In this new ClickFix campaign, attackers send phishing emails that impersonate a hotel guest cancelling their Booking.com reservation, typically sent to a hospitality firm.
The claimed refund amount is significant enough to create a sense of urgency for the recipient of the email.

Clicking the link in the email takes the victim to a fake Booking.com website. "The page utilizes official Booking.com branding, including the correct color palette, logos, and font styles.
The site hosts malicious JavaScript that displays a fake "Loading is taking too long" error to the target, prompting them to click a button to refresh the page.

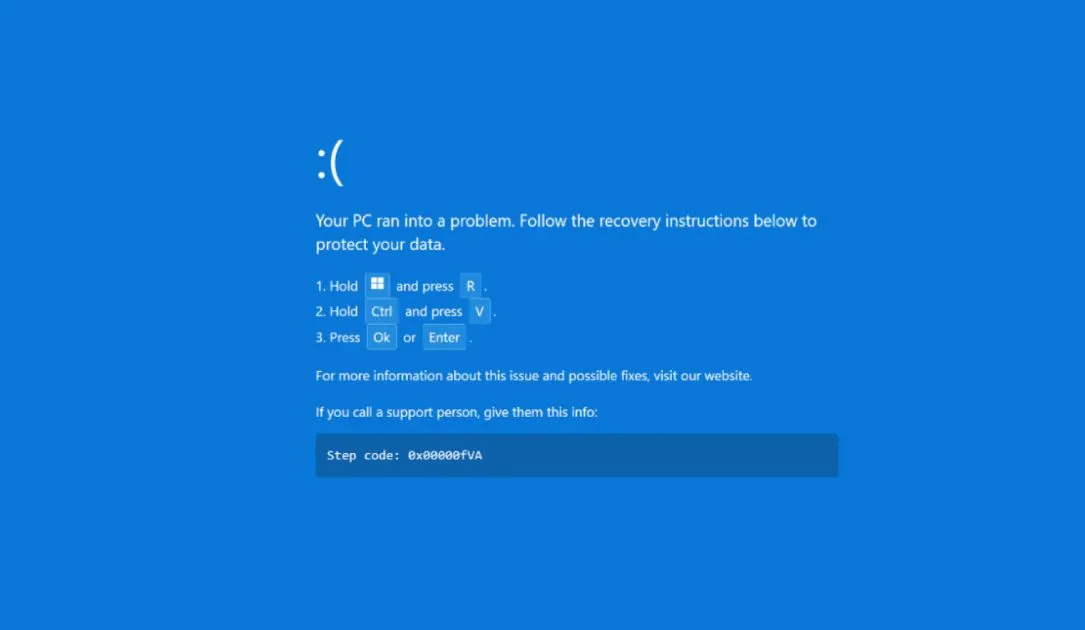
However, when the target clicks the button, the browser instead enters full-screen mode and displays a fake Windows BSOD crash screen that initiates the ClickFix social engineering attack.

