L
LabZero
Thread author
Recently it was discovered a new botnet: It's name is DiamondFox, also known as Gorynch, is a botnet with various features.
The technical analysis is explained here: A Study in Bots: DiamondFox but it is very difficult to understand for an average user, so I tried to simplify it, so that everyone can understand the complexity of this botnet and its dangers.
Botnet control panel.
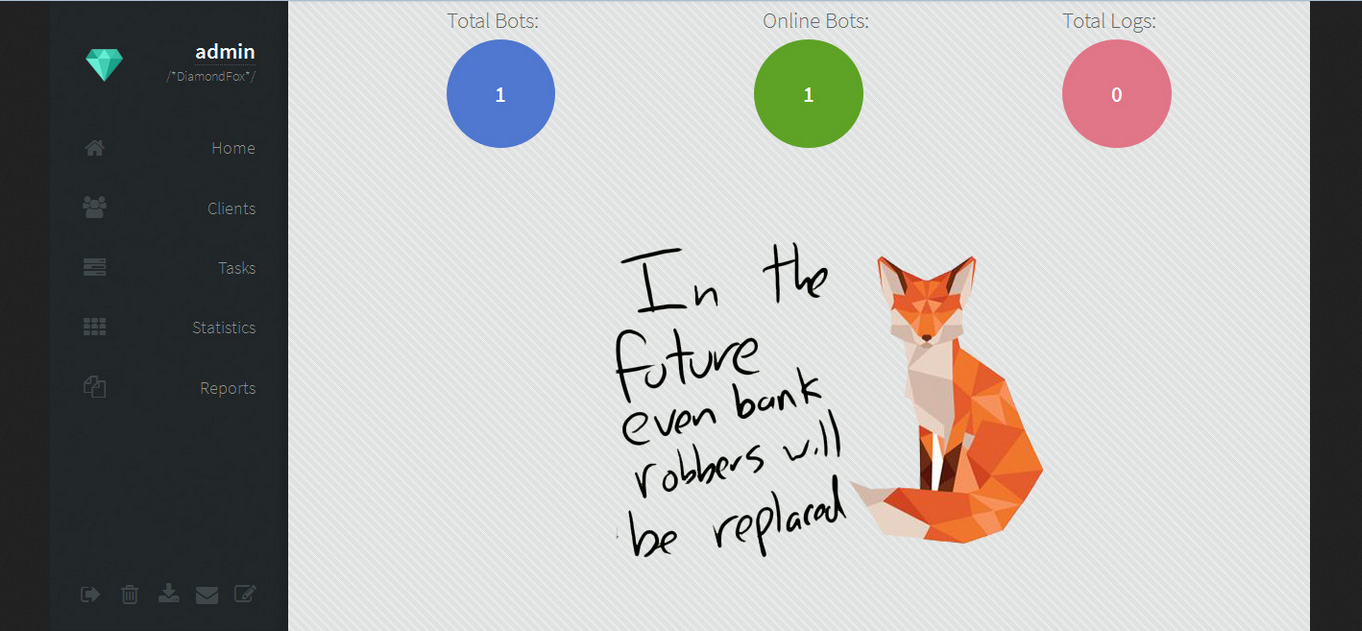
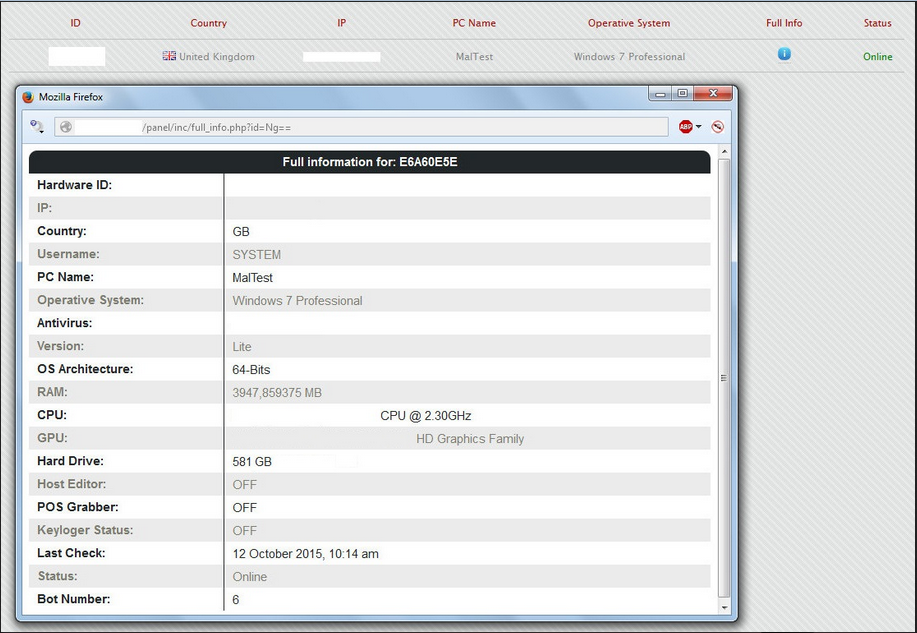
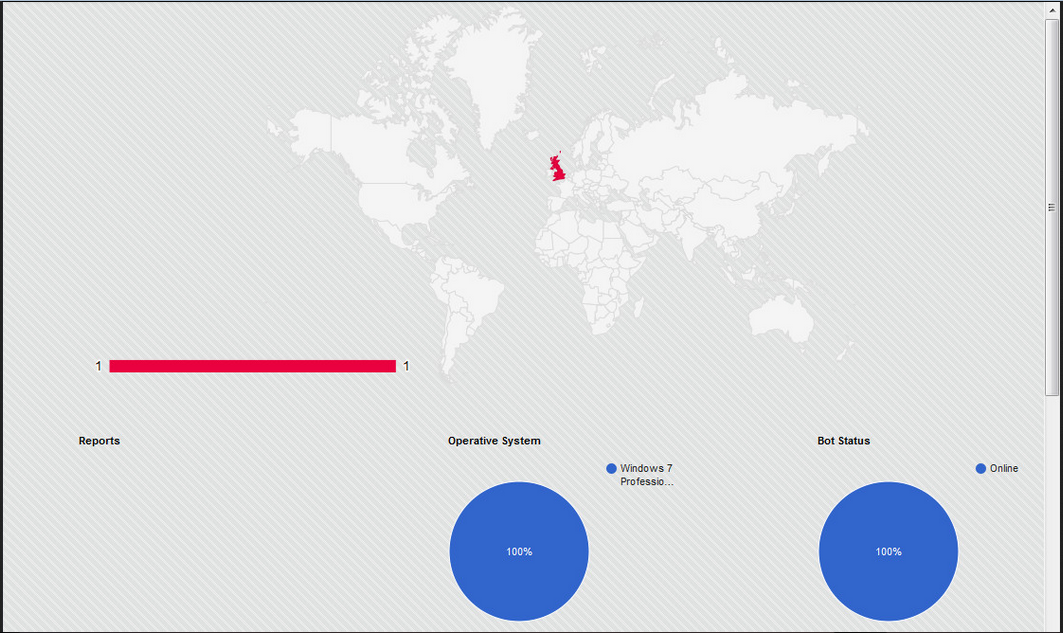
Malware is written in VB6, It has many functions inside, one of the most interesting is the scraper of cards, a form of bots that search the infected computer's RAM, generally a Point of Sale System (POS), the credit card data (number and CVV).
