
Polish security researcher Hasherezade has found a way to help victims of the Princess Locker ransomware by cracking the ransomware's encryption system and releasing a free decryptor.
Princess Locker is a ransomware family that appeared at the end of September and was made available as a Ransomware-as-a-Service, rentable via a Dark Web portal.
The ransomware was never at the center of a massive distribution campaign, but the crooks behind it made some victims regardless, who remained locked out of their files.
Keygen and decrypter available for download
After spending a few days looking at the ransomware's mode of operation, Hasherezade announced yesterday on Twitter that she finally found a way to recover files locked by this threat.
The decryption package can be downloaded from this Google Drive page. The archive should contain the following files:
The two main files are PrincessKeygen and PrincessDecrypter. Both files are CLI tools, so you'll need to open a command-line interface (cmd.exe) and navigate to the folder where these two files are located.
The first one you should run is PrincessKeygen. As the name hints, this is a tool to extract the encryption key used to lock your files. To run this file, from a cmd.exe window inside the tool's folder, you should type the following command structure:
Code:
PrincessKeygen.exe [encrypted file] [original file] [added extension] [*unique id]Where:
[encrypted file] - the name of the encrypted file, which you must place in the same folder as the PrincessKeygen.exe file.
[original file] - the name of the same encrypted file, but in an unencrypted, original version, which as well, you must place in the same folder as the PrincessKeygen.exe file. You can recover these files from backups, older emails, or online file storage portals. One file is enough. In case you don't have an unencrypted copy of a locked file, you can use one of the sample files Hasherezade provided in the headers.zip file
[added extension] - the random characters added as file extensions at the end of each encrypted file
[unique id] - a random string of characters included in the ransom note at "Your ID." This is an optional parameter and Hasherezade says the keygen will work without it, but will take longer to produce results.
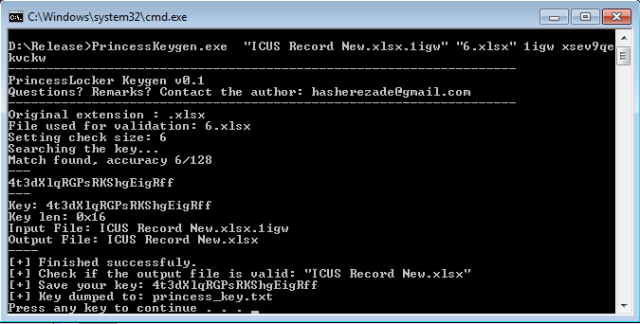
Using PrincessKeygen.exe (via Hasherezade)
Once you have the encryption key, you can move along to the decryption process. In a similar cmd.exe window, type in the following command:
Code:
PrincessDecryptor.exe [key] [added extension] [*file/directory]Where:
[key] - the key generated by the keygen
[added extension] - the random characters added as file extensions at the end of each encrypted file. Same as in the step before
[*file/directory] - optional parameter to decrypt certain files or certain folders only
Full article with video and in-depth analysis : Decryptor Available for Princess Locker Ransomware
Last edited: