A new wave of data leaks by the cybercriminal known as “Nam3L3ss” has surfaced, exposing sensitive employee information from some of the world's largest companies. The leaked databases, stemming from previous CL0P ransomware attacks exploiting the MOVEit vulnerability (CVE-2023-34362), include millions of records detailing corporate hierarchies, personal data, and internal identifiers.
The leaks, posted on a major cybercrime space ‘BreachForums,' mark an escalation in the fallout from the MOVEit vulnerability exploited previously. On November 11, the
threat actor published internal records from Amazon (confirmed authenticity), HSBC, MetLife, Cardinal Health, HP, Lenovo, and McDonald's.
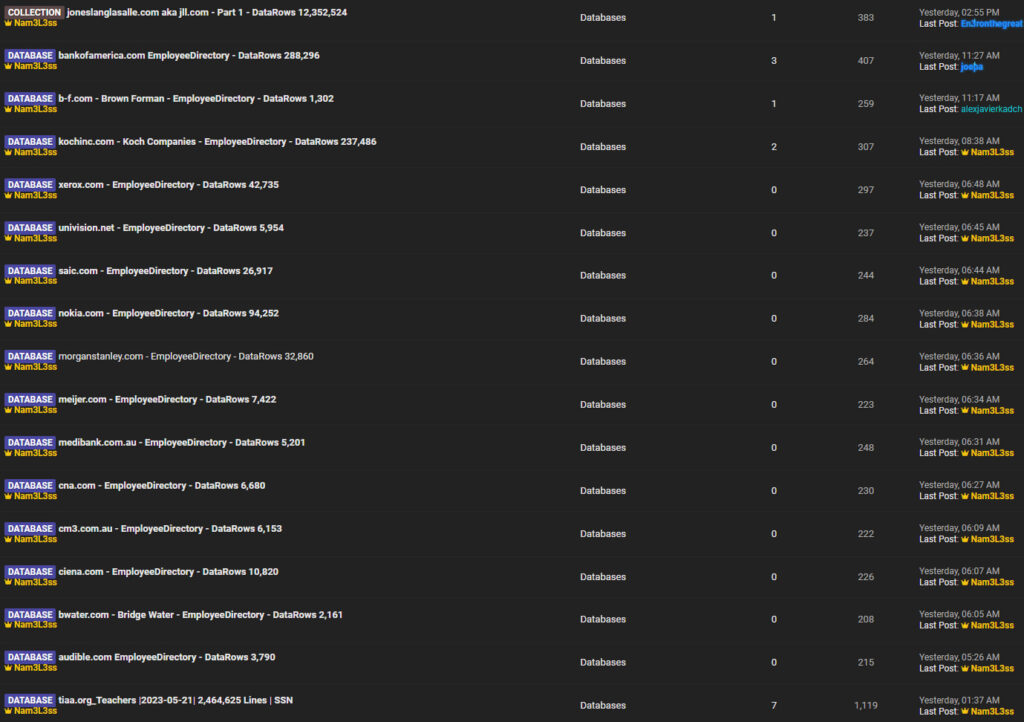
This latest round of exposures involves corporations across multiple industries, including finance, healthcare, technology, and real estate. Below is a summary of the most significant breaches in the latest wave:
- Jones Lang LaSalle (JLL): 12,352,524 records
- Koch Industries: 237,486 records
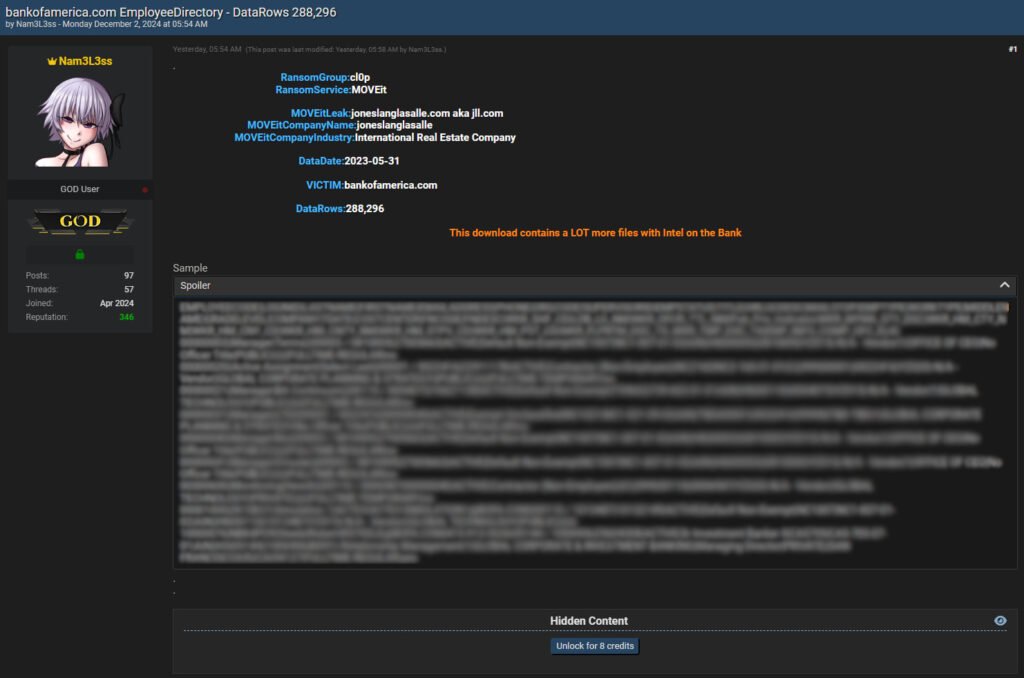
- Bank of America: 288,296 records
- Xerox: 42,735 records
- Morgan Stanley: 32,860 records
- Brown-Forman: 1,302 records
- Medibank (Australia): 5,201 records
Data leaks the threat actor posted yesterday
CyberInsider
These datasets contain sensitive employee information such as names, email addresses, phone numbers, cost center codes, department details, and job titles. In some cases, the records reveal highly detailed organizational structures, which could enable phishing attacks, corporate espionage, or identity theft. All records are available to registered forum members for 8 credits, which corresponds to a small amount in cryptocurrency.
Threat actor's motives
The breaches were linked to the CL0P ransomware group, which gained access to the exposed data earlier in 2023 during their exploitation of the MOVEit Transfer software vulnerability. Nam3L3ss, a prominent figure in the cybercrime world, has been systematically downloading and redistributing this data.
On his personal site, Nam3L3ss claims they are not directly affiliated with CL0P but rather aim to highlight the poor state of corporate data security. They described their role as a distributor of already-compromised information, stating:
“Everything I post, the criminal [world] already has on them… I am tired of Governments allowing Companies to SELL data on people.”
This statement echoes broader concerns about corporate data handling and privacy risks. Nam3L3ss says he is not interested in making money from redistributing the data but rather raising awareness and sending a message.
The consequences of publishing stolen data in structured form that makes it easily digestible and more usable are significant for victimized organizations and their workforce. Affecting entities could incur regulatory fines and investigations, litigation costs from class-action lawsuits, and extremely heightened phishing risks.