Hello everyone!! 
Here is my botnet anatomy. I hope you like it!
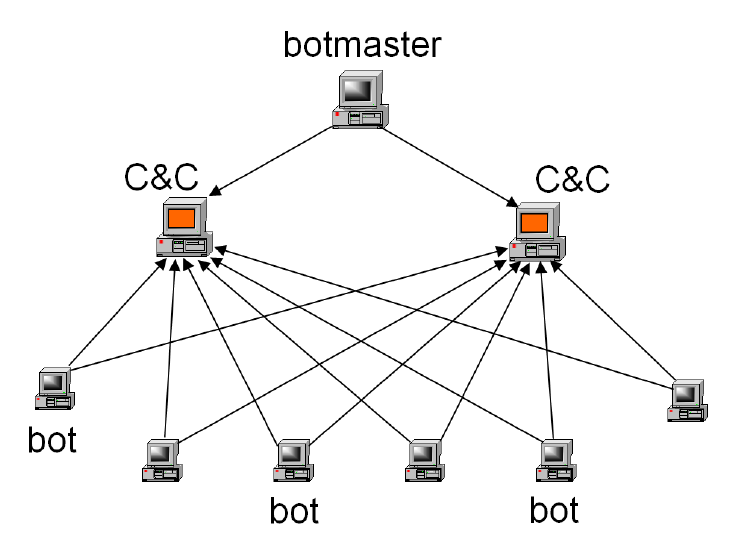
A botnet is a network of computers under the control of a botnet master. Consists of two components, the network of infected computers called zombie or drones, and a control panel (command and control, C&C) where the botnet master can control all the computers at once.
Another advantage of C&C is that the botnet master does not connect directly to the drones. C&C Unit acts as a mediator between the master and the botnet botnets, adding a layer of anonymity between the drones and the botnet master. Botnet master who will connect to C&C via Tor, Proxy or other method of anonymity. As you can understand, the owner of a botnet is daunting.
We see in detail the components of a botnet, C&C methods, purpose and how do Botnets:
Command and control unit (C&C). It's an interface from which the botnet master can run commands and obtain information about drones. From this centralized platform you control the entire botnet. The botnet master becomes the General of an army absolutely obedient and effective.
Zombie (or drones). Computers are infected. Unsuspecting computer users unwittingly deliver their PCs to the botnet master. The PCs so "enrolled" become an army ordered soldiers and obedient, which could lead to logout as attacks (DDoS) or espionage (Keylogging).
The control unit can take several forms, but the typical incarnations are:
IRC, Internet Relay Chat: is the most classic form of control interface, the oldest form of online chat, the most beloved by hackers. Imagine a chatroom with thousands of users, who are not members but drones. A command written in the chat from the botnet master gets the immediate mobilization of thousands of zombies.
Http: a little more awkward version of Irc but with the advantage that Http generally is filtered by the firewall. In this case the botnet master faces a web page (or a web application) where you can control all aspects of the botnet and ordering attacks, exactly as in the Irc chat.
What is a botnet? Let's see:
Spam: the millions of daily messages that inundate the Internet daily depart from drones.
Proxy: Botnets can be used as platforms to bouncing, useful for tactical bounce connections through several drones before reaching the target. Track the source of an intrusion diverted through these nodes become a virtually impossible job.
Keylogger: drones can be used to spy on users. Sensitive documents, financial data, e-banking account.
DDoS: together to spam the main activity of a botnet. The interfaces of C&C botnet can master, with a single command, unleashing thousands of drones against a single computer with the result of the paralization of the activity.
How is formed, develops and spreads a botnet? By: worm
By its nature the worm is the tool used to form a botnet. Typically a worm uses a vector of infection with high penetration such as bugs in Windows RPC services, but also more mundane streets tries as the invasion of shared resources or simple dictionary attacks against weak password protected shares. Once completed your computer infection is transformed to indrone and passes under the control of the botnet master. Worms can also be quite sophisticated, and cryptographic techniques can be used for communications with the C&C; can auto-update with more powerful versions and insightful. The worm also uses the drone to scan the network looking for other victims to aggregate to botnets.
