- Aug 17, 2014
- 11,775
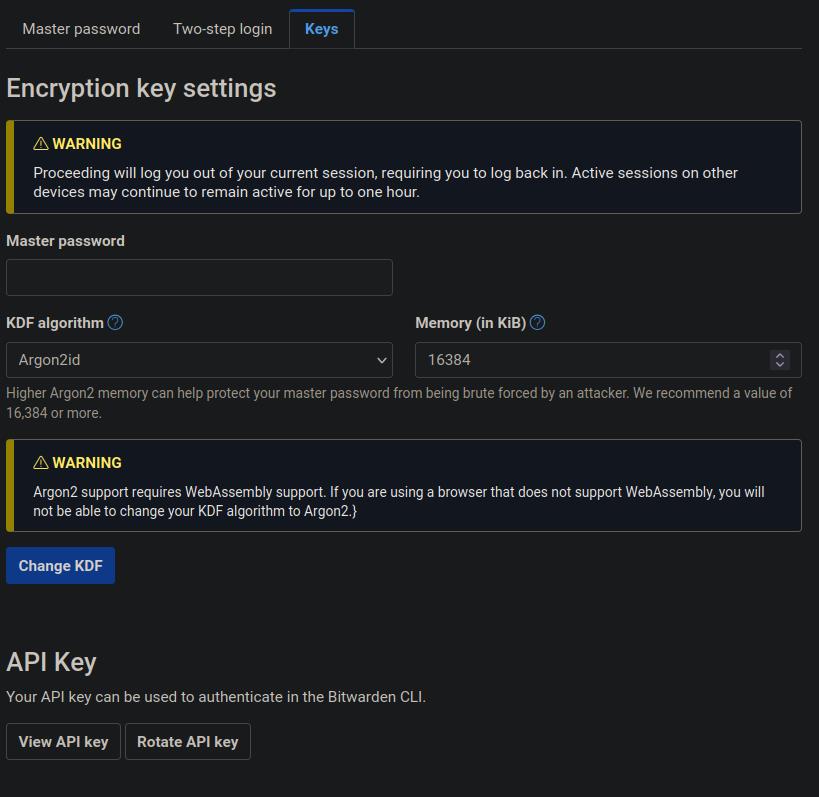
According to comments posted by Quexten at Bitwarden's community forums, the company has a 5-week release cycle, so we could expect Argon2 support to be added next month on all platforms if the tests are successful. The feature will be opt-in, and should be available on the same page as the password iteration settings in Bitwarden's web vault.
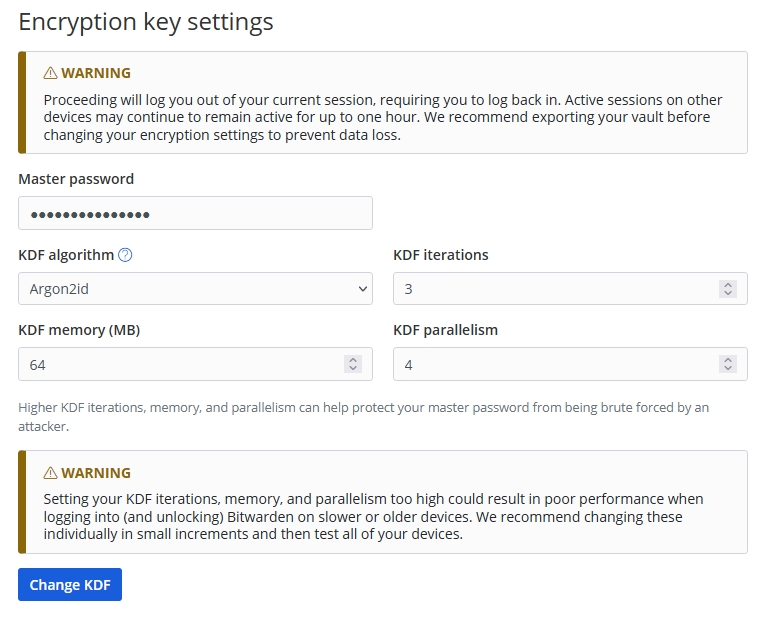
Bitwarden's implementation will use Argon2id. With PBKDF users have just one parameter that they can control, to set the number of iterations. Argon2 will offer more options, you will be able to set the number of iterations, the amount of memory to use, for example 64MB, and Parallelism lets you define the number of parallel threads to be used.

Bitwarden Password Manager will add support for Argon2 KDF soon - gHacks Tech News
Bitwarden Password Manager is set to become more secure than ever. It will add support for Argon2 KDF soon.
www.ghacks.net