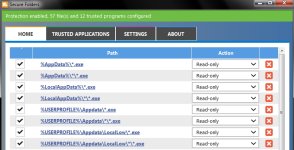
You have probably already heard about very well known type of virus called “Cryptolocker“.
Each day you can heard about new variant of Cryptolocker virus and based from my experience I can say that Antivirus vendors just can’t keep up with this kind of threat, because once downloaded Cryptolocker virus changes .exe file names and hashes so it is really hard to track it down.
Following recommendations will help you to protect your PC or your network from a Cryptolocker virus.
In order to prevent cryptolocker virus from activating and therefore start with the encryption of your files here’s what you can do if you are using Windows Professional or Enterprise versions of Microsoft Operating System.
Open local policy editor by running gpedit.msc and navigate to:
Computer Configuration | Windows Settings | Security Settings | Software Restriction Policies
From the action menu or using a right click select “New Software Restriction Policies”
Select Additional Rules and in the right pane right click and choose to create a New Path Rule.
Now add each of the following rules and set Security Level to “Disallowed“:
%AppData%\*.exe
%AppData%\*\*.exe
%LocalAppData%\*.exe
%LocalAppData%\*\*.exe
%USERPROFILE%\Appdata\*.exe
%USERPROFILE%\Appdata\*\*.exe
%USERPROFILE%\Appdata\LocalLow\*.exe
%USERPROFILE%\Appdata\LocalLow\*\*.exe
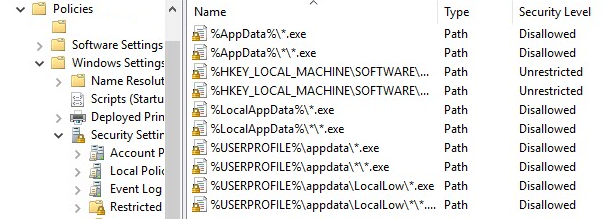
Once you’re done you should get this result:
Close policy editor and restart your machine.
With this policy in place you will prevent starting of executable files from directories that Cryptolocker mostly use.
If you work in a corporate environment you can link above created policy to your domain and thus prevent Cryptolocker from running.
Source
Each day you can heard about new variant of Cryptolocker virus and based from my experience I can say that Antivirus vendors just can’t keep up with this kind of threat, because once downloaded Cryptolocker virus changes .exe file names and hashes so it is really hard to track it down.
Following recommendations will help you to protect your PC or your network from a Cryptolocker virus.
- Do not use non-supported Operating System like Windows XP. Although you’ll be more protected using this guide, even if you use an outdated OS like Windows XP, we strongly recommend you to move forward and upgrade to a newer operating system. Microsoft no longer provides security updates or technical support for Windows XP.
- Use good Anti-Virus software protection and make sure your virus definitions are up to date.
- Use a third party Firewall or Windows Firewall.
- Use Windows User Account Control (UAC) in Admin approval mode. When the system or you initiates an .exe file it will ask you for consent or for a password if you are logged on as a standard user.
- Always work under Windows standard user account. Let Windows ask you for administrative credentials each time you try to install something.
In order to prevent cryptolocker virus from activating and therefore start with the encryption of your files here’s what you can do if you are using Windows Professional or Enterprise versions of Microsoft Operating System.
Open local policy editor by running gpedit.msc and navigate to:
Computer Configuration | Windows Settings | Security Settings | Software Restriction Policies
From the action menu or using a right click select “New Software Restriction Policies”
Select Additional Rules and in the right pane right click and choose to create a New Path Rule.
Now add each of the following rules and set Security Level to “Disallowed“:
%AppData%\*.exe
%AppData%\*\*.exe
%LocalAppData%\*.exe
%LocalAppData%\*\*.exe
%USERPROFILE%\Appdata\*.exe
%USERPROFILE%\Appdata\*\*.exe
%USERPROFILE%\Appdata\LocalLow\*.exe
%USERPROFILE%\Appdata\LocalLow\*\*.exe
Once you’re done you should get this result:
Close policy editor and restart your machine.
With this policy in place you will prevent starting of executable files from directories that Cryptolocker mostly use.
If you work in a corporate environment you can link above created policy to your domain and thus prevent Cryptolocker from running.
Source