- Jun 9, 2013
- 6,720
Miner-C now specifically targets Seagate Central NAS hard drives
This same functionality is still present in the latest Miner-C version, but security researchers from Sophos say that recent Miner-C iterations are using a design flaw in the Seagate Central NAS devices to place a copy of itself on their public data folders.
NAS devices, which are network-connected hard drives, allow users to access files from the local network, but also via the Internet if the administrator chooses to open the NAS drive for remote access.
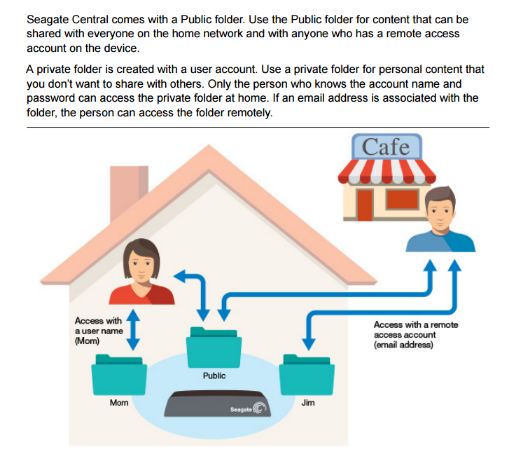
According to Sophos, Seagate Central devices contain a public folder accessible to all users, even anonymous non-logged-in users, which can't be deactivated or deleted.
Miner-C tricks users into installing the cryptocurrency miner
Miner-C is copying files to this public folder on all Seagate Central NAS devices it can find. One of the files it copies is called Photo.scr, a script file that malware coders have modified to use a standard Windows folder icon.
Because Windows has a bad habit of hiding file extensions, whenever the device owner accesses their NAS, they see this file as a folder, fooled by the fake icon.
When they try to access the folder, they're actually executing the Photo.scr file, which installs a cryptocurrency mining application on their PC.
Full Article. Cryptocurrency Mining Malware Discovered Targeting Seagate NAS Hard Drives
This same functionality is still present in the latest Miner-C version, but security researchers from Sophos say that recent Miner-C iterations are using a design flaw in the Seagate Central NAS devices to place a copy of itself on their public data folders.
NAS devices, which are network-connected hard drives, allow users to access files from the local network, but also via the Internet if the administrator chooses to open the NAS drive for remote access.
According to Sophos, Seagate Central devices contain a public folder accessible to all users, even anonymous non-logged-in users, which can't be deactivated or deleted.
Miner-C tricks users into installing the cryptocurrency miner
Miner-C is copying files to this public folder on all Seagate Central NAS devices it can find. One of the files it copies is called Photo.scr, a script file that malware coders have modified to use a standard Windows folder icon.
Because Windows has a bad habit of hiding file extensions, whenever the device owner accesses their NAS, they see this file as a folder, fooled by the fake icon.
When they try to access the folder, they're actually executing the Photo.scr file, which installs a cryptocurrency mining application on their PC.

Full Article. Cryptocurrency Mining Malware Discovered Targeting Seagate NAS Hard Drives
