- Feb 4, 2016
- 549
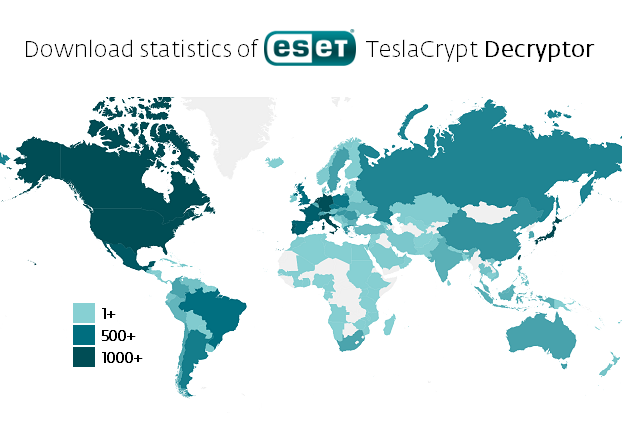
It has been two weeks since ESET created a TeslaCrypt decryptor, which allows victims of the ransomware to get their files back. This came on the back of its developers ceasing operations. Since then, over 32,000 users around the globe have taken advantage of this opportunity and downloaded the tool.
But even with TeslaCrypt abandoning its territory, malware extortion families have lost none of their prominence amongst cybercriminals. With unceasing waves of JS/TrojanDownloader.Nemucod andJS/Danger.ScriptAttachment trying to download several variants of Locky, it would seem that this ransomware would be the one to lay claim to former TeslaCrypt’s turf.
But according to ESET LiveGrid® statistics, there is another player in the game, showing an even higher level of prevalence – namely Win32/Filecoder.Crysis.
Full article : Beyond TeslaCrypt: Crysis family lays claim to parts of its territory
But even with TeslaCrypt abandoning its territory, malware extortion families have lost none of their prominence amongst cybercriminals. With unceasing waves of JS/TrojanDownloader.Nemucod andJS/Danger.ScriptAttachment trying to download several variants of Locky, it would seem that this ransomware would be the one to lay claim to former TeslaCrypt’s turf.
But according to ESET LiveGrid® statistics, there is another player in the game, showing an even higher level of prevalence – namely Win32/Filecoder.Crysis.
Full article : Beyond TeslaCrypt: Crysis family lays claim to parts of its territory
