Cybersecurity researchers have called attention to a new antivirus evasion technique that involves embedding a malicious Microsoft Word file into a PDF file.
The sneaky method, dubbed
MalDoc in PDF by JPCERT/CC, is said to have been employed in an in-the-wild attack in July 2023.
"A file created with MalDoc in PDF can be opened in Word even though it has magic numbers and file structure of PDF," researchers Yuma Masubuchi and Kota Kino
said. "If the file has a configured macro, by opening it in Word, VBS runs and performs malicious behaviors."
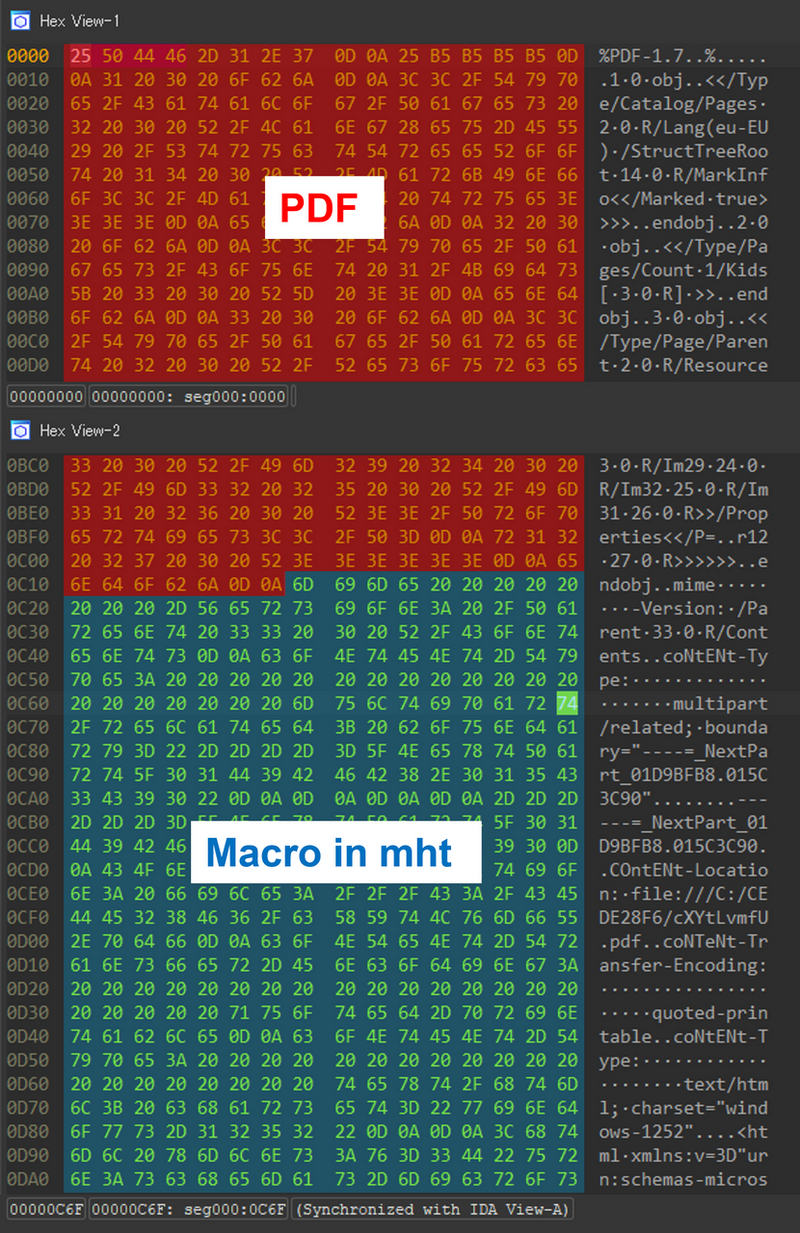
Such specially crafted files are called
polyglots as they are a legitimate form of multiple different file types, in this case, both PDF and Word (DOC).
This entails adding an MHT file created in Word and with a macro attached after the PDF file object. The end result is a valid PDF file that can also be opened in the Word application.
Put differently; the PDF document embeds within itself a Word document with a VBS macro that's designed to download and install an MSI malware file if opened as a .DOC file in Microsoft Office. It's not immediately clear what malware was distributed in this fashion.