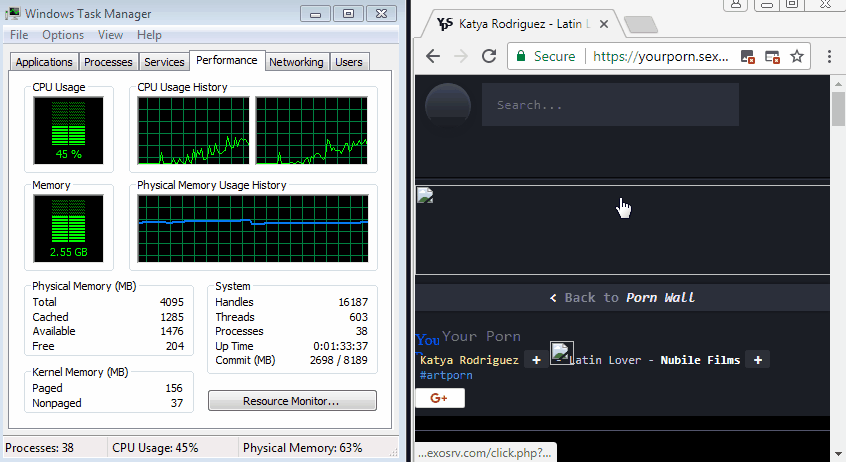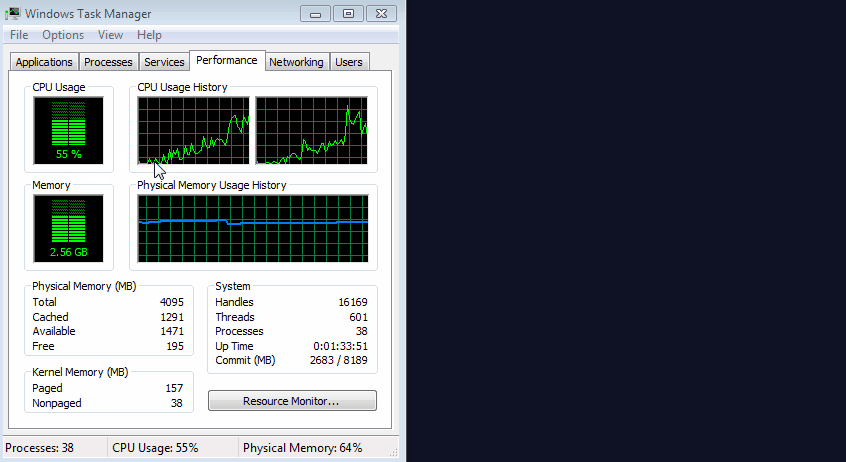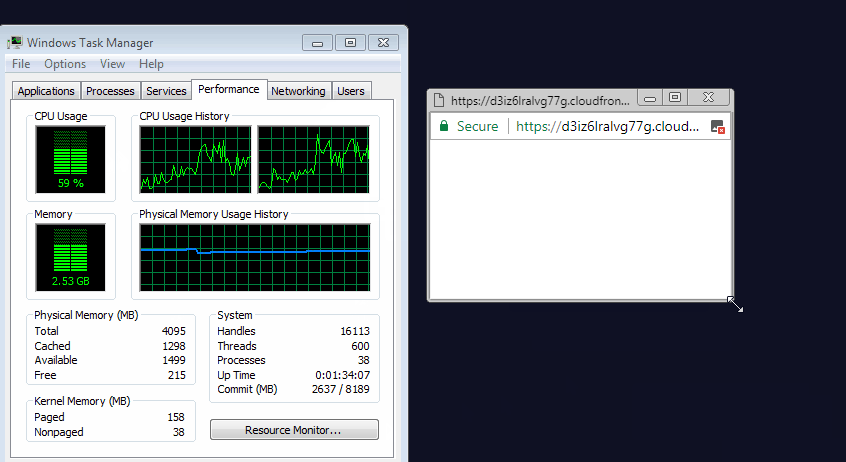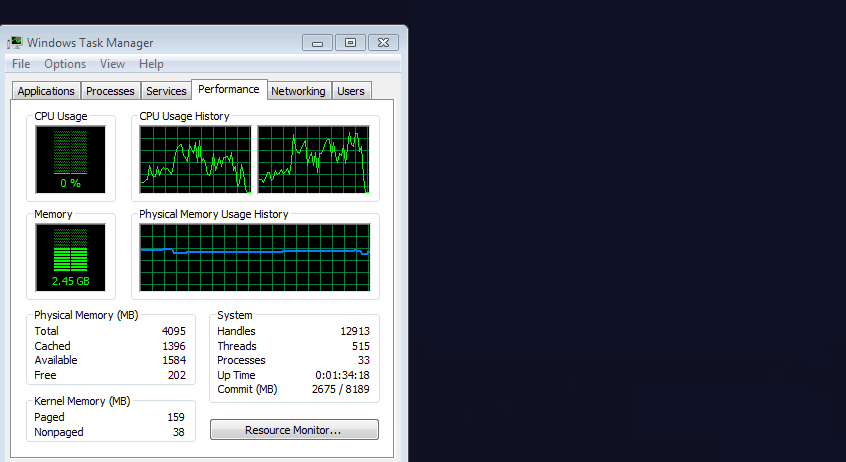
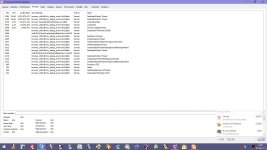
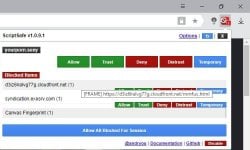
The operator of at least one website has been spotted using small windows hidden under the user's Windows taskbar to continue to operate an in-browser miner even after the user closed the main browser window.
Discovered by Malwarebytes researcher Jerome Segura, the miscreants behind this campaign utilize a tactic known as a pop-under, a trick that allows them to spawn a new window, separate from the main browser.
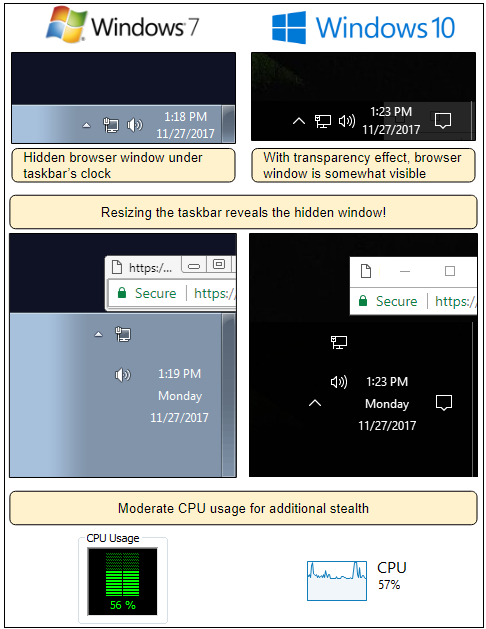
Site operator hid popup under Windows taskbar
JavaScript code also allows the abusive website owners to configure the size of this window and its coordinates (position) on the user's screen.
According to Segura, this website — an adult portal— used the following formula to dynamically calculate the position of this new window.
Horizontal position = (current screen width) – 100px
Vertical position = (current screen height) – 40px
For most users, this would display a tiny window hiding under the Windows taskbar. Crooks would then load
a JavaScript file inside this hidden window. This file is a customized version of the Coinhive in-browser miner, a script that would utilize the user's CPU resources to mine the Monero cryptocurrency for the crooks.