DiamondFox has quite a few features, some of which are listed here:
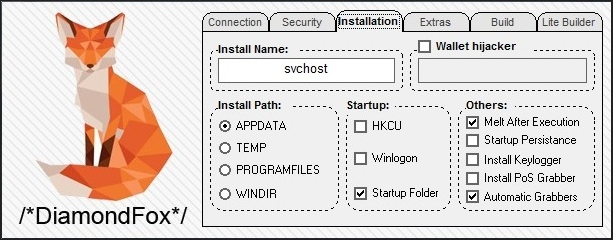
The malware infects these paths:
And the following options:
For HKCU registry, the following key is generated:
For the Winlogon, the path to the application DiamondFox is added to the following locations:
With the "Startup" Folder, DiamondFox is simply copied to the user's startup, renamed WordPad.exe.
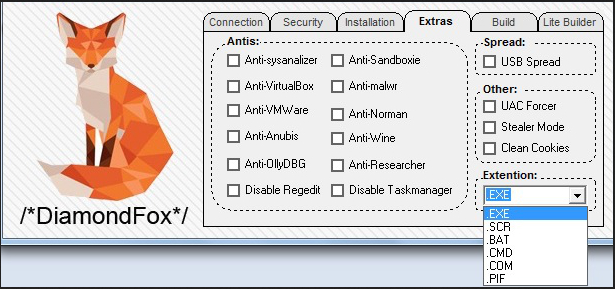
There are also anti-reversing features, to make it more difficult to reverse work by researchers, including control over the infected machine name to prevent the bot from being run in a controlled environment.
Bot's settings can be saved or in the final part of the executable (EOF) of the bot and the configuration is "encrypted" using hard-coded key.
The feature that most of all I found interesting and innovative is that it can generate a "Lite" bot version which contains limited functionality: Download&Execute, to explore a web page and the "Uninstall" of BOT. The Lite version is generated by the builder as a .vbs file.
The .vbs has attractive features, with minor modifications can be blurred to be made completely FUD (Fully Undetectable), and then bypass the antivirus, can also be used in macros of the Office suite.
Call Home
DiamondFox is a HTTP Botnets and during the process of communicating with the C&C server User-Agent value is used as a "filter", without the correct value, the request is not processed by the server.
The data sent in a POST request are "encrypted" in the sources of the bot.
Regarding the upload of files stolen from the victim, files are processed by "post.php", and placed in the directory "logs/". The developer of the botnet forgot a small and insignificant detail: check for multiple extensions. This feature was partially fixed in the last updated of the C&C Panel of the botnet and It could load and execute files on the command and control server. (Gorynych/DiamondFox v4.2.0.257- File Upload Vulnerability · GitHub)
Save files from the web server by following this draft:
This botnet can be used to APT attacks and to amplify the tendency of "as a service" malware.
Thanks and sorry for mistakes
The technical analysis is explained here: A Study in Bots: DiamondFox but it is very difficult to understand for an average user, so I tried to simplify it, so that everyone can understand the complexity of this botnet and its dangers.
Botnet control panel.
Malware is written in VB6, It has many functions inside, one of the most interesting is the scraper of cards, a form of bots that search the infected computer's RAM, generally a Point of Sale System (POS), the credit card data (number and CVV).
DiamondFox has quite a few features, some of which are listed here:
- VM detection
- Detonation service detection
- Debugger detection
- Researcher detection
- Configurable install locations
- Configurable persistence locations
- Self-deletion
- Keystroke logging
- RAM scraping (credit card scraping)
- Password theft
- Spreading USB
- Dropbox spreading
- Disable TaskMgr/Regedit
- Plugin-based functionality
- Desktop screenshots
- DDoS
- Download&Execute: note that it is possible to execute directly in memory, without writing the downloaded file on disk and therefore reducing the risk of being detected by antivirus products.
- The stealing of the bitcoin wallet with the possibility to change the addresses with the bitcoin wallet of botmaster.
- The ability to transmit spam or malware through Facebook account &Twitter.
- Redirect websites, made by editing the Windows host file.
- Theft of credentials such as passwords, RDP, FTP, Instant Messaging and Mail stored on your system.
- The spreading of the bot via USB
The malware infects these paths:
Code:
APPDATA –% APPDATA%
TEMP –% TEMP%
PROGRAMFILES –% PROGRAMFILES%
–% WINDIR% WINDIRAnd the following options:
- HKCU (registry)
- Winlogon
- Startup Folder
For HKCU registry, the following key is generated:
Code:
HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run\ & BOTNAMEFor the Winlogon, the path to the application DiamondFox is added to the following locations:
Code:
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\currentversion\winlogon\Userinit
HKEY_LOCAL_MACHINE64\software\microsoft\windows\currentversion\winlogon\UserinitWith the "Startup" Folder, DiamondFox is simply copied to the user's startup, renamed WordPad.exe.
There are also anti-reversing features, to make it more difficult to reverse work by researchers, including control over the infected machine name to prevent the bot from being run in a controlled environment.
Bot's settings can be saved or in the final part of the executable (EOF) of the bot and the configuration is "encrypted" using hard-coded key.
The feature that most of all I found interesting and innovative is that it can generate a "Lite" bot version which contains limited functionality: Download&Execute, to explore a web page and the "Uninstall" of BOT. The Lite version is generated by the builder as a .vbs file.
The .vbs has attractive features, with minor modifications can be blurred to be made completely FUD (Fully Undetectable), and then bypass the antivirus, can also be used in macros of the Office suite.
Call Home
DiamondFox is a HTTP Botnets and during the process of communicating with the C&C server User-Agent value is used as a "filter", without the correct value, the request is not processed by the server.
The data sent in a POST request are "encrypted" in the sources of the bot.
Regarding the upload of files stolen from the victim, files are processed by "post.php", and placed in the directory "logs/". The developer of the botnet forgot a small and insignificant detail: check for multiple extensions. This feature was partially fixed in the last updated of the C&C Panel of the botnet and It could load and execute files on the command and control server. (Gorynych/DiamondFox v4.2.0.257- File Upload Vulnerability · GitHub)
Save files from the web server by following this draft:
Code:
logs/wallet
logs/scr
logs/rdp
logs/ftp
logs/mail
logs/pass
logs/kyl
logs/dumpsThis botnet can be used to APT attacks and to amplify the tendency of "as a service" malware.
Thanks and sorry for mistakes
Last edited by a moderator: