- Aug 17, 2014
- 11,108
A previously undocumented Windows malware has infected over 222,000 systems worldwide since at least June 2018, yielding its developer no less than 9,000 Moneros ($2 million) in illegal profits.
Dubbed "Crackonosh," the malware is distributed via illegal, cracked copies of popular software, only to disable antivirus programs installed in the machine and install a coin miner package called XMRig for stealthily exploiting the infected host's resources to mine Monero.
At least 30 different versions of the malware executable have been discovered between Jan. 1, 2018, and Nov. 23, 2020, Czech cybersecurity software company Avast said on Thursday, with a majority of the victims located in the U.S., Brazil, India, Poland, and the Philippines.
Crackonosh works by replacing critical Windows system files such as serviceinstaller.msi and maintenance.vbs to cover its tracks and abuses the safe mode, which prevents antivirus software from working, to delete Windows Defender (and other installed solutions) and turn off automatic updates.
As part of its anti-detection and anti-forensics tactics, the malware also installs its own version of "MSASCuiL.exe" (i.e., Windows Defender), which puts the icon of Windows Security with a green tick to the system tray and runs tests to determine if it's running in a virtual machine.
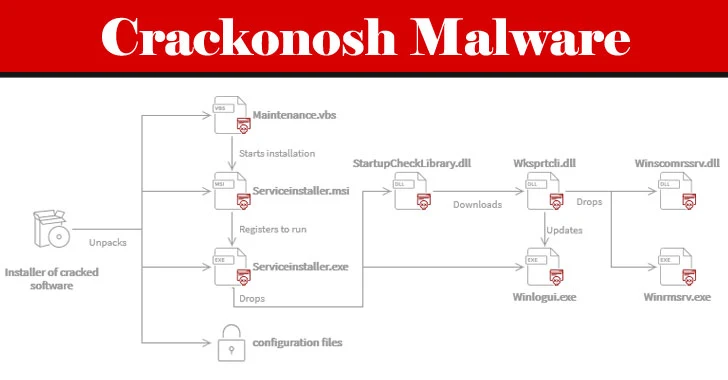
Crackonosh virus mined $2 million of Monero from 222,000 hacked computers
A malware called Crackonosh infected 222,000 PCs in order to mine $2 million worth of Monero cryptocurrency.
 thehackernews.com
thehackernews.com




