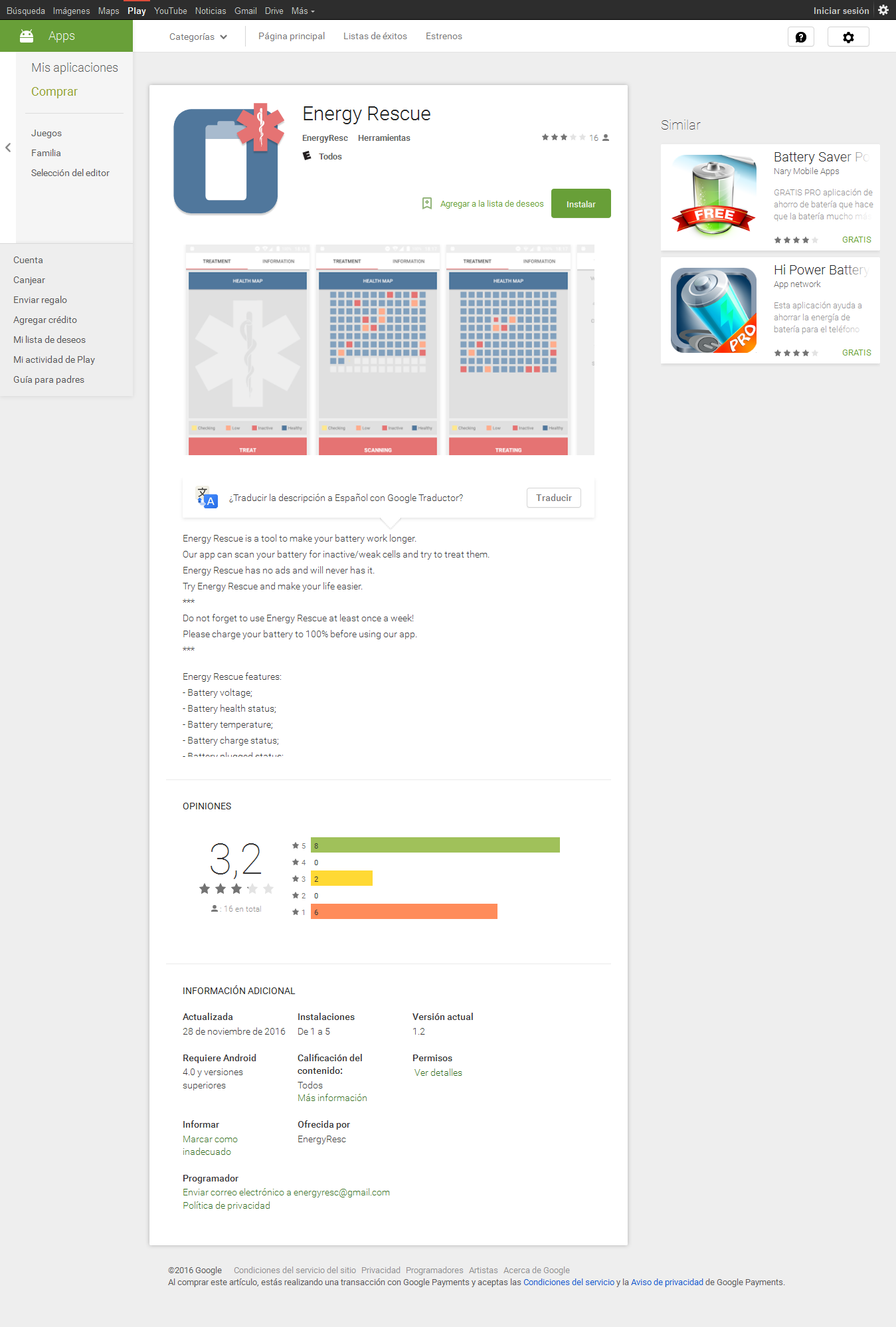
Google has removed an app from the Play Store that contained a new Android ransomware family named Charger.
The app's name is EnergyRescue, an app that posed as a battery-saving application, but which secretly stole a user's SMS messages and contact list, uploaded the data to the crooks' servers, and later locked the user's device.
The ransom note, embedded below, would go on to threaten users that if they didn't pay, they'd publish his data online.
