- Jul 27, 2015
- 5,458
A critical vulnerability patched 10 days ago in widely used email software from IT security company Barracuda Networks has been under active exploitation since October. The vulnerability has been used to install multiple pieces of malware inside large organization networks and steal data, Barracuda said Tuesday.
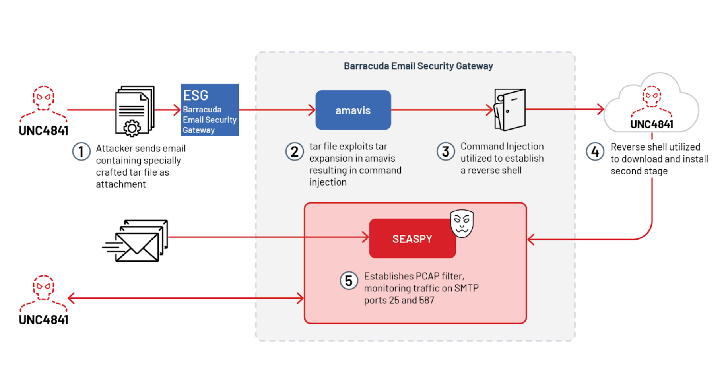
The software bug, tracked as CVE-2023-2868, is a remote-command injection vulnerability that stems from incomplete input validation of user-supplied .tar files, which are used to pack or archive multiple files. When file names are formatted in a particular way, an attacker can execute system commands through the QX operator, a function in the Perl programming language that handles quotation marks. The vulnerability is present in the Barracuda Email Security Gateway versions 5.1.3.001 through 9.2.0.006; Barracuda issued a patch 10 days ago. On Tuesday, Barracuda notified customers that CVE-2023-2868 has been under active exploitation since October in attacks that allowed threat actors to install multiple pieces of malware for use in exfiltrating sensitive data out of infected networks. “Users whose appliances we believe were impacted have been notified via the ESG user interface of actions to take,” Tuesday’s notice stated. “Barracuda has also reached out to these specific customers. Additional customers may be identified in the course of the investigation.”
Malware identified to date includes packages tracked as Saltwater, Seaside, and Seaspy. Saltwater is a malicious module for the SMTP daemon (bsmtpd) that the Barracuda ESG uses. The module contains backdoor functionality that includes the ability to upload or download arbitrary files, execute commands, and provide proxy and tunneling capabilities. Seaside is an x64 executable in ELF (executable and linkable format), which stores binaries, libraries, and core dumps on disks in Linux and Unix-based systems. It provides a persistence backdoor that poses as a legitimate Barracuda Networks service and establishes itself as a PCAP filter for capturing data packets flowing through a network and performing various operations. Seaside monitors tracking on port 25, which is used for SMTP-based email. It can be activated using a “magic packet” that’s known only to the attacker but appears innocuous to all others.

Critical Barracuda 0-day was used to backdoor networks for 8 months
Attackers then went on to steal data from infected systems.
 arstechnica.com
arstechnica.com