Earlier today, @Moonhorse posted a java malware which poses as a game.
Upon research, the real game was renamed from Ikov to Elkoy and the real website is elkoy.io.
Ikov is now used by attackers to distribute malware. The domain was registered on the 17th of March 2025. It may have remained dormant for quite some time, or it may have been compromised later. It is not known how long the domain has been pushing malware. The malware appears to have been compiled on the 20th of June 2025.
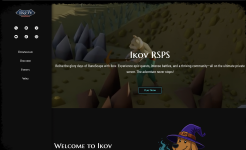
The website pushes a file named ikov.jar with the following hashes:
SHA256: 982e47f604b9b5cbb710f9d6bad16a3e44b0122c44dede726729b843ba357414
TLSH: T1DD06F223AE97C4B8DEA74CB351C68255942E957CAE0B91BE03D07DC84B60D4B8352FF9
Obfuscation is used on the 2 classes that reside within the java app.


RSPS.java
FileDownloader.java
Operational Flow
First, the malware takes care of its persistence.
It drops the following files:
Next, the malware proceeds to establishing several connections:
The Mitre ATT&CK Matrix is as follows:
Mitigations: Enable MFA for Discord. Use up-to-date antivirus software with web blocking and firewall capabilities. Do not download games from suspicious websites.
Upon research, the real game was renamed from Ikov to Elkoy and the real website is elkoy.io.
Ikov is now used by attackers to distribute malware. The domain was registered on the 17th of March 2025. It may have remained dormant for quite some time, or it may have been compromised later. It is not known how long the domain has been pushing malware. The malware appears to have been compiled on the 20th of June 2025.

The website pushes a file named ikov.jar with the following hashes:
SHA256: 982e47f604b9b5cbb710f9d6bad16a3e44b0122c44dede726729b843ba357414
TLSH: T1DD06F223AE97C4B8DEA74CB351C68255942E957CAE0B91BE03D07DC84B60D4B8352FF9
Obfuscation is used on the 2 classes that reside within the java app.
- Obfuscation is based on the following methods:
Symmetric Ciphers for Obfuscation (DES and Blowfish): To hide strings within the compiled code (like file paths and keywords), the malware uses standard symmetric block ciphers like DES and Blowfish. The decryption keys are hardcoded right next to the encrypted strings, making it a self-contained system. This works against static analysis. - Simple XOR Obfuscation: For some strings, it uses a simple XOR cipher. This isn't true encryption, but a basic obfuscation technique where each character of the string is mathematically XOR'd with a character from a key. It's fast, easy, and very effective at turning readable strings into gibberish in the compiled file.
- Additional BASE64 encoding serves as a final wrapper
RSPS.java
| Code Reference | Decrypted Plaintext | Purpose | |||
| lIIIlIIIIl[0] | \Discord\Local State | Path to Discord's state file containing the master key. | |||
| lIIIlIIIIl[1] | token | Keyword to search for within the database files. | |||
| lIIIlIIIIl[2], [5] | APPDATA | Windows environment variable for the AppData folder. | |||
| lIIIlIIIIl[3] | \Discord\Local Storage\leveldb | Path to Discord's token database. | |||
| lIIIlIIIIl[4] | " | A quote character used as a delimiter for parsing. | |||
| lIIIlIIIIl[6] | os_crypt | The top-level JSON object holding the encryption key. | |||
| lIIIlIIIIl[7] | encrypted_key | The specific JSON key for the encrypted master key. | |||
| lIIIlIIIIl[10] | AES/GCM/NoPadding | The cipher specification for decrypting the tokens. | |||
| lIIIlIIIIl[11] | AES | The encryption algorithm name. |
FileDownloader.java
| Code Reference | Decrypted Plaintext | Purpose | ||||
| WEBHOOK_URL, ZIP_WEBHOOK_URL | (Hardcoded Discord Webhook URLs) | C2 endpoints for exfiltrating the stolen screenshot, logs, and zipped files. | ||||
| FILE_URL | (Hardcoded File Download URL) | URL to download the malware itself, used for the persistence mechanism. | ||||
