Web Injects, Malware, Phishing and Fake Advertising Used in Attack Arsenal
Attackers continue to socially engineer cryptocurrency users by tricking them into visiting malicious sites such as "blockchaina.info," pictured. (Source: Cisco Talos)
Criminals continue their quest for acquiring cryptocurrencies without having to buy and manage their own mining equipment. They're resorting to attacks aimed at stealing the cryptocurrencies via hacking, demanding them as ransom payments as well as sneaking cryptocurrency mining software onto servers to generate virtual currencies (see Cybercriminals Go Cryptocurrency Crazy: 9 Factors).
See Also: IoT is Happening Now: Are You Prepared?
Not coincidentally, attackers' insatiable thirst for cryptocurrencies has paralleled the increasing value of bitcoin and other digital currencies.
Last July, a bitcoin was worth about $2,500, but by December had reached $13,800. Even though the value has declined somewhat since then, it's still hovering around $11,000.
Source: Trend Micro
"That steep and quick increase apparently prompted cybercriminals to target cryptocurrency through different methods," according to security firm Trend Micro. "Some used social engineering attacks to directly target cryptocurrency wallets, while others evolved old ransomware threats to do the same. There were even attempts to mine cryptocurrency through mobile malware, despite the improbability of gaining any substantial amount by that means."
Criminals operating online typically attempt to steal the greatest amount possible for the least amount of effort. Increasingly, that means targeting cryptocurrency. "In 2017, at least four advanced criminal groups shifted resources away from their bank hacking activities and directed them towards hacking bitcoin and cryptocurrency exchanges instead," Avivah Litan, a vice president and distinguished analyst at Gartner Research, says in a blog post, citing research from Israeli consultancy Diskin Advanced Technologies. "It's already working." (see Cryptocurrency Infrastructure Flaws Pose Bitcoin Risks).
Many criminals, however, aren't inventing new attack techniques. "In 2018, the groups are continuing these cryptocurrency hack efforts using the same old techniques they have successfully used for over a decade, albeit modified for the specifics of the cryptocurrency exchange websites and servers, and the customer authentication processes they employ," Litan says.
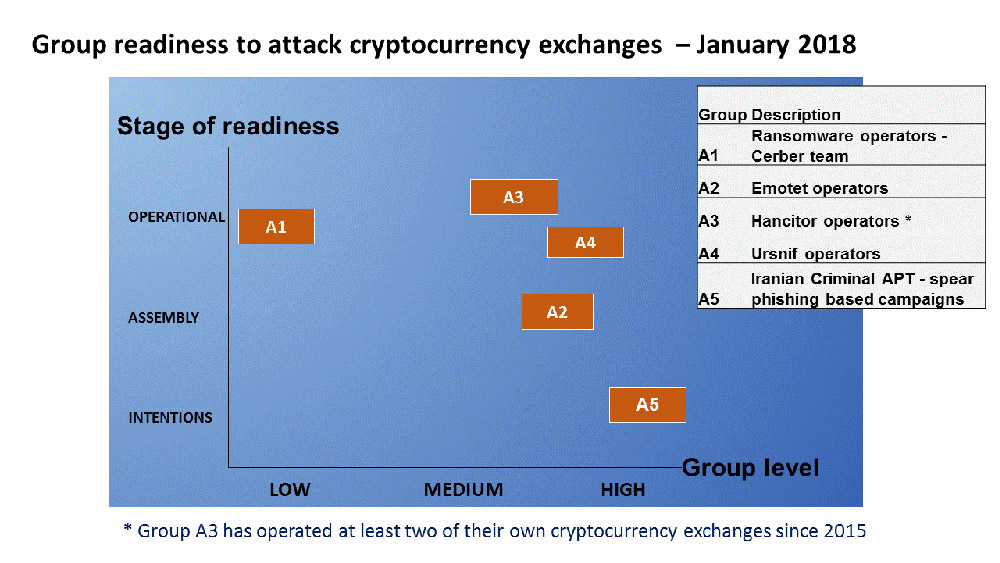
Source: Diskin Advanced Technologies
The biggest apparent heist to date occurred last month, when attackers stole $530 million from Japan's Coincheck exchange (see Japanese Cryptocurrency Exchange Suffers $530 Million Theft).
