A
Alkajak
Thread author
While trying to find bugs in Facebook's services, a security researcher accidentally stumbled over a hacker's backdoor script that was logging Facebook employee credentials for some of the company's backend applications.
Orange Tsai, a consultant for DevCore, also spends a lot of his free time helping big name companies fix vulnerabilities via their bug bounty programs. At the end of February, Tsai decided to give Facebook's bug bounty program another try and started mapping some of the company's backend services for possible servers he might hack.
Researcher hacks Facebook's internal file sharing application
His search led him to the files.fb.com domain, which is an online file transfer and file hosting service, running on Accellion’s Secure File Transfer (FTA) application.
After identifying the application's type and version, the researcher went to work and explored its source code, discovering in three cross-site scripting (XSS) flaws, two local privilege escalation issues, a known-secret-key issue that led to remote code execution, and a pre-auth SQL injection that also led to remote code execution.
The researcher used the SQL injection flaw he discovered in the FTA application to access Facebook's server and was rewarded with complete control over the machine.
With his goal reached, the researcher then started collecting the necessary information to submit a bug report to Facebook's staff. While looking at one of the server's logs, Tsai discovered a lot of suspicious error messages.
Somebody already hacked the server and not part of the bug bounty program
He tracked these messages down to a webshell, which he was sure, and quite obvious, that no Facebook employee ever uploaded. Inspecting the webshell's source code, Tsai found evidence of a server-side keylogger which was intercepting login operations and storing Facebook employee access credentials in a local log file.
The researcher then looked at other log files that showed how the hacker came back at various intervals to collect the logged data, map the local network, and attempt to steal SSL private keys.
Details revealed two separate periods when the hacker was active, one in July 2015, and then one in mid-September 2015.
Tsai filed a bug report with Facebook about the incident, who started an in-house forensics investigation, and rewarded the researcher with $10,000 (€8,850) for his efforts.
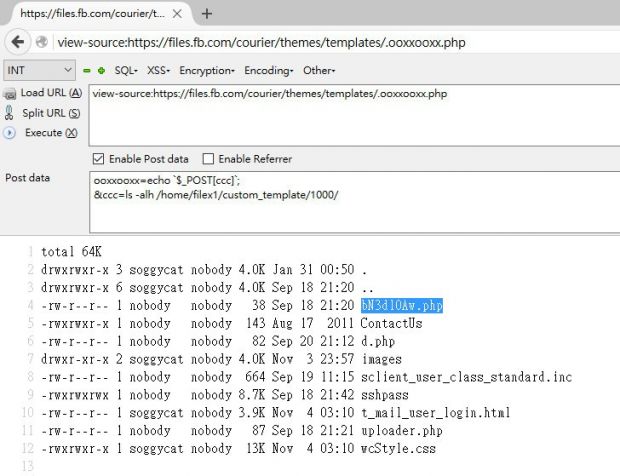
The webshell on Facebook's server
Orange Tsai, a consultant for DevCore, also spends a lot of his free time helping big name companies fix vulnerabilities via their bug bounty programs. At the end of February, Tsai decided to give Facebook's bug bounty program another try and started mapping some of the company's backend services for possible servers he might hack.
Researcher hacks Facebook's internal file sharing application
His search led him to the files.fb.com domain, which is an online file transfer and file hosting service, running on Accellion’s Secure File Transfer (FTA) application.
After identifying the application's type and version, the researcher went to work and explored its source code, discovering in three cross-site scripting (XSS) flaws, two local privilege escalation issues, a known-secret-key issue that led to remote code execution, and a pre-auth SQL injection that also led to remote code execution.
The researcher used the SQL injection flaw he discovered in the FTA application to access Facebook's server and was rewarded with complete control over the machine.
With his goal reached, the researcher then started collecting the necessary information to submit a bug report to Facebook's staff. While looking at one of the server's logs, Tsai discovered a lot of suspicious error messages.
Somebody already hacked the server and not part of the bug bounty program
He tracked these messages down to a webshell, which he was sure, and quite obvious, that no Facebook employee ever uploaded. Inspecting the webshell's source code, Tsai found evidence of a server-side keylogger which was intercepting login operations and storing Facebook employee access credentials in a local log file.
The researcher then looked at other log files that showed how the hacker came back at various intervals to collect the logged data, map the local network, and attempt to steal SSL private keys.
Details revealed two separate periods when the hacker was active, one in July 2015, and then one in mid-September 2015.
Tsai filed a bug report with Facebook about the incident, who started an in-house forensics investigation, and rewarded the researcher with $10,000 (€8,850) for his efforts.

The webshell on Facebook's server