| lIIIlllllIIl[1] | \Microsoft\Windows\Start Menu\Programs\Startup\launch.jar | Full path for placing the malware to achieve persistence (run on login). | ||||
| lIIIlllllIIl[4] | #ERROR! | Header for the log file sent to the attacker. | ||||
| lIIIlllllIIl[29], [33] | (Hardcoded URL to malicious RuneLite settings file) | The malicious .properties file downloaded to hijack the RuneLite client. | ||||
| lIIIlllllIIl[38] | An unexpected error has occurred with a JNI library | Fake error message text shown to the user. | ||||
| lIIIlllllIIl[39] | JNI Error | Fake error message title. | ||||
| lIIIlllllIIl[49] | \.runelite\settings.properties | Path to the RuneLite settings file that is targeted. | ||||
| lIIIlllllIIl[62] | http://checkip.amazonaws.com | Service used to get the victim's public IP address. | ||||
| lIIIlllllIIl[118-123] | user.home, Desktop, Downloads, Documents, temp, hussla.zip | System properties and folder names used for finding files and creating the output zip. | ||||
| lIIIlllllIIl[155] | .txt | File extension the malware searches for on the Desktop and in Downloads. |
Operational Flow
First, the malware takes care of its persistence.
It drops the following files:
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\launch.jar - The path used to establish persistence.
- %USERPROFILE%\Documents\hussla.zip - The temporary archive created to stage stolen .txt files before exfiltration.
- %USERPROFILE%\AppData\Local\Temp\screenshot.png - The temporary file created for the desktop screenshot.
- \.runelite\settings.properties.bak[timestamp].tmp - The backup file created after hijacking the original RuneLite settings.
Next, the malware proceeds to establishing several connections:
- hxxps://discord[.]com/api/webhooks/[REDACTED] - Used for exfiltrating screenshots and system logs.
- hxxps://discord[.]com/api/webhooks/[REDACTED] - Used for exfiltrating the hussla.zip archive.
The Mitre ATT&CK Matrix is as follows:
| Tactic | Technique ID & Name | Description | |||||||
| Execution | T1204.002 - User Execution: Malicious File | Relies on the user running the malicious .jar file. | |||||||
| Persistence | T1547.001 - Boot or Logon Autostart Execution: Startup Folder | Copies itself to the Windows Startup folder to ensure it runs every time the user logs in. | |||||||
| Defense Evasion | T1027 - Obfuscated Files or Information | Employs multiple layers of string encryption (DES, Blowfish, XOR) to hide its capabilities from static analysis. | |||||||
| T1036.005 - Masquerading: Match Legitimate Name or Location | Displays a fake "JNI Error" message to appear as a legitimate but faulty Java application. | ||||||||
| Credential Access | T1555.003 - Credentials from Web Browsers | Uses techniques identical to browser credential theft to steal Discord tokens by decrypting the master key with Windows DPAPI. | |||||||
| T1552.001 - Credentials in Files | Collects all .txt files from the Desktop and Downloads folders, which may contain plaintext credentials. | ||||||||
| Discovery | T1083 - File and Directory Discovery | Scans for the .runelite folder and enumerates files in the Desktop and Downloads directories. | |||||||
| T1082 - System Information Discovery | Gathers the system hostname. | ||||||||
| Collection | T1113 - Screen Capture | Takes a screenshot of the victim's entire desktop. | |||||||
| T1560.001 - Archive Collected Data: Archive via Utility | Compresses all collected .txt files into a single hussla.zip archive for easier exfiltration. | ||||||||
| Command and Control | T1102.002 - Web Service | Uses Discord webhooks as its C2 infrastructure to receive stolen data. | |||||||
| Exfiltration | T1567.002 - Exfiltration Over Web Service: Exfiltration to Cloud Storage | Uploads the screenshot and zip archive to Discord's CDN via webhook POST requests. | |||||||
Mitigations: Enable MFA for Discord. Use up-to-date antivirus software with web blocking and firewall capabilities. Do not download games from suspicious websites.
Last edited:
