- Oct 23, 2012
- 12,527
Data breach indexing website LeakedSource has announced today that it received a data dump of 43,570,999 user records that were stolen in 2012 from music streaming service Last.fm.
London-based Last.fm admitted to the data breach in June 2012, when it also asked users to reset passwords.
According to timestamps in the data received by LeakedSource, the Last.fm data breach occurred on March 22, 2012, which is consistent with a GigaOM article from June 2012 that reported a similar timeline for the security breach.
Initial Last.fm data breach estimation was of 1.5 million
Last.fm said it started to investigate the incident after multiple users complained of spam in May 2012, and after a batch of 1.5 million user passwords ended up on a cryptography forum.
While Last.fm never revealed technical details of how the breach took place, some weak security measures were surely into play.
LeakedSource says it took them two hours to crack 96 percent of all the passwords included in the Last.fm data. This was possible because passwords used an unsalted MD5 hashing system.
Back on June 7, 2012, on the day after Last.fm asked users to reset passwords, a former Last.fm developer named Russ Garrett admitted on Twitter that passwords were hashed using MD5, a hashing function considered weak even before 2012.
London-based Last.fm admitted to the data breach in June 2012, when it also asked users to reset passwords.
According to timestamps in the data received by LeakedSource, the Last.fm data breach occurred on March 22, 2012, which is consistent with a GigaOM article from June 2012 that reported a similar timeline for the security breach.
Initial Last.fm data breach estimation was of 1.5 million
Last.fm said it started to investigate the incident after multiple users complained of spam in May 2012, and after a batch of 1.5 million user passwords ended up on a cryptography forum.
While Last.fm never revealed technical details of how the breach took place, some weak security measures were surely into play.
LeakedSource says it took them two hours to crack 96 percent of all the passwords included in the Last.fm data. This was possible because passwords used an unsalted MD5 hashing system.
Back on June 7, 2012, on the day after Last.fm asked users to reset passwords, a former Last.fm developer named Russ Garrett admitted on Twitter that passwords were hashed using MD5, a hashing function considered weak even before 2012.
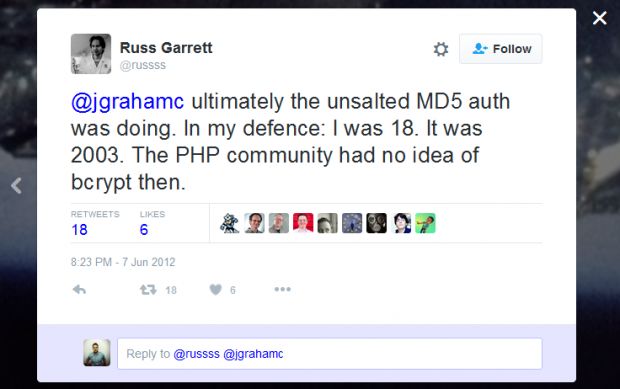
Russ Garrett tweet from 2012
According to LeakedSource, the Last.fm data contains a username, email address, password, join date, and internal Last.fm service data (campaign hits, banned users, newsletter details, used invites, web player details, and more).
Softpedia and a reporter from another publication who wanted to remain unnamed have helped LeakedSource verify the data's validity. The username-email-password combos Softpedia tested with LeakedSource belonged to Last.fm accounts for Softpedia employees dating back to circa 2012.
Softpedia was able to verify the data validity of some accounts, but not if the entire data belongs to active or actual Last.fm users. Some duplicate or bot accounts are bound to be included.
LeakedSource says it received the data from a user named after his Jabber ID, daykalif@xmpp.jp.
Last.fm is the latest addition to the list of recent mega breaches
Last.fm now joins the ranks of other major services that have been breached and their data dumped online, either on Dark Web marketplaces or into the vaults of data breach index services like LeakedSource.
Previously, services like Dropbox, Tumblr, LinkedIn, MySpace, VK, Mail.ru, Badoo, and others also suffered similar data breaches of epic proportions. Twitter users were also affected, but because malware infected their computers and logged their passwords. Twitter hasn't suffered a data breach, as far as we know.
Last.fm users can visit LeakedSource and see if their details are part of the compromised data. Users should reset passwords for all accounts where they used their Last.fm 2012 passwords.
Softpedia has reached out to Last.fm to inform the company about the data dump's ressurgence and for additional comment but has not received an answer in time for this article's publication.
