- Jan 24, 2011
- 9,378
Two Israeli security firms that took a closer look at the Cerber ransomware operations claim that the criminal group running this complex ransomware service is making around $78,000 per month from their illegal activities, which adds up to around $946,000 per year.
Following a lengthy investigation, the two companies, Check Point and IntSights, put together a technical report that offers an in-depth look at how the Cerber operation runs.
As a side effect of their efforts put into this task, the two even managed to create a Cerber decrypter that can help victims unlock files for free.
Cerber run as a RaaS service
On the technical side of things, the people who developed Cerber opted to go for a RaaS model, a Ransomware-as-a-Service business that rents out the final ransomware payload to other crooks (called affiliates) who take it upon themselves to distribute it to victims.
This operational model is nothing groundbreaking and has been used by many other crooks who developed ransomware in the past, among whom the people behind the Chimera and Petya ransomware variants.
In most cases, Check Point has discovered that Cerber's distribution model involved the usage of exploit kits.
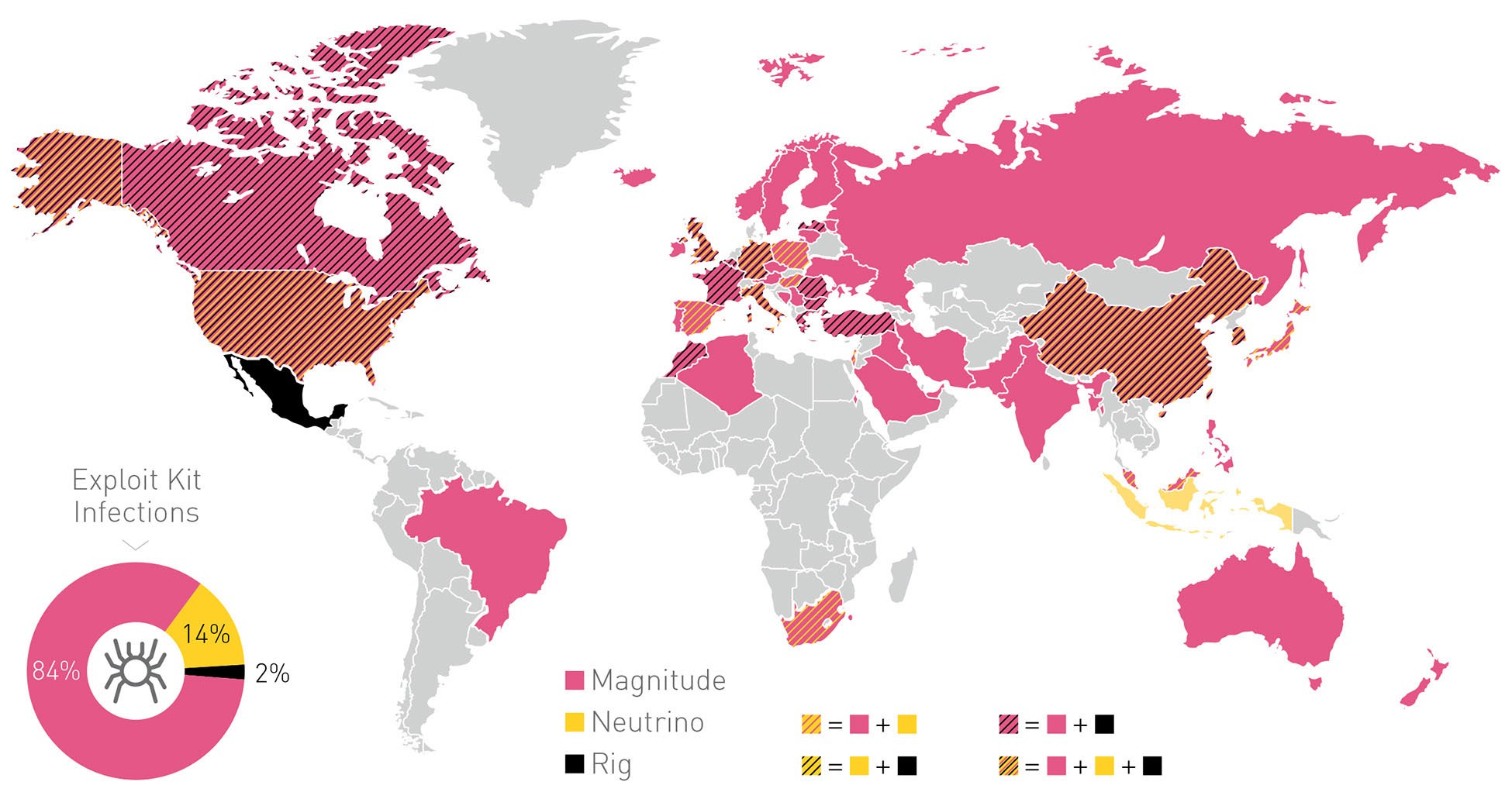
For most distribution campaigns, the affiliates relied on the Magnitude exploit kit (EK), which accounted for 84 percent of all Cerber EK-based infections. Other exploit kits were also used, like Neutrino (14 percent) ad RIG (2 percent), but to a smaller degree.
Read more: Cerber Ransomware Estimated Yearly Profit Is $946,000
Following a lengthy investigation, the two companies, Check Point and IntSights, put together a technical report that offers an in-depth look at how the Cerber operation runs.
As a side effect of their efforts put into this task, the two even managed to create a Cerber decrypter that can help victims unlock files for free.
Cerber run as a RaaS service
On the technical side of things, the people who developed Cerber opted to go for a RaaS model, a Ransomware-as-a-Service business that rents out the final ransomware payload to other crooks (called affiliates) who take it upon themselves to distribute it to victims.
This operational model is nothing groundbreaking and has been used by many other crooks who developed ransomware in the past, among whom the people behind the Chimera and Petya ransomware variants.
In most cases, Check Point has discovered that Cerber's distribution model involved the usage of exploit kits.
For most distribution campaigns, the affiliates relied on the Magnitude exploit kit (EK), which accounted for 84 percent of all Cerber EK-based infections. Other exploit kits were also used, like Neutrino (14 percent) ad RIG (2 percent), but to a smaller degree.
Read more: Cerber Ransomware Estimated Yearly Profit Is $946,000