Many of these attacks appear to trace to cash-strapped North Korea. By some estimates, one-third of its gross domestic product may come from hacking (see Lazarus Hackers Phish For Bitcoins, Researchers Warn).
Old Trojan Tricks, New Targets
Malware operators are also getting in the game.
In August, the developers behind the Trickbot Trojan updated their malware to launch web injection attacks against users of cryptocurrency exchanges, including Coinbase. Web injections, or "man in the browser" attacks, are designed to activate when a user visits a specified website, such as a cryptocurrency exchange. The malware can intercept a user's keystrokes and also alter the browser interface to disguise attacker activity, such as draining a user's account of all funds.
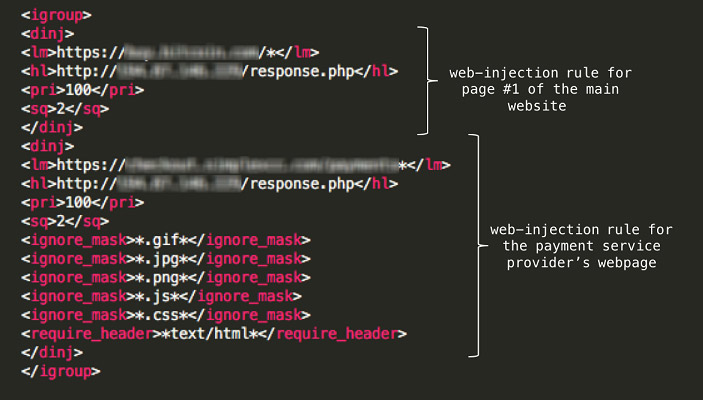
Attack rules in Trickbot's configuration file. (Source: X-Force Research)
In the case of Trickbot, the malware does that by tricking users into believing they're transferring purchased bitcoins to their own wallet, when in fact, it gets redirected to an attacker-controlled wallet, IBM's X-Force Research team reported earlier this month.
"In the normal payment scenario, a user looking to buy coins provides his or her public bitcoin wallet address and specifies the amount of bitcoin to purchase. When submitting this initial form, the user is redirected from the bitcoin exchange platform to a payment gateway on another domain, which is operated by a payment service provider. There, the user fills in his or her personal information, as well as credit card and billing details, and confirms the purchase of coins," the X-Force researchers write.
"This is where TrickBot hijacks the coins. This particular attack targets both the bitcoin exchange website and that of the payment service to grab the coins and route them to an attacker-controlled wallet."
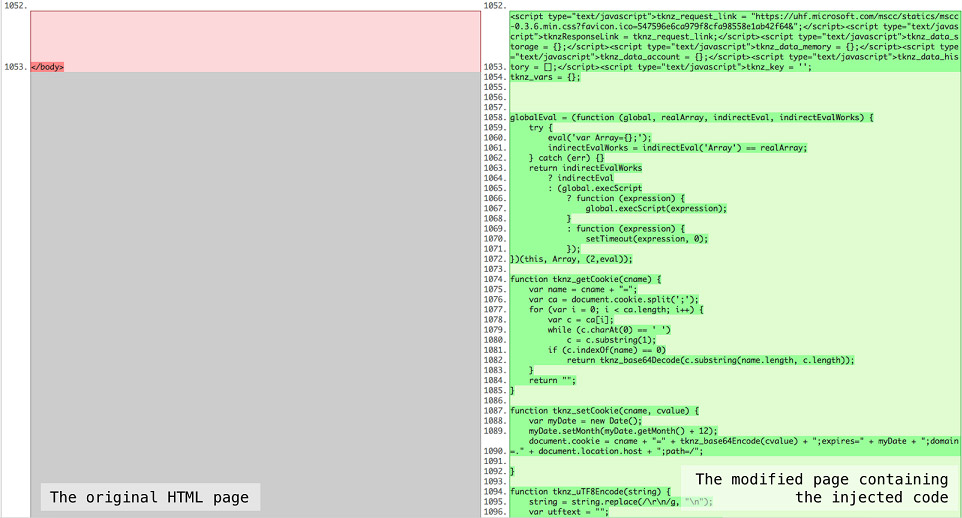
Difference between original HTML page and one returned by Trickbot. (Source: X-Force Research)
Phishing for Bitcoins
Social engineering attackers are also targeting cryptocurrency.
Researchers at Cisco's Talos security group have identified a malicious advertising campaign they dub Coinhoarder, which appears to be based out of Ukraine and to have netted about $50 million in the past three years, including $10 million alone in the last three months of 2017.
For this campaign, which began last February, the researchers say attackers purchased Google Adwords to "poison user search results" and direct them to attacker-controlled phishing sites designed to separate them from their cryptocurrency.
"Cisco identified an attack pattern in which the threat actors behind the operation would establish a 'gateway' phishing link that would appear in search results among Google Ads," the Cisco Talos researchers say. "When searching for crypto-related keywords such as 'blockchain' or 'bitcoin wallet,' the spoofed links would appear at the top of search results. When clicked, the link would redirect to a 'lander' page and serve phishing content in the native language of the geographic region of the victim's IP address."
At one point last February, Cisco reports that DNS queries for the gang's fake cryptocurrency sites exceeded 200,000 queries per hour. A significant number of them came from Nigeria, Ghana and Estonia, leading researchers to suggest that attackers were attempt "to target potential victims African countries and other developing nations where banking can be more difficult, and local currencies much more unstable compared to the digital asset."
Cisco says it's been sharing intelligence on the operation with Cyberpolice Ukraine.
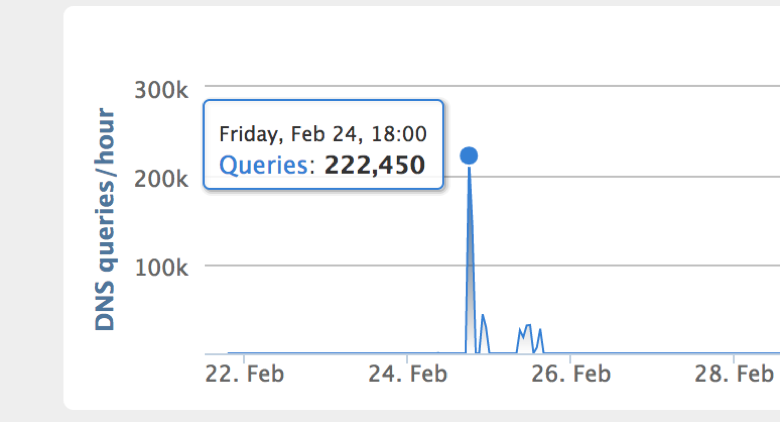
DNS queries for "block-clain.info" domain. (Source: Cisco Talos)
Many of the phishing sites use real-looking but fake domain names - referred to as "typosquatting" or brand spoofing - for example featuring a word such as "blockclain" - instead of "blockchain" - in the URL, Cisco says. Such typos could be especially effective on users whose first language is not English or for anyone who's using a mobile device, researchers say.
More recently, Cisco Talos reports that attackers have been refining their campaign by making their phishing sites look more legitimate. "A few months after we began tracking this particular group, we observed them starting to use SSL certs issued by Cloudflare and Let's Encrypt," the researchers say."SSL certificate abuse has been a rising trend among phishing campaigns in general." (See Darknet Vendors Sell Counterfeit TLS Certificates).
Mining Malware Surges
Meanwhile, attacks aimed at infecting systems with cryptocurrency mining software continue.
Earlier this month, security vendor Check Point Software reported that three cryptocurrency mining applications - Coinhive, Crytoloot and Rocks - are now among the top 10 most-seen malware families even though the code itself isn't malware (see Cryptocurrency Miners Crash Malware 'Top 10').
Other security firms report similar results. "Ever since September 2017, malicious cryptomining has been our top detection overall," says Jérôme Segura, lead malware intelligence analyst at security firm Malwarebytes.
In December 2017, security firm Imperva reports, 88 percent of all hack attacks that execute arbitrary code on targeted servers "sent a request to an external source to try to download a crypto-mining malware."
Miners Target EternalBlue
Last year, the WannaCry "ransom-worm" spread quickly by exploiting the Windows SMB_v1 flaw known as EternalBlue (CVE-2017-0144). Both U.S. and U.K. intelligence agencies have blamed the Pyongyang-based government of North Korea for WannaCry.
But before the May 2017 version of WannaCry that targeted EternalBlue appeared, the flaw was targeted by the Adylkuzz botnet to mine for monero Before WannaCry, Cryptocurrency Miners Exploited SMB Flaw).
Since last May, the operators of another botnet called Smominru have been doing the same, targeting EternalBlue as well as EsteemAudit (CVE-2017-0176), a smart card authentication code flaw that can be exploited on Windows systems that have remote desktop protocol enabled.
As of last month, the Proofpoint malware researcher known as Kafeine says in a blog post, Smominru "has earned millions of dollars for its operators" by running cryptocurrency mining malware on systems. It's not clear if the botnet operators are tied to the Adylkuzz botnet operators.
Kafeine says the greatest number of Smominru-infected nodes appear to be in Russia, India, Taiwan and Ukraine. Proofpoint reported the monero address tied to the botnet to MineXMR, a monero mining pool in which the attackers were participating.
"Mining pools are platforms that allow miners to work together and share computation resources to solve the puzzle," according to Imperva. "Once it is solved, the coins are divided between the participants of the pool according to how much computation power they each contributed."
But after being reported, Kafeine says the botnet operators appeared to register new addresses and resume their mining operations, directing the coins to a new address.
Enterprise Servers at Risk
Enterprises are especially at risk from these types of botnets, Kafeine says, noting that most of the infected endpoints appear to be Windows servers. "While monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators."
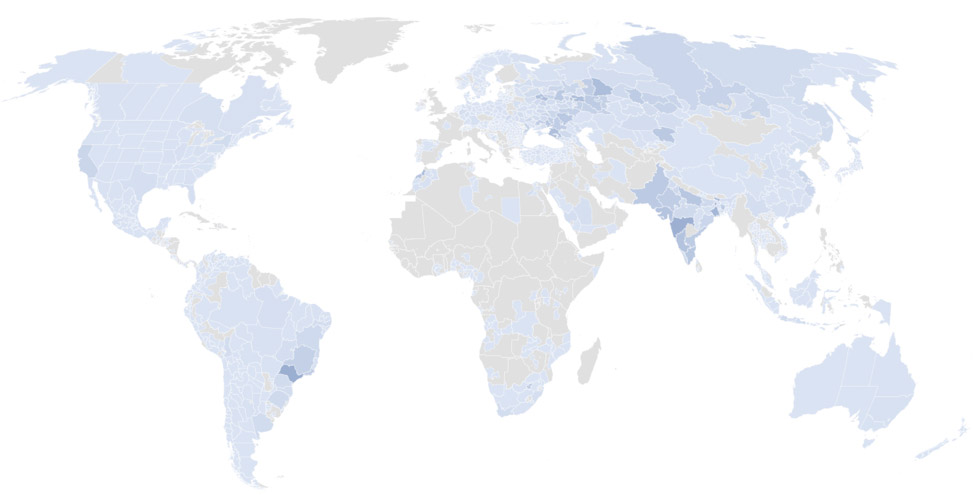
Concentration of Smominru nodes worldwide. (Source: Proofpoint)
Kafeine warns that enterprise resources are very much at risk from these types of attacks. "Because most of the nodes in this botnet appear to be Windows servers, the performance impact on potentially critical business infrastructure may be high, as can the cost of increased energy usage by servers running much closer to capacity," he writes. "Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes."