You need to pay for us, otherwise we will sell portion of your personal information on black market every 30 minutes. WE GIVE 100% GUARANTEE THAT ALL FILES WILL RESTORE AFTER WE RECEIVE PAYMENT. WE WILL UNLOCK THE MOBILE DEVICE AND DELETE ALL YOUR DATA FROM OUR SERVER! TURNING OFF YOUR PHONE IS MEANINGLESS, ALL YOUR DATA IS ALREADY STORED ON OUR SERVERS! WE STILL CAN SELLING IT FOR SPAM, FAKE, BANK CRIME etc… We collect and download all of your personal data. All information about your social networks, Bank accounts, Credit Cards. We collect all data about your friends and family.
Some of these threats are empty since researchers didn't observe the app exfiltrating some of the information the crook's threatened to expose, such as credit card details and bank accounts.
This type of ransomware that makes (empty) threats to expose a user's private data has been recently referred to as "doxware."
Security firm Check Point says it came across this threat after their mobile security app had quarantined the device of a client that installed the app.
After analyzing the ransomware, researchers found several things that stood out, compared to previous Android ransomware families.
The biggest of these was how the ransomware infected devices. Previous threats relied on droppers to gain a foothold on infected devices. These would be small apps, with limited malicious behavior, but which would bypass Google's Play Store security checks, and later ask users for administrator rights.
If they'd convince users to grant them admin rights, these apps would download the real ransomware at later points.
Charger is quite sophisticated
With Charger this was different. Check Point says that the EnergyRescue app contained all the malicious code right from the get-go.
Despite putting all its code in one basket, researchers say that the Charger authors have done a good job at disguising the ransomware's malicious behavior.
For starters, they encoded all strings as binary arrays, making it hard to inspect the app, even by veteran security researchers.
Second, they loaded malicious code from encrypted resources, where Google's detection engine could not reach to inspect.
Third, they flooded the phone with useless commands, in order to hide malicious operations from a human's manual inspection.
Last, Charger also included code that would check if the app ran inside Android emulators, and stop the ransomware from triggering. This is most likely the feature that allowed Charger to bypass Bouncer, the Play Store's security scanner.
Read more: Charger Android Ransomware Reaches Google Play Store
The app's name is EnergyRescue, an app that posed as a battery-saving application, but which secretly stole a user's SMS messages and contact list, uploaded the data to the crooks' servers, and later locked the user's device.
The ransom note, embedded below, would go on to threaten users that if they didn't pay, they'd publish his data online.
You need to pay for us, otherwise we will sell portion of your personal information on black market every 30 minutes. WE GIVE 100% GUARANTEE THAT ALL FILES WILL RESTORE AFTER WE RECEIVE PAYMENT. WE WILL UNLOCK THE MOBILE DEVICE AND DELETE ALL YOUR DATA FROM OUR SERVER! TURNING OFF YOUR PHONE IS MEANINGLESS, ALL YOUR DATA IS ALREADY STORED ON OUR SERVERS! WE STILL CAN SELLING IT FOR SPAM, FAKE, BANK CRIME etc… We collect and download all of your personal data. All information about your social networks, Bank accounts, Credit Cards. We collect all data about your friends and family.
Some of these threats are empty since researchers didn't observe the app exfiltrating some of the information the crook's threatened to expose, such as credit card details and bank accounts.
This type of ransomware that makes (empty) threats to expose a user's private data has been recently referred to as "doxware."

Security firm Check Point says it came across this threat after their mobile security app had quarantined the device of a client that installed the app.
After analyzing the ransomware, researchers found several things that stood out, compared to previous Android ransomware families.
The biggest of these was how the ransomware infected devices. Previous threats relied on droppers to gain a foothold on infected devices. These would be small apps, with limited malicious behavior, but which would bypass Google's Play Store security checks, and later ask users for administrator rights.
If they'd convince users to grant them admin rights, these apps would download the real ransomware at later points.
Charger is quite sophisticated
With Charger this was different. Check Point says that the EnergyRescue app contained all the malicious code right from the get-go.
Despite putting all its code in one basket, researchers say that the Charger authors have done a good job at disguising the ransomware's malicious behavior.
For starters, they encoded all strings as binary arrays, making it hard to inspect the app, even by veteran security researchers.
Second, they loaded malicious code from encrypted resources, where Google's detection engine could not reach to inspect.
Third, they flooded the phone with useless commands, in order to hide malicious operations from a human's manual inspection.
Last, Charger also included code that would check if the app ran inside Android emulators, and stop the ransomware from triggering. This is most likely the feature that allowed Charger to bypass Bouncer, the Play Store's security scanner.
Read more: Charger Android Ransomware Reaches Google Play Store
Last edited by a moderator: