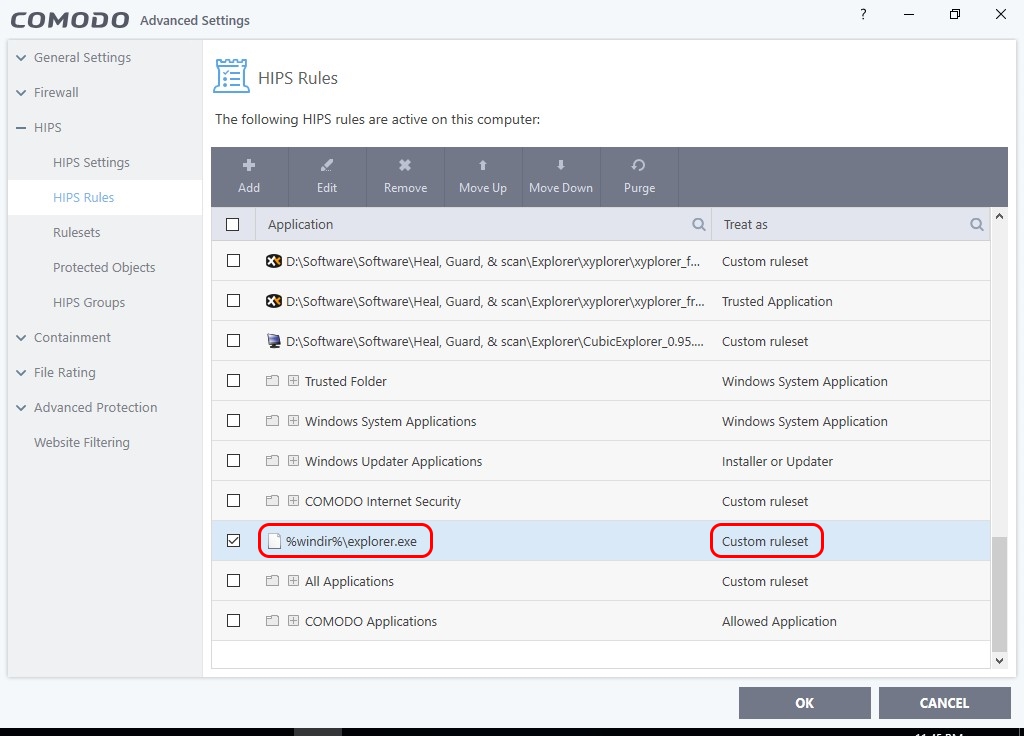
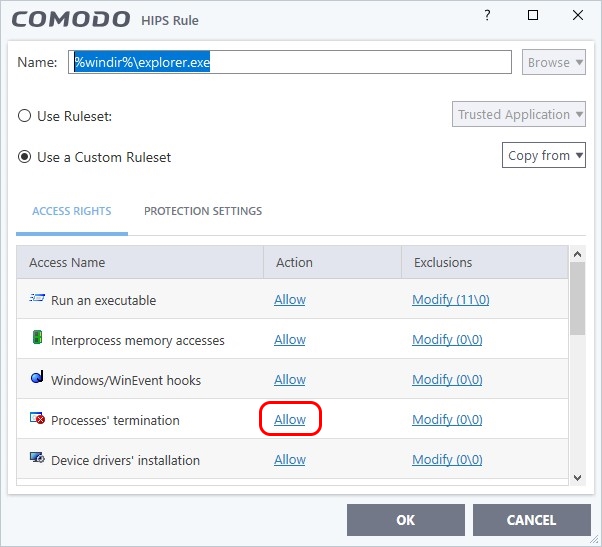
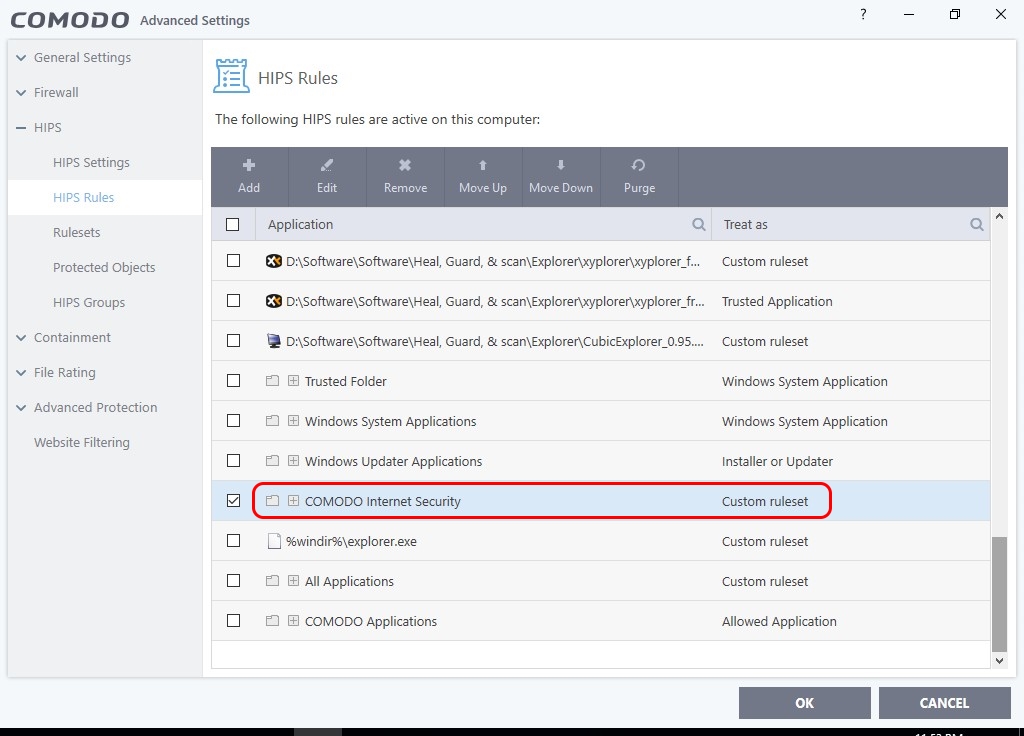
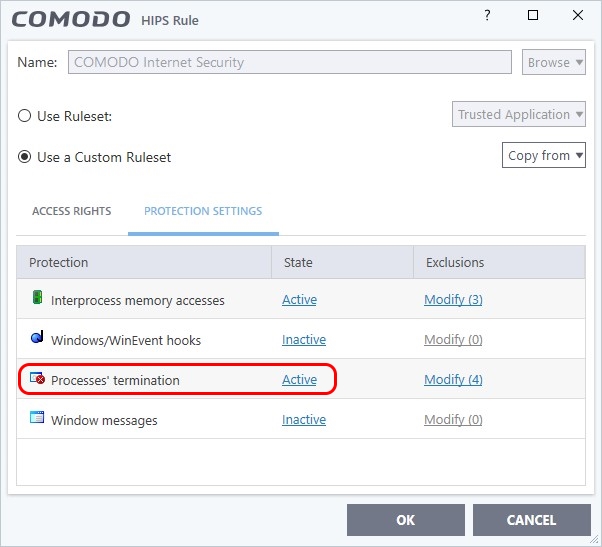
How does comodo firewall protects against signed malware at cruelsister's settings? Also i can disable its processes via task manager. How its self protection?
I am going to use it on my system with cruelsister's settings but these issues are my main concern which do not let me believe in comodo's power.
So,help me out and give the required info.
Thanks.
I am going to use it on my system with cruelsister's settings but these issues are my main concern which do not let me believe in comodo's power.
So,help me out and give the required info.
Thanks.