Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,871
Introduction
This is a short fact sheet for our Business Main-Test Series, containing the results of the Business Malware Protection Test (September) and Business Real-World Protection Test (August-September). The full report, including the Performance Test and product reviews, will be released in December. To be certified in December 2021 as an “Approved Business Product” by AV-Comparatives, the tested products must score at least 90% in the Malware Protection Test with zero false alarms on common business software, and at least 90% in the overall Real-World Protection Test (i.e. over the course of four months), with less than one hundred false alarms on any clean software/websites (and with zero false alarms on common business software). Tested products must also avoid major performance issues (impact score must be below 40) and have fixed all reported bugs in order to gain certification.
Please note that the results of the Business Main-Test Series cannot be compared with the results of the Consumer Main-Test Series, as the tests are done at different times, with different sets, different settings, etc.
Starting from 2022, products will be required to have an FP rate on non-business files below the Remarkably High threshold.
Test ResultsBelow we have listed relevant deviations from default settings (i.e. setting changes applied by the vendors):
Acronis: “Backup”, “Vulnerability assessment”, “Patch management” and “Data protection map” disabled.
Bitdefender: “Fileless Attack Protection”, “Sandbox Analyzer” (for Applications and Documents) and “Scan SSL” enabled. “Encryption” and “Patch Management” add-ons registered and enabled. “HyperDetect” and “Device Sensor” disabled. “Update ring” changed to “Fast ring”. “Web Traffic Scan” enabled for HTTP Web traffic and Incoming POP3 emails.
Cisco: “On Execute File and Process Scan” set to Active; “Exploit Prevention: Script Control” and “TETRA Deep Scan File” enabled; “Event Tracing for Windows” enabled.
CrowdStrike: everything enabled and set to maximum, i.e. “Extra Aggressive”. “Sensor Visibility” for “Firmware” disabled. Uploading of “Unknown Detection-Related Executables” and “Unknown Executables” disabled.
Cybereason: “Anti-Malware” enabled; “Signatures mode” set to “Disinfect”; “Behavioral document protection” enabled; “Artificial intelligence” and “Anti-Exploit” set to “Aggressive”; “Exploit protection”, “PowerShell and .NET”, “Anti-Ransomware” and “App Control” enabled and set to “Prevent”; all “Collection features” enabled; “Scan archives on access” enabled.
Elastic: MalwareScore (“windows.advanced.malware.threshold”) set to “aggressive”.
ESET: All “Real-Time & Machine Learning Protection” settings set to “Aggressive”.
FireEye: “Real-Time Indicator Detection” disabled, “Exploit Guard” and “Malware Protection” enabled.
Fortinet: “Sandbox analysis” (FortiSandbox) and FortiEDR enabled. “Submit files from USB Sources” disabled; “Exclude Files from Trusted Sources” for “Sandbox Detection” enabled; in “Execution Prevention”, “Suspicious Script Execution” was disabled and “Unconfirmed File Detected” was enabled; eXtended Detection (XDR) was disabled.
G Data: “BEAST Behavior Monitoring” set to “Halt program and move to quarantine”. “G DATA WebProtection” add-on for Google Chrome installed and activated.
Malwarebytes: “Expert System Algorithms”, “Block penetration testing attacks”, “Disable IE VB Scripting”, “Java Malicious Inbound/outbound Shell Protection”, “Earlier RTP blocking”, “Enhanced sandbox protection” and “Thorough scan” enabled; “RET ROP Gadget detection” and “Malicious LoadLibrary Protection” enabled for all applications; “Protection for MessageBox Payload” enabled for MS Office; “Malwarebytes Browser Guard” Chrome extension enabled.
Microsoft: Google Chrome extension “Windows Defender Browser Protection” installed and enabled.
Sophos: “Threat Case creation” and “Web Control” disabled.
VIPRE: “DNS Traffic Filtering” and “Malicious URL Blocking for HTTPS Traffic” enabled. “Firewall” and “IDS” enabled and set to “Block With Notify”.
VMware: policy set to “Advanced”.
Avast, K7, Kaspersky, Panda: default settings.
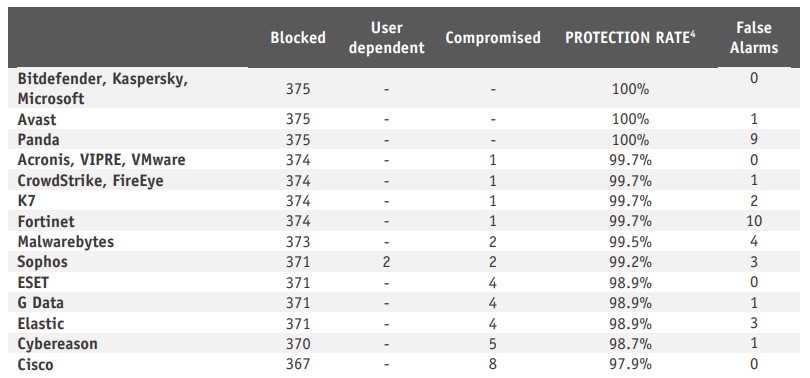
Real-World Protection Test (August-September)
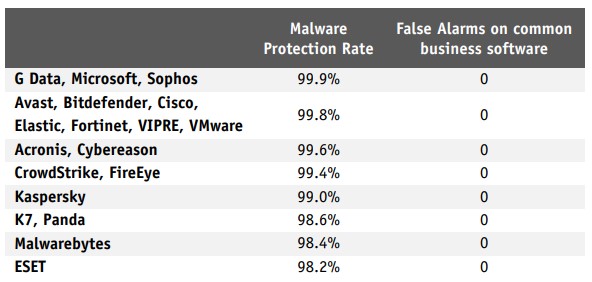
Malware Protection Test (September)
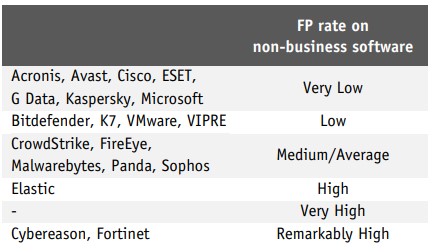
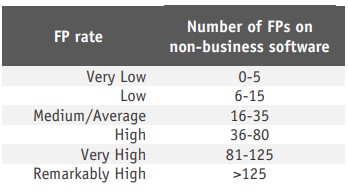

Business Security Test August-September 2021 - Factsheet
The Business Security Test August-September 2021 - Factsheet covering results of our Enterprise main-test series has been released.
 www.av-comparatives.org
www.av-comparatives.org


