silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,924
- 8,399
A new dropper-as-a-service (DaaS) cybercrime operation named 'SecuriDropper' has emerged, using a method that bypasses the 'Restricted Settings' feature in Android to install malware on devices and obtain access to Accessibility Services.
Restricted Settings is a security feature introduced with Android 13 that prevents side-loaded applications (APK files) installed from outside Google Play to access powerful features like the Accessibility settings and Notification Listener. The two permissions are commonly abused by malware, so the feature was intended to protect users by blocking the approval of requests by displaying a warning when these permissions are requested.
SecuriDropper infects Android devices posing as a legitimate app, most often impersonating a Google app, Android update, video player, security app, or a game, and then installing a second payload, which is some form of malware.
The dropper achieves this by securing access to the "Read & Write External Storage" and "Install & Delete Packages" permissions upon installation.
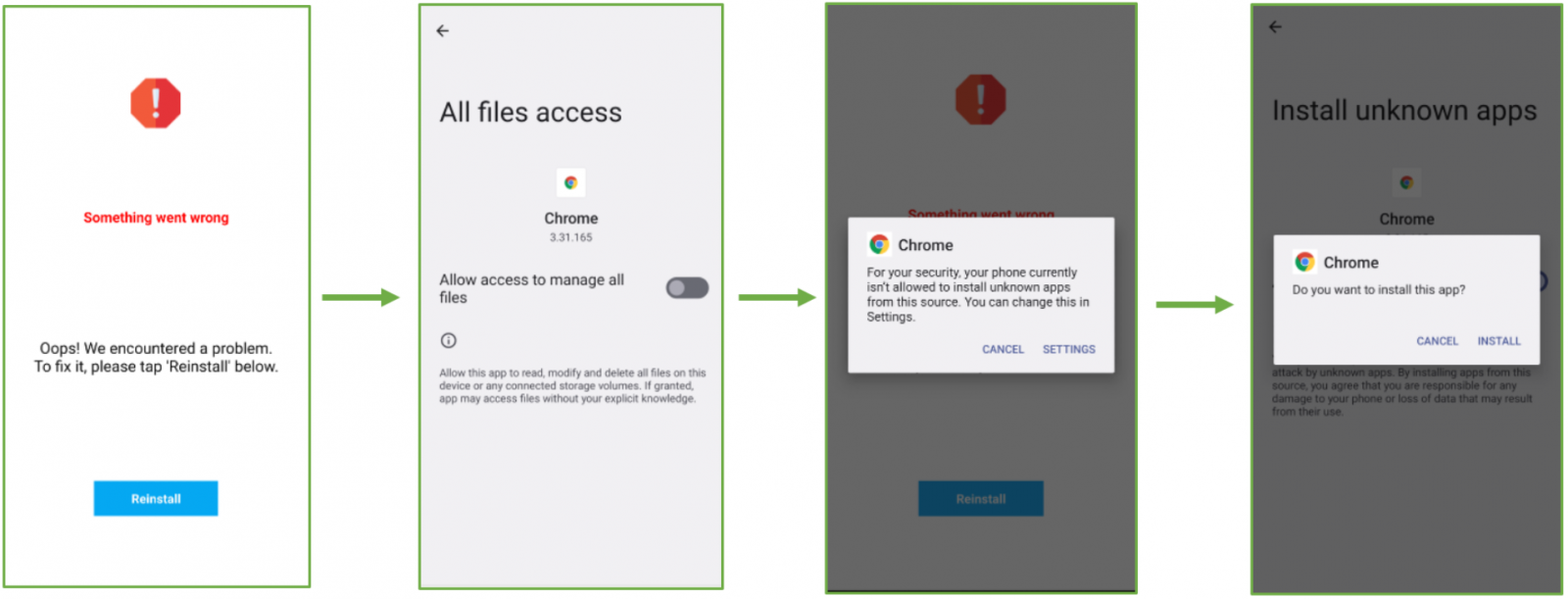
The second-stage payload is installed through user deception and interface manipulation, prompting users to click a "Reinstall" button after displaying bogus error messages about the dropper app's installation.
Payload dropping process (ThreatFabric)