- Nov 15, 2016
- 867
Police Want More Help From Cryptocurrency Exchanges During Major Investigations

The value of a bitcoin has fallen from a high of around $20,000 last December, hovering on Thursday around the $10,000 mark. But despite bitcoin's volatility, cryptocurrencies remain a valuable tool for money laundering, law enforcement agencies warn.
See Also: IoT is Happening Now: Are You Prepared?
Europol, the EU's law enforcement intelligence agency, estimates that criminals in Europe generate $140 billion in illicit proceeds annually, of which about 3 or 4 percent - $4 billion to $6 billion - is being laundered via cryptocurrencies.
"It's growing quite quickly and we're quite concerned," Rob Wainwright, Europol's director, tells BBC Panorama (see Cybercriminals Go Cryptocurrency Crazy: 9 Factors).
Bitcoin isn't the only cryptocurrency used not just by law-abiding virtual currency aficionados but by those involved in illegal activities. Europol's most recent Internet Organized Crime Threat Assessment warned: "While the abuse of bitcoin remains a key enabler for criminal conduct on the internet, a number of other cryptocurrencies are beginning to emerge in the digital underground," including monero, ethereum and zcash.
Security experts say that bitcoin's recent price volatility has led many cybercrime gangs to drop bitcoin in favor of these and other alternatives, including litecoin, dash and bitcoin cash (see Bitcoin's Reign on the Dark Web May Be Waning).
Services Help Clean Coins
Proceeds from online crime are not the only ill-gotten gains to be laundered using cryptocurrencies, police say. Wainwright estimates that proceeds "in the billions" from sales of street drugs in Europe are being laundered by being converted into cryptocurrency.
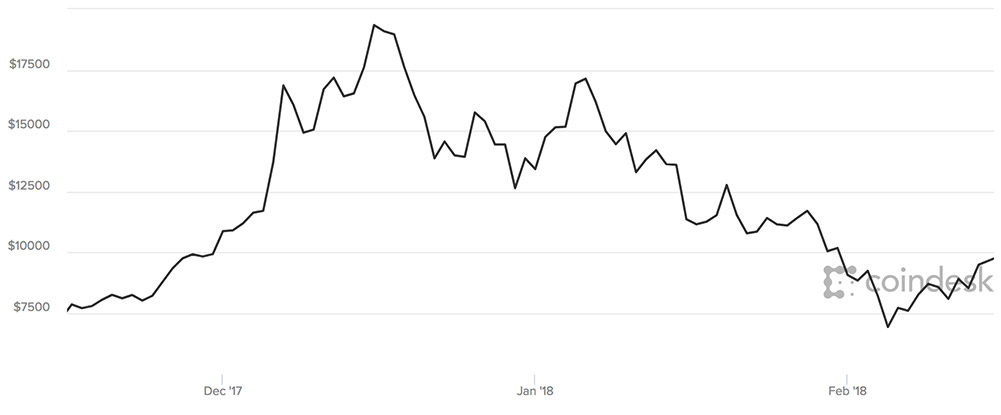
The U.S. dollar value of a bitcoin over the past three months. (Source: Coindesk)
One way to launder cryptocurrency is by using bitcoin tumbling, aka "bitcoin mixing," services or techniques. Such services offer to "clean coins" by trying to obscure the address from which bitcoins originated and where they ultimately end up. To do that, they split cryptocurrency into small amounts and try to shuttle it between many different wallets. As there's no trusted "Consumer Reports" for these services, it's unclear how effective they might be.
Wainwright says that at some stage of the laundering process, money mules - individuals recruited to move illicit proceeds from one location or account to another - may be exploited to receive the bitcoins and convert them into cash. "It's very difficult for the police in most cases to identify who's actually cashing this out," he says (see Don't Be a Money Mule for the Holidays).
Of course, many law enforcement officials love to talk about how advances in technology make their jobs harder. Two FBI directors in quick succession have lamented their inability to eavesdrop on end-to-end encrypted messaging, arguing that services should weaken their cryptography so outsiders can listen in. But law enforcement officials rarely mention that the explosion of smartphones, websites and massive quantities of data on individuals have enabled automated surveillance on a heretofore unprecedented scale.
Mass surveillance capabilities, in fact, may give law enforcement agencies even more useful and actionable information about suspects.
