- Jul 27, 2015
- 5,458
Bisonal is a remote access trojan (RAT) that's part of the Tonto Team arsenal. The peculiarity of the RAT is that it's been in use for more than 10 years — this is an uncommon and long period for malware. Over the years, it has evolved and adapted mechanisms to avoid detection while keeping the core of its RAT the same. We identified specific functions here for more than six years.
How did it work?
Bisonal used multiple lure documents to entice their victims to open and then be infected with Bisonal malware. This group has continued its operations for over a decade and they continue to evolve their malware to avoid detection. Bisonal primarily used spear phishing to obtain a foothold within their victims' networks. Their campaigns had very specific targets which would suggest their end game was more around operational intelligence gathering and espionage.
So what?
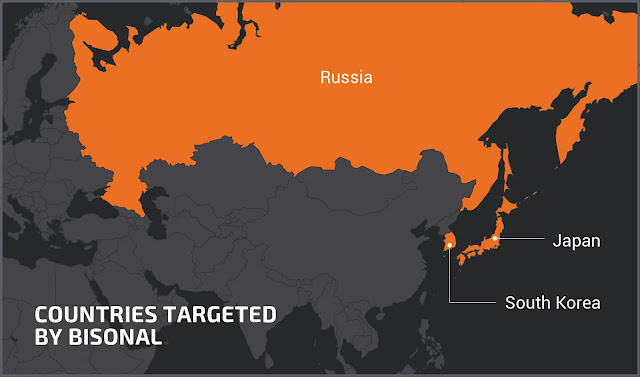
This is an extremely experienced group likely to keep their activities even after exposure, even if we identified mistakes and bad copy/paste, they are doing this job for more than 10 years. We think that exposing this malware, explaining the behavior and the campaigns where Bisonal was used is important to protect the potential future targets. The targets to this point are located in the public and private sectors with a focus on Russia, Japan and South Korea. We recommend the entities located in this area to prepare for this malware and actor and implement detections based on the technical details provided in this article.

Bisonal: 10 years of play
By Warren Mercer, Paul Rascagneres and Vitor Ventura. Update 06/03/20: added samples from 2020. Executive summary * Security researchers detected and exposed the Bisonal malware over the past 10 years. But the Tonto team, the threat actor behind it, didn't stop. * The victimology didn't...
 blog.talosintelligence.com
blog.talosintelligence.com