The screen prompts the person to open the Windows Run dialog box and then press CTRL+V, which pastes a malicious command copied to the Windows clipboard.
The user is then prompted to press the OK button or Enter on their keyboard to execute the command.
Pasting the provided command runs a PowerShell command that opens a decoy Booking.com admin page. At the same time, in the background, it downloads a malicious .NET project (v.proj) and compiles it with the legitimate Windows MSBuild.exe compiler.
When executed, the payload adds Windows Defender exclusions and triggers UAC prompts to gain admin rights, before it downloads the primary loader using the Background Intelligent Transfer Service (BITS) and establishes persistence by dropping a .url file in the Startup folder.
The malware (staxs.exe) is DCRAT, a remote access Trojan commonly used by threat actors for remote access to infected devices.
Security News ClickFix attack uses fake Windows BSOD screens to push malware
- Thread starter Parkinsond
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It seems "Windows Defender exclusions" attracts the attention of a lot of malware.
A simple way to neutralize MD, but as mentioned, requires approving a prompt.It seems "Windows Defender exclusions" attracts the attention of a lot of malware.
Love it! Very well thought out!
Sadly that's one thing I am afraid of; one moment of being too tired combined with: "it could never happen to me because I know better! mentality" and poof I am infected.
Thankfully I never use a third party booking site. I got burnt in the past with Kayak and having to talk to Kayak vs the lady at the front desk. That wasted an extra 1 hour of my vacation time combined with frustration and feeling of hopelessness. No thank you. I would rather pay 10% more (if that) and deal directly with the vendor.
Sadly that's one thing I am afraid of; one moment of being too tired combined with: "it could never happen to me because I know better! mentality" and poof I am infected.
Thankfully I never use a third party booking site. I got burnt in the past with Kayak and having to talk to Kayak vs the lady at the front desk. That wasted an extra 1 hour of my vacation time combined with frustration and feeling of hopelessness. No thank you. I would rather pay 10% more (if that) and deal directly with the vendor.
A multitude of steps would have prevented this possibility of infection with a correct PC configuration.
So, from the outset, the fake Booking.com website was only HTTP..............
So, from the outset, the fake Booking.com website was only HTTP..............
Nice catch!!!!A multitude of steps would have prevented this possibility of infection with a correct PC configuration.
So, from the outset, the fake Booking.com website was only HTTP..............
Full Story:Suspected Russian cybercriminals are using a fake “Blue Screen of Death” page to target European hotels and hospitality companies with malware.
Researchers from Securonix said they have been tracking an ongoing malware campaign they call PHALT#BLYX, which typically starts with a lure centered around hospitality search engines.
The scheme starts with a fake reservation cancellation that impersonates a popular booking site, and eventually prompts victims with an error message and “Blue Screen of Death” page.
Russian hackers target European hospitality industry with ‘blue screen of death’ malware
The scheme starts with a fake reservation cancellation that impersonates a popular booking site, and eventually prompts victims with an error message and “Blue Screen of Death” page.
Users freak when they see BSD; being unable to think properly gives advantage to the malware process.Full Story:

Russian hackers target European hospitality industry with ‘blue screen of death’ malware
The scheme starts with a fake reservation cancellation that impersonates a popular booking site, and eventually prompts victims with an error message and “Blue Screen of Death” page.therecord.media
The "ClickFix" campaign is currently making the rounds, and it’s effectively weaponizing user panic against common sense. The attack starts with a garden-variety phishing email, usually pretending to be a Booking.com cancellation, that dumps you onto a cloned site which immediately throws a fake browser-based Blue Screen of Death. Instead of the usual reboot loop, this fake error screen helpfully offers a "fix" that involves opening the Windows Run dialog and pasting a script directly from your clipboard. If you follow these instructions, you aren't fixing a crash; you are manually executing a PowerShell script that bypasses local security controls to pull down the DCRAT trojan.
My bet is on this spreading fast because it shortcuts technical exploitation entirely, it simply convinces the user to open the front door themselves. The "error" isn't in the code, it's in the wetware operating the keyboard. If you see a website giving you specific technical instructions on how to run a script to "recover" your session, close the browser immediately. Microsoft isn't in the habit of asking users to paste random PowerShell commands to fix kernel panics, and treating a web page like IT support is exactly how you hand over the keys to your subnet.
My bet is on this spreading fast because it shortcuts technical exploitation entirely, it simply convinces the user to open the front door themselves. The "error" isn't in the code, it's in the wetware operating the keyboard. If you see a website giving you specific technical instructions on how to run a script to "recover" your session, close the browser immediately. Microsoft isn't in the habit of asking users to paste random PowerShell commands to fix kernel panics, and treating a web page like IT support is exactly how you hand over the keys to your subnet.
You may also like...
-
Security News New ErrTraffic service enables ClickFix attacks via fake browser glitches
- Started by Parkinsond
- Replies: 1
-
-
Security News Hackers Weaponize SVG Files and Office Documents to Target Windows Users
- Started by Brownie2019
- Replies: 2
-
Malware News Fake “Mac Cleaner” Campaign Uses Google Ads to Redirect Users to Malware
- Started by Brownie2019
- Replies: 3