Anonymity: No Silver Bullets
Bitcoins aren't truly anonymous, but rather pseudonymous, and researchers continue to find and develop new tools that would allow law enforcement agencies to use "big data" techniques to help unmask users, helped in part by all bitcoin transactions being logged on the public blockchain.
A paper published last month, "Deanonymizing Tor Hidden Service Users Through Bitcoin Transactions Analysis," reports that users of the Tor anonymizing browser can be deanonymized if they pay for anything using bitcoin. "In a real-world experiment, we were able to link many users of Twitter and the BitcoinTalk forum to various hidden services, including WikiLeaks, Silk Road, and The Pirate Bay," researchers from Doha-based Qatar University and Qatar Computing Research Institute write.
Any missteps today could also lead to unmasking in the future. "Due to its pseudonymity model, bitcoin lacks retroactive operational security, which means historical pieces of information could be used to identify a certain user," the Qatari researchers write.
Secret Operations Remain Tough
As that suggests, the odds of cryptocurrency users being able to operate anonymously over the long term may not be great.
But this should be no surprise. "Maintaining a strong security posture (i.e. 'good OPSEC') for long periods of time is very stressful, even for professionally trained espionage officers," writes the operational security expert known as the Grugq.
Cryptocurrency offers no anonymity silver bullet. Furthermore, practicing great OPSEC requires patience and the ability to move slowly - two attributes that few would associate, for example, with darknet buyers and sellers of hard drugs, cybercrime tools or stolen payment card data (see Glove Use Key to Arrest of Alleged Darknet Drug Trafficker).
Criminals only need to make one mistake at some point in time. Authorities, meanwhile, get to play a long game, waiting until they have enough information to unmask suspects (see Poor OPSEC Led to Spyware Developer's Downfall).
But as with cybercrime, just because an intelligence agency might be able to identify who's sitting behind a keyboard, that doesn't mean they could arrest or extradite the suspect. Of course, law enforcement agencies can also be patient and wait for suspects to enter favorable jurisdictions, which from an OPSEC standpoint would count as another mistake (see Hackers' Vacation Plans in Disarray After Prague Arrest).
Push for Information Sharing
Regardless of whatever money tracking capabilities they may have, police say that it's difficult to trace the flow of cryptocurrency. Wainwright tells the BBC that cryptocurrency exchanges remaining unregulated and often not subject to information-sharing requirements poses a challenge. "They're not banks and governed by a central authority so the police cannot monitor those transactions," he says. "And if they do identify them as criminal, they have no way to freeze the assets unlike in the regular banking system."
Accordingly, he's called on exchanges to "take a responsible action and collaborate with us when we are investigating very large-scale crime." He's also called on regulators and legislators to help, especially to protect consumers.
"We need the help of regulators; we need the help of legislators, particularly to crack down on these high-value investment scams and this trend of fool's gold, effectively, that is offered to people as they seek to cash in on the bitcoin frenzy," he says. "Because it's not regulated, there's no means by which the investor can make an informed decision about, is it safe to invest my money in this?"
Who's Monitoring Transactions?
Cryptocurrency scams continue. On Thursday, German newspaper Die Presse reported that 10,000 Austrians had fallen victim to an alleged scam run by a firm called Optioment that cost victims up to 12,000 bitcoins, which at current market rates would be worth $120 million. Bloomberg reports that police are seeking suspects in Denmark, Latvia and Germany.
Behind the scenes, however, there's likely much more transaction monitoring occurring than governments have acknowledged, in the name of tracking not only terrorism but also organized crime.
The Shadow Brokers leaks, for example, revealed at least one apparent effort by the National Security Agency to hack into SWIFT "service bureaus" in the Middle East and spy on their customers' money moving activities.
Many cryptocurrency exchanges continue to get hacked, suggesting that their information security defenses are not robust enough to withstand assaults by cryptocurrency-craving criminals (see Cryptocurrency Infrastructure Flaws Pose Bitcoin Risks). Of course, intelligence agencies have even more resources and expertise to bring to bear. So it's a fair bet that the NSA, Britain's GCHQ and other intelligence agencies are camped out in multiple cryptocurrency exchanges, gathering data on users' transactions. For criminals attempting to hide their activities by using cryptocurrencies, time may not be on their side.
