- Aug 18, 2024
- 10
Hello, I am looking for advice regarding rootkits and hacking.
I have been dealing with this cyberstalker person for the past several years on and off. I have tried a lot of things, and to my surprise, I was not able to stop this person from tracking me down.
This led me to conclude that I might have been hacked or rootkitted. What would be the best remedies for dealing with this?
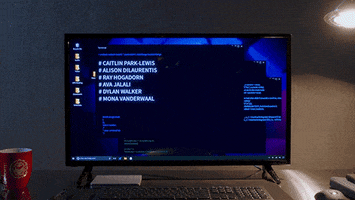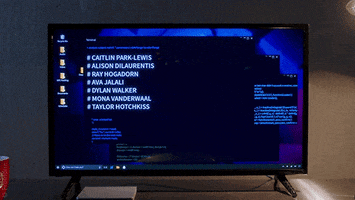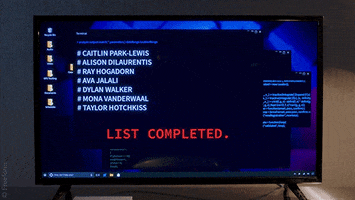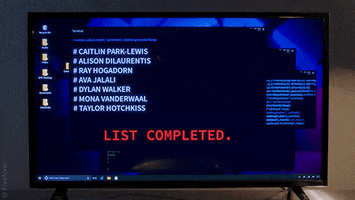
For further context, I met this person from an online gaming community in 2018. I am not exactly sure what mistakes I might have made since it was a long time ago, but I might have clicked on something?? I am not sure. After this, this person was able to track down on all of my computer activities, and by all I mean ALL, EVERYTHING. My private DMs with friends on Telegram, Discord, my phone number, personal files, photos, games I'm playing, all activities, information, emails, all social media accounts, EVERYTHING was found.
This cyberstalker uses her advantage of having complete spying of my system to torment me and harass me by inducing panic and anxiety through deliberate attempts where she would message me things from multiple fake accounts that ONLY I should know about. She also somehow found new accounts I have made on forums, social media sites, and I used random names and random email, and no signs of any accounts were ever compromised.
An example, say I was watching a very specific porn genre on my computer and have told no one about, since you know it is porn and the genre can be pretty nasty. This cyberstalker then sent subtle texts or messages from a random fake account about that kind of porn to mess with me, you know what I mean? These kinds of harassments.
Yes, I have contacted police, but they haven't considered my situation severe enough and have not taken actions. Which is why I am now trying to seek help online. Any experts here in rootkits?
At times, there were also strange symptoms on my PC, where it would suddenly wake up in middle of night while the display was off or asleep, and that also wakes me up, which is hella spooky. I did research online for a while, and a rootkit seems like the most accurate infection that I might have, nothing else seems out of the ordinary, no detections.
Things I have tried:
What should I do?
I have been dealing with this cyberstalker person for the past several years on and off. I have tried a lot of things, and to my surprise, I was not able to stop this person from tracking me down.
This led me to conclude that I might have been hacked or rootkitted. What would be the best remedies for dealing with this?
For further context, I met this person from an online gaming community in 2018. I am not exactly sure what mistakes I might have made since it was a long time ago, but I might have clicked on something?? I am not sure. After this, this person was able to track down on all of my computer activities, and by all I mean ALL, EVERYTHING. My private DMs with friends on Telegram, Discord, my phone number, personal files, photos, games I'm playing, all activities, information, emails, all social media accounts, EVERYTHING was found.
This cyberstalker uses her advantage of having complete spying of my system to torment me and harass me by inducing panic and anxiety through deliberate attempts where she would message me things from multiple fake accounts that ONLY I should know about. She also somehow found new accounts I have made on forums, social media sites, and I used random names and random email, and no signs of any accounts were ever compromised.
An example, say I was watching a very specific porn genre on my computer and have told no one about, since you know it is porn and the genre can be pretty nasty. This cyberstalker then sent subtle texts or messages from a random fake account about that kind of porn to mess with me, you know what I mean? These kinds of harassments.
Yes, I have contacted police, but they haven't considered my situation severe enough and have not taken actions. Which is why I am now trying to seek help online. Any experts here in rootkits?
At times, there were also strange symptoms on my PC, where it would suddenly wake up in middle of night while the display was off or asleep, and that also wakes me up, which is hella spooky. I did research online for a while, and a rootkit seems like the most accurate infection that I might have, nothing else seems out of the ordinary, no detections.
Things I have tried:
- Paid for antivirus softwares, multiples of them in fact.
- All kinds of virus scanners and tools.
- VPN
- Clean reinstall of Windows.
- Dual boot Linux.
What should I do?