We have seen how a botnet master controls thousands of infected computers (drones) with a simple interface (C&C), that interface also ensures a fair level of anonymity. With those tools he is able to carry out any illegal activity possible on the network. The formation and dissemination of botnet is entrusted to the worm, which spreads itself, infect the computer and deliver them to the botmaster.
By its very nature a botnet is a very dynamic and volatile entity: every day new drones are added, but others are lost.
Botnet activities are monitored by Counterintelligence units (honeypot), gathering intelligence on the activities of these "weapons" and digital attempt to provide contrast forces useful information in order to neutralize the threat.
Users can give a hand to the botnet contrast with a few simple actions, such as using a personal firewall and keep their PCs.
To complete the thread I want to add that the bots can be used as remote stockage units for illegal datas. (Suggestion by @Umbra ).
Thanks for reading
Here is my botnet anatomy. I hope you like it!
A botnet is a network of computers under the control of a botnet master. Consists of two components, the network of infected computers called zombie or drones, and a control panel (command and control, C&C) where the botnet master can control all the computers at once.
Another advantage of C&C is that the botnet master does not connect directly to the drones. C&C Unit acts as a mediator between the master and the botnet botnets, adding a layer of anonymity between the drones and the botnet master. Botnet master who will connect to C&C via Tor, Proxy or other method of anonymity. As you can understand, the owner of a botnet is daunting.
We see in detail the components of a botnet, C&C methods, purpose and how do Botnets:
Command and control unit (C&C). It's an interface from which the botnet master can run commands and obtain information about drones. From this centralized platform you control the entire botnet. The botnet master becomes the General of an army absolutely obedient and effective.
Zombie (or drones). Computers are infected. Unsuspecting computer users unwittingly deliver their PCs to the botnet master. The PCs so "enrolled" become an army ordered soldiers and obedient, which could lead to logout as attacks (DDoS) or espionage (Keylogging).
The control unit can take several forms, but the typical incarnations are:
IRC, Internet Relay Chat: is the most classic form of control interface, the oldest form of online chat, the most beloved by hackers. Imagine a chatroom with thousands of users, who are not members but drones. A command written in the chat from the botnet master gets the immediate mobilization of thousands of zombies.
Http: a little more awkward version of Irc but with the advantage that Http generally is filtered by the firewall. In this case the botnet master faces a web page (or a web application) where you can control all aspects of the botnet and ordering attacks, exactly as in the Irc chat.
What is a botnet? Let's see:
Spam: the millions of daily messages that inundate the Internet daily depart from drones.
Proxy: Botnets can be used as platforms to bouncing, useful for tactical bounce connections through several drones before reaching the target. Track the source of an intrusion diverted through these nodes become a virtually impossible job.
Keylogger: drones can be used to spy on users. Sensitive documents, financial data, e-banking account.
DDoS: together to spam the main activity of a botnet. The interfaces of C&C botnet can master, with a single command, unleashing thousands of drones against a single computer with the result of the paralization of the activity.
How is formed, develops and spreads a botnet? By: worm
By its nature the worm is the tool used to form a botnet. Typically a worm uses a vector of infection with high penetration such as bugs in Windows RPC services, but also more mundane streets tries as the invasion of shared resources or simple dictionary attacks against weak password protected shares. Once completed your computer infection is transformed to indrone and passes under the control of the botnet master. Worms can also be quite sophisticated, and cryptographic techniques can be used for communications with the C&C; can auto-update with more powerful versions and insightful. The worm also uses the drone to scan the network looking for other victims to aggregate to botnets.
We have seen how a botnet master controls thousands of infected computers (drones) with a simple interface (C&C), that interface also ensures a fair level of anonymity. With those tools he is able to carry out any illegal activity possible on the network. The formation and dissemination of botnet is entrusted to the worm, which spreads itself, infect the computer and deliver them to the botmaster.
By its very nature a botnet is a very dynamic and volatile entity: every day new drones are added, but others are lost.
Botnet activities are monitored by Counterintelligence units (honeypot), gathering intelligence on the activities of these "weapons" and digital attempt to provide contrast forces useful information in order to neutralize the threat.
Users can give a hand to the botnet contrast with a few simple actions, such as using a personal firewall and keep their PCs.
To complete the thread I want to add that the bots can be used as remote stockage units for illegal datas. (Suggestion by @Umbra ).

Thanks for reading
Last edited: