please can anyone help me?
when im trying to recovery my files with emsisoft decryptor for STOP djvu
(this ID appears to be an online ID, decryption is impossible) this is the notice.
is any chance to recovery my files?
i install new windows but my D and E disk is already virused cant open single files. please someone help me if there is any worker or app to help me for my files recovery. thank you
 .
.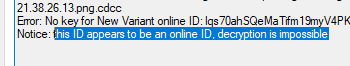
when im trying to recovery my files with emsisoft decryptor for STOP djvu
(this ID appears to be an online ID, decryption is impossible) this is the notice.
is any chance to recovery my files?
i install new windows but my D and E disk is already virused cant open single files. please someone help me if there is any worker or app to help me for my files recovery. thank you
 .
.