He adds that it's a virtual certainty that botnets such as Smominru will "become more common and to continue growing in size."
Bitcoin in Decline for Criminals?
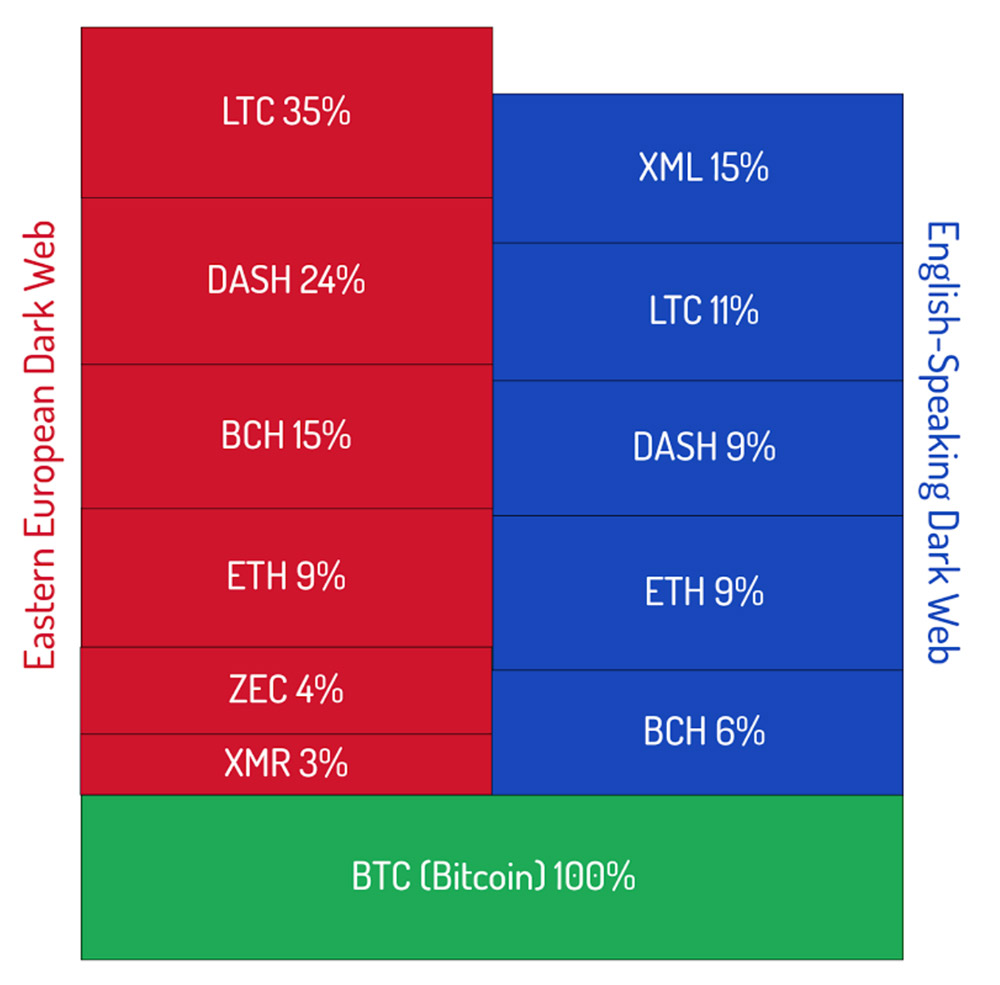
Review of 150 cybercrime forums finds all take bitcoin, and increasingly other cryptocurrencies too. (Source: Recorded Future)
But bitcoin's days as the cryptocurrency of choice for criminal transactions may be numbered.
Threat intelligence firm Recorded Future recently reviewed 150 underground markets and found that while all accept bitcoin, they're also increasingly supporting litecoin, monero, dash, bitcoin cash, ethereum and zcash.
The firm says that within the next 12 months, it expects bitcoin to no longer be the dominant payment mechanism for cybercrime service buyers and sellers (see Bitcoin's Reign on the Dark Web May Be Waning).