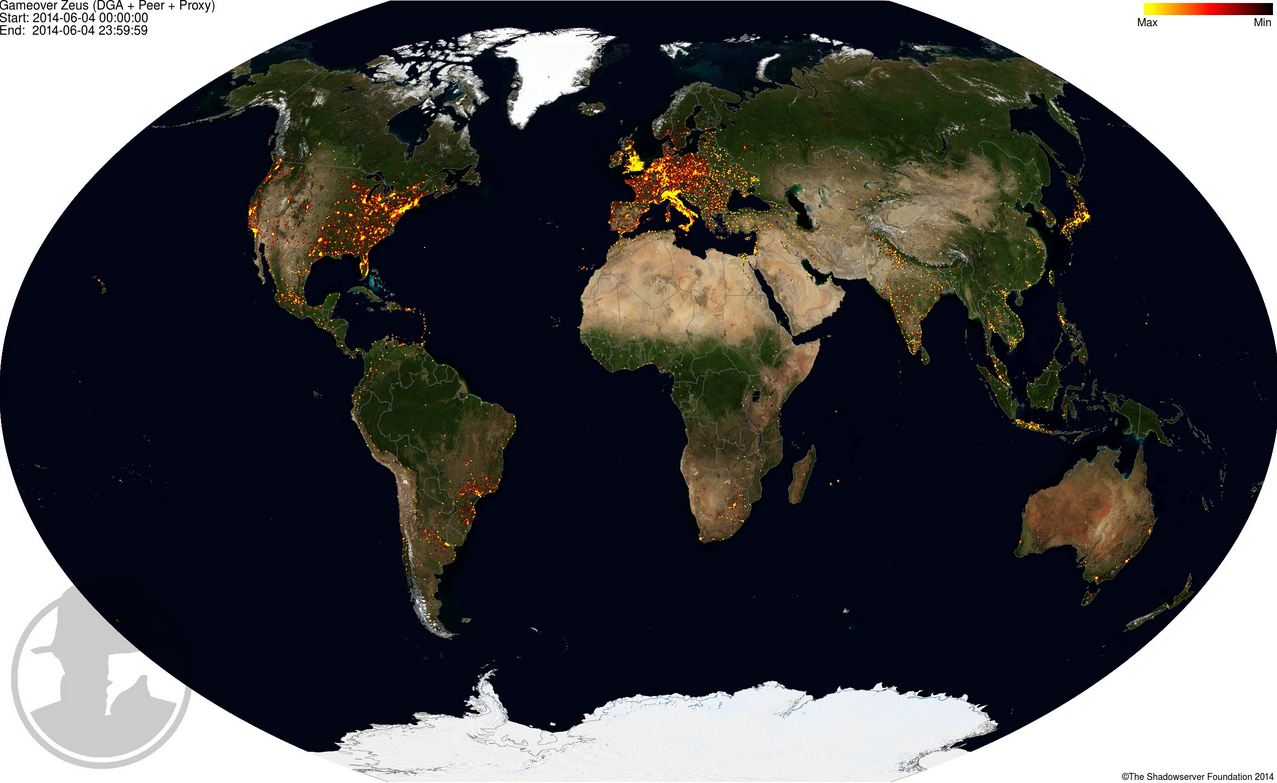
Gameover infections on June 4, 2014. Source: Shadowserver.org:
Neither expert I spoke with wished to be identified for this story, citing a lack of permission from their employers and a desire to remain off the radar of the crooks inconvenienced by the action. For obvious reasons, they were also reluctant to share details about the exact weaknesses that were used to hijack the botnet, focusing instead on the planning and and preparation that went into this effort.
GAMEOVER ZEUS PRIMER
A quick review of how Gameover works should help readers get more out of the interview. In traditional botnets, infected PCs report home to and are controlled by a central server. But this architecture leaves such botnets vulnerable to disruption or takeover if authorities or security experts can gain access to the control server.
Gameover, on the other hand, is a peer-to-peer (P2P) botnet designed as a collection of small networks that are distinct but linked up in a decentralized fashion. The individual Gameover-infected PCs are known as “peers.” Above the peers are a select number of slightly more powerful and important infected systems that are assigned roles as “proxy nodes,” meaning they were selected from the peers to serve as relay points for commands coming from the Gameover botnet operators and as conduits for encrypted data stolen from the infected systems.
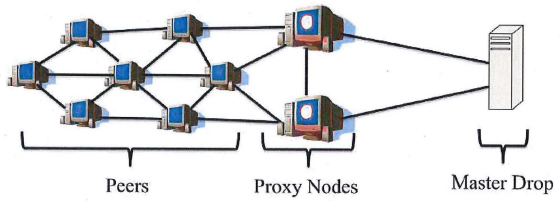
The basic network structure of the Gameover botnet. Source: FBI
Article
Gameover infections on June 4, 2014. Source: Shadowserver.org:

Neither expert I spoke with wished to be identified for this story, citing a lack of permission from their employers and a desire to remain off the radar of the crooks inconvenienced by the action. For obvious reasons, they were also reluctant to share details about the exact weaknesses that were used to hijack the botnet, focusing instead on the planning and and preparation that went into this effort.
GAMEOVER ZEUS PRIMER
A quick review of how Gameover works should help readers get more out of the interview. In traditional botnets, infected PCs report home to and are controlled by a central server. But this architecture leaves such botnets vulnerable to disruption or takeover if authorities or security experts can gain access to the control server.
Gameover, on the other hand, is a peer-to-peer (P2P) botnet designed as a collection of small networks that are distinct but linked up in a decentralized fashion. The individual Gameover-infected PCs are known as “peers.” Above the peers are a select number of slightly more powerful and important infected systems that are assigned roles as “proxy nodes,” meaning they were selected from the peers to serve as relay points for commands coming from the Gameover botnet operators and as conduits for encrypted data stolen from the infected systems.

The basic network structure of the Gameover botnet. Source: FBI
Article